The pro-Ukraine groups thought they were fighting back against Russia with a new DDoS app, but it turns out the app itself is malware that has been infecting their devices, Google has confirmed.
Google Threat Analysis Group (TAG) has published its findings on the activities of an Advanced Persistent Threat (APT) group Turla, aka Venomous Bear, Krypton, Uroburos, and Waterbug, against Ukrainian targets.
This APT group is affiliated with the Federal Security Service, Russia, and according to TAG security engineer Billy Leonard, it is deploying Android malware disguised as a DDoS attack tool.
It is worth noting that Turla is the same group that was found to control malware via Instagram posts of the popular American singer and dancer Britney Spears back in June 2017.
Ukrainians Trapped with Fake DDoS Tools
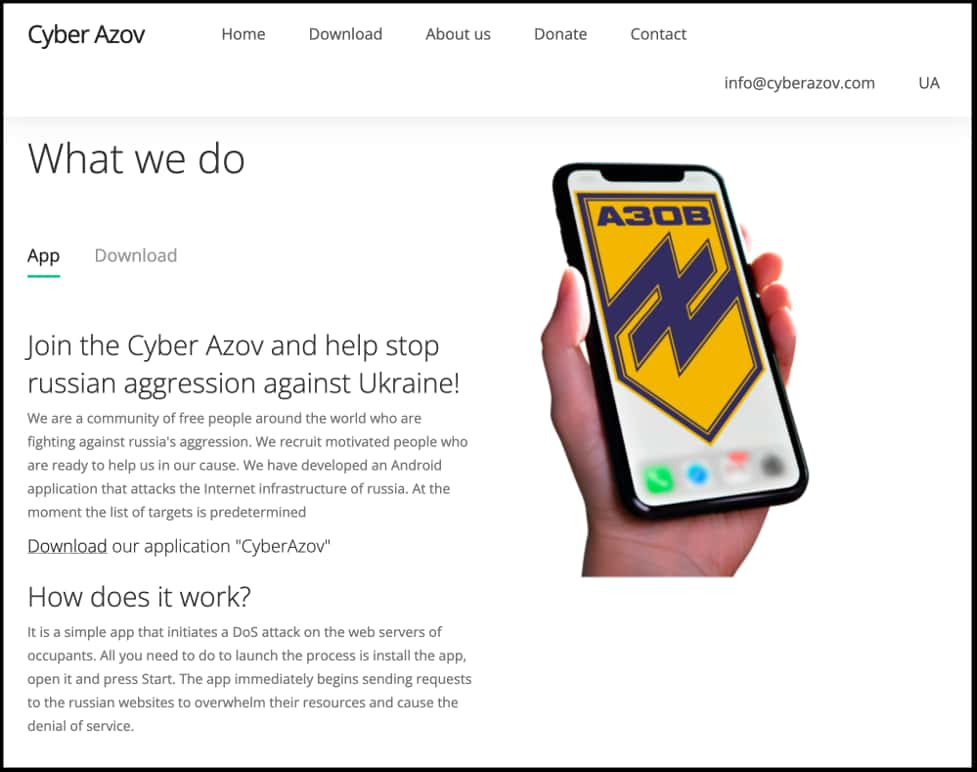
As per Google Tag’s report, Turla’s fake DDoS app is hosted on a spoofed version of the Ukrainian Azov Regiment (the country’s far-right inventory unit) identified as cyberazovcom.
Leonard explained that this is the first time they have seen Turla distributing Android malware. The fake apps weren’t delivered via the Google Play Store but on the spoofed domain, which the attackers controlled. They also used third-party messaging services to promote the domain.
However, according to Lab52, this is not the first time the Turla APT group has been caught spreading Android malware. In its report published in April 2022, the company stated that the Turla group has been distributing Android malware capable of tracking GPS location and spying on victims.
At the moment, Turla is focusing on targeting pro-Ukrainian activists, primarily those who enlisted to volunteer for the IT army to launch DDoS attacks against Russian IT infrastructure.
Scam Details
According to Google TAG’s blog post, the malicious Cyber Azov app is being distributed among Pro-Ukrainian activists and organizations to launch DDoS attacks against Russian sites from their smartphones quickly.
“The app is distributed under the guise of performing Denial of Service (DoS) attacks against a set of Russian websites. However, the ‘DoS’ consists only of a single GET request to the target website, not enough to be effective.”
Billy Leonard – Google TAG
The final malicious payload is unclear, and Leonard noted that the number of installs is also relatively low. The fake app was detected in March 2022, after which TAG security researchers warned Ukrainian activities to remain cautious while downloading DDoS tools from unverified platforms.
In conclusion, be very careful about who you trust online. Russian hackers are highly sophisticated not only in developing and malware but in social engineering aimed at targeting their victims.
More Related Hackers News
- Ukraine Thwart Russian Industroyer 2 Malware Attack on Energy Provider
- Feds Dismantle Russian Rsocks Botnet Powered by Millions of IoT Devices
- Russia Hackers Abusing BRc4 Red Team Penetration Tool in Recent Attacks
- Russia’s Yandex hit by largest DDoS attack involving 200,000 hacked devices
- Google takes down sites with ties to hack-for-hire groups in UAE, Russia, India
