- Malware transforms Windows and macOS devices into proxy nodes.
- Compromised machines reroute traffic as covert proxy exit points.
- Malicious actors exploit infected systems for proxy requests.
- Windows and macOS devices were repurposed for unauthorized activities.
- AT&T Alien Labs reveals an alarming malware-driven proxy phenomenon.
The cybersecurity researchers at AT&T Alien Labs have shed light on an alarming phenomenon where malicious actors are harnessing malware-infected Windows and macOS machines as proxy exit nodes to reroute proxy requests.
These actors, utilizing a proxy server application, are covertly leveraging compromised systems to establish proxy exit nodes, enabling them to redirect proxy requests. It appears that these proxy exit nodes are not exclusively originating from users who have knowingly agreed to participate, as the proxy service’s website claims.
The attack vector involves delivering proxy servers through various malware strains that target unsuspecting users enticed by offers of cracked software and games. The proxy application, coded using the versatile Go programming language, ensures compatibility across multiple operating systems, including macOS and Windows.
One striking observation is the difference in the detection rates between macOS and Windows systems. While the Windows version of the proxy application effortlessly evades security measures due to its signed nature, the macOS variant is more easily detected.
According to AT&T’s blog post, Once executed on a compromised system, the malware discreetly installs the proxy application, sidestepping user interaction and simultaneously introducing additional malware or adware components. To achieve this covert process, the malware creators employ Inno Setup, a widely-used Windows installer. This tool enables the creation of packed executables, facilitating the proxy’s seamless installation and persistence within the system.
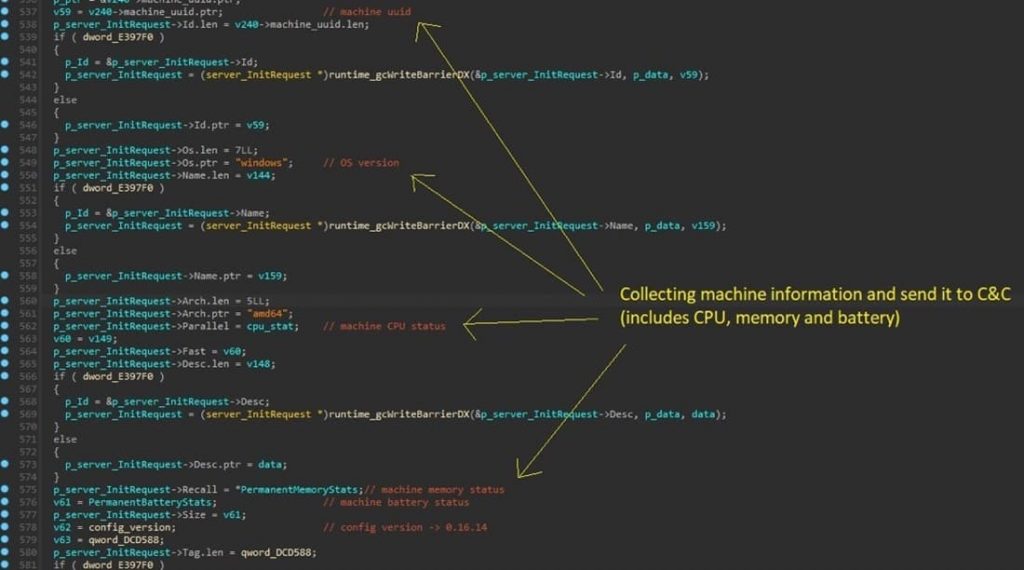
The nature of the malware-driven proxy server extends to its communication with the command and control server (C&C). The proxy application not only relays specific parameters to the C&C but also collects critical information about the compromised system, including processes, CPU and memory usage, and even battery status. This adaptive data collection ensures the proxy’s optimal performance and responsiveness while evading suspicion.
The monetization of malware-infused proxy servers through affiliate programs poses a significant challenge. The proxy application, packaged with Inno Setup, persists through multiple mechanisms, including registry keys and scheduled tasks, enabling the proxy to continually function as a covert channel for unauthorized financial gains.
The campaign’s disclosure builds upon previous findings by AT&T Alien Labs, in which macOS systems infected with AdLoad adware were repurposed as exit nodes for a vast residential proxy botnet.
This pattern potentially points to operators of AdLoad orchestrating a pay-per-install campaign. AdLoad, a notorious adware strain masquerading as legitimate applications, has been capitalizing on unsuspecting users to navigate them towards malicious websites, ultimately profiting from these schemes.
This evolving threat landscape is particularly concerning for macOS users, as the dark web has seen an exponential rise in the advertisement of information stealer strains and sophisticated tools aimed at bypassing macOS security mechanisms.
The past few years have witnessed an intensified focus on targeting macOS devices due to their growing prevalence in corporate environments, coupled with the high potential for earnings from malicious activities.