Unit 42 researchers discovered a new vulnerability in QNAP devices on 7 November 2023, which was confirmed by the vendor on 19 December 2023, and a security advisory was released subsequently to provide guidance and recommendations.
Palo Alto Networks Unit 42’s Advanced Threat Prevention (ATP) and telemetry systems identified a new zero-day vulnerability in QNAP QTS and QuTS hero firmware from the vendor QNAP. The vulnerability is tracked as CVE-2023-50358 and affects QNAP Network Attached Storage (NAS) devices.
For your information, QNAP, a company specializing in NAS devices, is known for its QNAP Turbo NAS System (QTS) operating system, which is often embedded in the firmware of QNAP NAS devices.
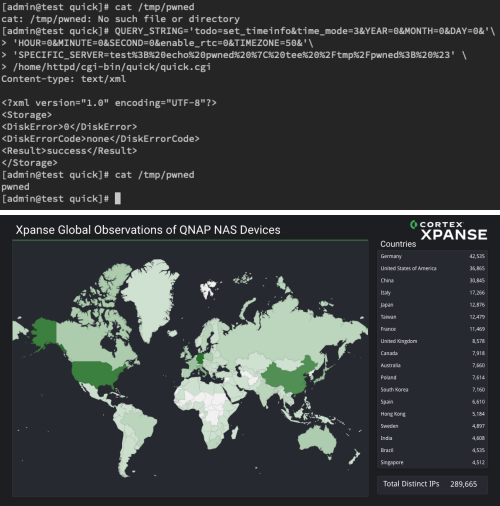
In its report published on 13 February 2024, authors Chao Lei, Jeff Luo, and Zhibin Zhang explained that CVE-2023-50358 is a command injection vulnerability found in the quick.cgi component of QNAP QTS firmware that is accessible without authentication. The vulnerability occurs when the HTTP request parameter todo=set_timeinfo is set, and the parameter SPECIFIC_SERVER is saved into a configuration file /tmp/quick/quick_tmp.conf with the entry name NTP Address.
The component then starts time synchronization using the ntpdate utility, and the command-line execution is ensured by reading the NTP Address in quick_tmp.conf and system(). Untrusted data from the SPECIFIC_SERVER parameter helps build a command line, which is executed in the shell, leading to arbitrary command execution.
It is worth noting that this vulnerability affects 289,665 separate IP addresses. The top five countries affected by the vulnerability are Germany, the United States, China, Italy, and Japan.
According to Unit 42 researchers threat actors constantly search for vulnerabilities in network-connected hosts, such as NAS devices because these can be exploited quickly. This is why ensuring foolproof security of these devices is necessary.
IoT devices are vulnerable to remote code execution vulnerabilities due to their low attack complexity and critical impact. To protect against these threats, QNAP recommends updating to the latest version of QTS or QuTScloud hero- QTS 5.1.5 or QuTS hero h5.1.5.
List of Affected Devices
- QTS 5.1.x
- QTS 5.0.1
- QTS 5.0.0
- QTS 4.5.x
- QTS 4.3.6
- QTS 4.3.4
- QTS 4.3.x
- QTS 4.2.x
- QuTS hero h5.1.x
- QuTS hero h5.0.1
- QuTS hero h5.0.0
- QuTS hero h4.x
QNAP has released a security advisory, advising affected organizations to follow mitigation instructions or apply firmware updates.
“Multiple vulnerabilities have been reported to affect several QNAP operating system versions. If exploited, the OS command injection vulnerabilities could allow users to execute commands via a network.”
In its advisory, the vendor noted fixing two vulnerabilities, CVE-2023-47218 and CVE-2023-50358 and explained how to implement the fixes.
“If you do not want to install a fully fixed version for your device, you can still mitigate the vulnerabilities by installing a partially fixed version. However, note that the vulnerabilities still exist during the installation process of a partially fixed version. The vulnerabilities only disappear after installation is complete.”
RELATED TOPICS
- CISA and Fortinet Warns of New FortiOS Zero-Day Flaws
- Ivanti VPN Flaws Exploited by DSLog Backdoor and Crypto Miners
- Hackers Uncover Airbus EFB App Vulnerability, Risking Aircraft Data
- Ethical Hackers Reported 835 Vulnerabilities, Earned $450K in 2023
- Smart Helmets Flaw Exposed Millions to Risk of Hacking and Surveillance
