What happened to the LockBit Ransomware Gang? Has the group been disrupted? Have any arrests been made? Learn all about the breaking development regarding one of the most notorious ransomware gangs possibly facing law enforcement scrutiny.
Law enforcement authorities have seized the official and all known dark web websites of the LockBit ransomware gang as part of “Operation Cronos.” The latest development appears to have occurred earlier today, although there has been no confirmation or press release issued by authorities at this time.
However, as observed by Hackread.com, .Onion domains owned by the group now display a seizure notice announcing its takeover by the United Kingdom’s National Cyber Crime Agency in cooperation with the US Department of Justice, the FBI, Europol, and other entities.
“Operation Cronos – Come Back Tomorrow”
It’s important to note that the notice itself contains details about the incident. Authorities have revealed that this is an ongoing and developing operation conducted under the banner of “Operation Cronos.”
Does this suggest that more ransomware gangs will face the wrath of law enforcement agencies? Have arrests been made, and has electronic and monetary infrastructure been seized? For answers, we must wait until tomorrow, as authorities have urged visitors to visit seized LockBit domains at 11:30 GMT on Tuesday, February 20th, for more information about the operation.
This site is now under the control of Law Enforcement – This site is now under the control of The National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, “Operation Cronos.”
We can confirm that LockBit’s services have been disrupted as a result of International Law Enforcement action – this is an ongoing and developing operation. Return here for more information at: 11:30 GMT on Tuesday 20th Feb.
National Crime Agency (NCA)

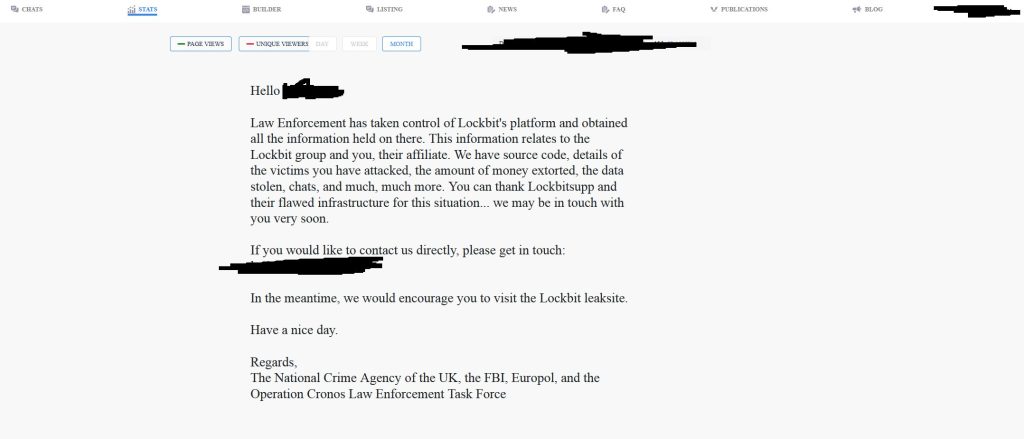
Additionally, LockBit affiliates attempting to log into the affiliate panel have also encountered a surprising message, providing a glimpse of what has been accessed and seized by authorities.
Here is the list of all dark web domains that display seizure notice:
- lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd.onion/
- lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead.onion/
- lockbitapt2yfbt7lchxejug47kmqvqqxvvjpqkmevv4l3azl3gy6pyd.onion/
- lockbitapt34kvrip6xojylohhxrwsvpzdffgs5z4pbbsywnzsbdguqd.onion/
- lockbitapt5x4zkjbcqmz6frdhecqqgadevyiwqxukksspnlidyvd7qd.onion/
- lockbitapt72iw55njgnqpymggskg5yp75ry7rirtdg4m7i42artsbqd.onion/
- lockbitaptawjl6udhpd323uehekiyatj6ftcxmkwe5sezs4fqgpjpid.onion/
- lockbitaptbdiajqtplcrigzgdjprwugkkut63nbvy2d5r4w2agyekqd.onion/
It is worth noting that the exact origin of the group is unknown, but the US government believes the cybercrime syndicate operates from Russia. In June 2023, Ruslan Magomedovich Astamirov (20), a Russian national, was arrested and charged with conspiring to commit LockBit ransomware attacks against U.S. and foreign businesses.
Is this the end of the LockBit ransomware gang?
Probably not. While we await official confirmation from law enforcement agencies, it’s quite likely that no arrests have been made, allowing the group to potentially continue operating under its existing guise or rebrand itself with a new identity. Furthermore, it remains unclear if authorities have successfully seized the group’s cryptocurrency wallets, which likely contain significant sums gained from ransomware payments.
Some Known and Alleged Victims
LockBit ransomware emerged as a significant threat, targeting both large and mid-sized organizations across various sectors, including healthcare, education, government, and critical infrastructure. Some of the group’s notable claimed targets included the following:
- Boeing (A)
- Subway
- Accenture
- Royal Mail
- Bangkok Airways
- PayBito crypto exchange
- Darktrace Cybersecurity Firm
- SpaceX Contractor Maximum Industries
The group utilizes multiple techniques to infiltrate victim networks, such as phishing emails, exploiting vulnerabilities, and purchasing stolen credentials on the dark web. Once inside, LockBit encrypts critical data, making it inaccessible to the victim, and demands a ransom payment in exchange for a decryption tool. If the ransom is not paid, they threaten to leak stolen data online through their dark web portal.
LockBit has released several versions of their ransomware, notably LockBit 2.0 and LockBit 3.0. The impact of LockBit attacks extends beyond financial losses, including disruption to operations, data recovery costs, reputational damage, and privacy concerns due to data leaks, which expose sensitive information and pose risks such as identity theft and fraud.
For insights into this, we reached out to William Wright, CEO of Closed Door Security, who sees no surprise in the event due to the extent of LockBit’s targets over the years.”
“LockBit is the most prolific ransomware gang to ever have existed and it was responsible for devastating attacks on hundreds of businesses, including the Royal Mail, which cost the organisation millions to recover from, so it’s not surprising the UK’s NCA wanted to feature so heavily in this disruption.”
“It could be said that LockBit was largely responsible for the growth of the ransomware industry today,” William explained. “Its affiliates saw big financial returns from the attacks, which undoubtedly made ransomware the attack-of-choice for many criminals and drew others to the industry.”
William also warned of LockBit’s potential return, which could be more aggressive than before. Therefore, companies must exercise precautions. “The attackers could resurface under new branding as we have seen with DarkSide to BlackMatter to BlackCat, and many others. Enterprises must therefore continue to protect their networks against ransomware. While law enforcement is making good progress, the battle is not over yet.”
This is a developing story, with official confirmation from law enforcement authorities pending. We will continue to monitor the situation closely and update this article accordingly.
