Researcher Aaron Spangler identified a bug in Internet Explorer back in 1997. This flaw allowed stealing of user credentials through Windows Server Message Block protocol.
Now, after almost eighteen years, Cylance Wallace, a senior researcher at SPEAR research team, discovered a larger vulnerability while testing a messaging app keeping that particular bug in mind.
This newly identified vulnerability threatens around 31 applications including iTunes, Adobe Reader, Symantec SYMC-5.59% Norton Security Scan and Box on all versions of Windows.
Must Read: Microsoft fixes security flaw in Windows that existed for 19 years
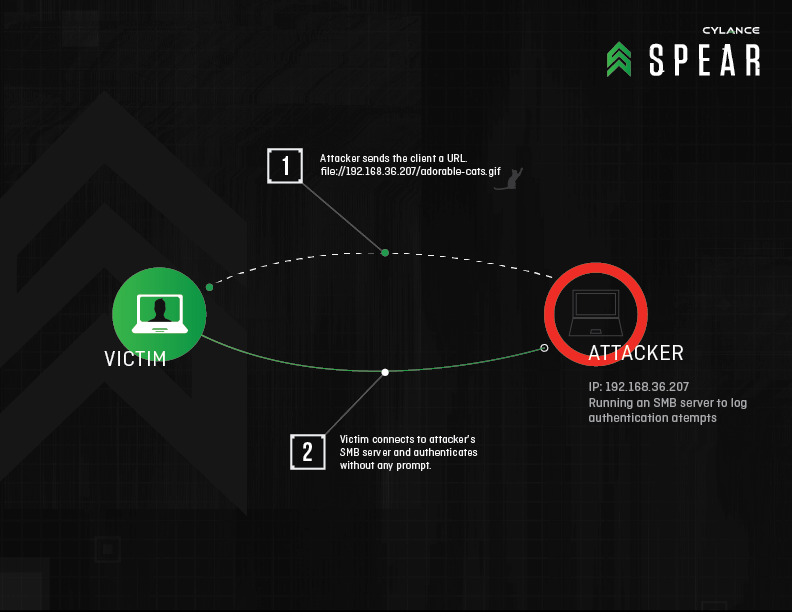
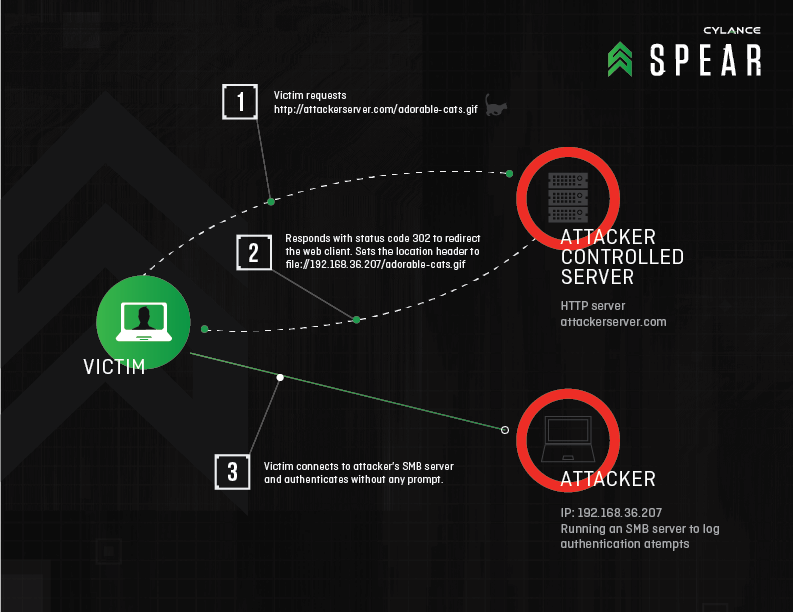
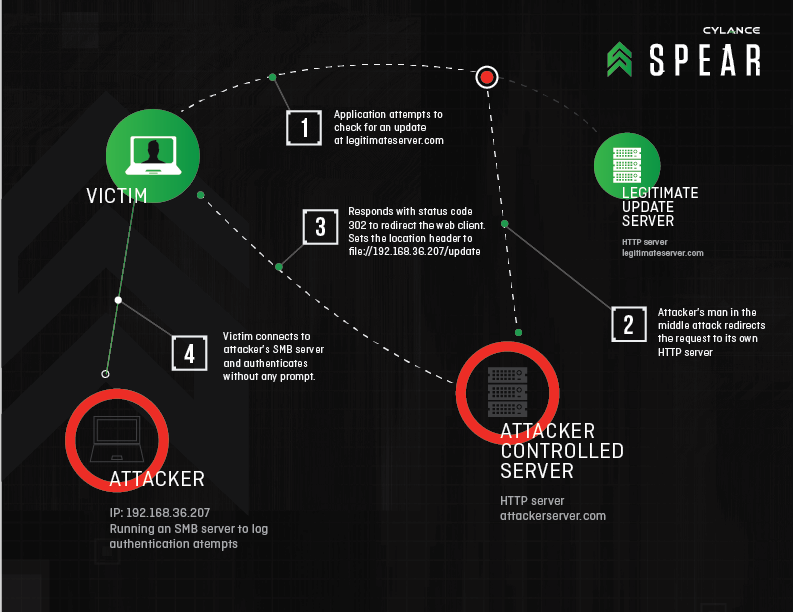
“Redirect to SMB” is the name given to this new vulnerability. It lets user login credentials to be exposed from numerous Windows applications by deceiving the apps into authenticating data via a rogue server. Redirect to SMB also lets attackers execute a man-in-the-middle attack on any device of Windows and allows sending communications to a mischievous SMB server and this allows the creation of the username and encrypted password of the user. Moreover, hackers can decrypt the password to access a variety of other vulnerable applications.
This vulnerability, says Cylance, is a “forever-day” phenomenon because the original bug has continued to remain a threat since 1997. Spangler’s bug was just restricted to Internet Explorer whereas the Redirect to SMB affects a variety of other applications across all versions of Windows.
So, what this means for Windows users? Let’s imagine that a person is in a coffee shop surfing the web on a Windows laptop using unsecured, free public WiFi is actually exposing his device and credentials to hackers who on the other hand can easily launch a man-in-the-middle attack to access the device since it is easy to obtain user credentials from a number of applications. For instance, when iTunes is accessed for an upgrade or scan has been run through Symantec Norton anti-virus, the attacker will be able to access user’s credentials. If a user has synced files from their laptop to Box, the Box login info will be easily transferred to the hacker. Most significant concern is regarding the possibility of corporate files being exposed.
According to Wallace, he identified this vulnerability when he looked into the messaging app that the team was testing and then expanded research to other applications. Wallace described, “At first, I was happy I was able to discover an issue with the chat messenger. It was a mixed feeling of excitement and fear. That feeling built over time to the disclosure,” according to Forbes.
When he realized the wide scope of “Redirect to SMB” his team decided to reveal it to Carnegie Mellon University CERT, which then worked with all the vulnerable applications to patch it before making the threat public. Wallace urges that the security community will collaborate to identify more such applications that need to be patched.
The 31 applications that Cylance discovered to be vulnerable include the following:
Adobe Reader, Apple QuickTime, Apple Software Update (that manages iTunes updates), Internet Explorer, Windows Media Player, Excel 2010, Symantec’s Norton Security Scan, AVG Free, BitDefender
Free, Comodo Antivirus, NET Reflector, Maltego CE, Box Sync, TeamViewer, Github for Windows, PyCharm, IntelliJ IDEA, PHP Storm, and JDK 8u31’s installer.
Attacking AVG via ARP Poisoning:
Source: Cylance