Currently, over 30 sites have been marked as malicious by Google’s Safe Browsing feature.
Google TAG (Threat Analysis Group) has blocked dozens of malicious websites and domains used by hack-for-hire groups. These groups are different from commercial surveillance tools providers because where the latter only provides tools to conduct cybercrimes, hack-for-hire groups are involved in the attacks directly.
Moreover, companies offering such services may also employ these groups. But, usually, they provide services as freelancers. These groups target organizations and individuals in corporate espionage and data-stealing campaigns. Human rights and political activists, journalists, and politicians are some of their prime targets.
TAG director Shane Huntley stated there’s no definite delineation of hack-for-hire groups’ targets and missions.
Hackers Targeting High-Risk Entities
According to TAG’s analysts, hack-for-hire groups attacked high-risk targets across the globe. Although many such groups have been detected over the past few years, in this particular instance, Google has focused on three hack-for-hire gangs operating in the following countries:
- India
- Russia
- United Arab Emirates
In their blog post published Thursday, Google’s researchers explained that while the domains were blocked, over thirty domains were also added to Google’s Safe Browsing system, so users can no longer access them.
Details of Hack-for-Hire Groups
India: The India-based threat actors have been under Google’s radar since 2012. Some of its members were supposedly linked to offensive security providers Belltrox and Appin. Currently, they work for a new espionage services provider firm Rebsec, revealed TAG.
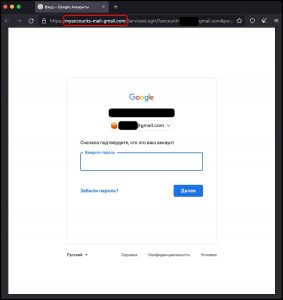
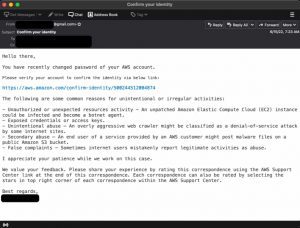
This group usually targets healthcare, telecom, and government organizations in the Middle East. Their attacks involve phishing credentials for Gmail and AWS (Amazon Web Services) and government service accounts.
Russia: The Russia-based group is tracked as Void Balaur. This group primarily targets politicians, journalists, non-profit organizations, and NGOs. It also targets citizens in Russia and nearby countries. This group’s main attack vector is phishing campaigns, and at one point, it had a public website where it promoted its email and social media accounts hacking services.
UAE: The threat actor linked with the UAE targets entities across the Middle East and North Africa. Its main targets include educational, government, and political organizations. Like other groups, this one also relies on phishing email scams, but what makes this group different is that it also uses a custom phishing kit.
According to Google researchers, an individual, Mohammed Benabdella, whom Microsoft sued in 2014 for developing H-Worm or njRAT malware, is associated with this group.
Huntley has shared the list of domains Google has blocked (available below) and also tracking many other state-backed threat actors, including surveillance vendors for selling spyware to governments and running financially motivated campaigns worldwide.
aplonl
myproject-loginshop
mysite-logshop
supp-helpme
account-noreply3xyz
goolgeltd
goolgehelp
account-noreply8info
account-serverxyz
kcynvd-mailcom
mail-goolgecom
kcynve-mailcom
dtiwa.applink
share-team.applink
mipim.applink
processs.applink
aws-amazon.appink
cliksbs
loadingsbs
userprofilelive
requestservicelive
unt-logcom
webtech-portalcom
id-aplinfo
rnanage-icloudcom
go-glio
login-my-oauth-mailru
oauth-login-accounts-mailru
my-oauth-accounts-mailru
login-cloud-myaccount-mailru
myaccounts-authru
security-my-accountru
source-place-preferenceru
safe-place-smartlinkru
safe-place-experienceru
preference-community-placeru
This is the second major event reported by Google. Just last week, the IT security researchers at the tech giant’s Threat Analysis Group exposed an ongoing campaign in which local ISPs (Internet service providers) in Italy and Kazakhstan were caught installing malware on the smartphones of their customers.
