KEY FINDINGS
- Check Point Research shared details of a newly discovered BBTok banking trojan variant.
- This malicious variant can spoof the interfaces of over 40 Banks in Brazil and Mexico.
- The malware operator aims to compromise PCs and steal bank card numbers or 2FA authentication codes.
- Phishing emails serve as the primary lure in this campaign, where attackers have used sophisticated techniques to make them believable and relied on multiple file types, including ISO, ZIP, LNK, DOCX, JS and XLL, to distribute BBTok.
- The campaign is still active, targeting Brazilian and Mexican users through multi-layered geo-fencing.
BBTok malware, first detected in 2020, has resurfaced in a brand-new, far more sinister avatar mainly targeting users in Latin America, reported Check Point Research’s cybersecurity researchers in their latest blog post published on 20 September 2020.
Researchers claim that since 2020, they have observed significant improvement in the TTPs (techniques, tactics, and procedures) adopted by BBTok malware operators as they have added multiple obfuscation layers and downloaders. This helps them avoid detection.
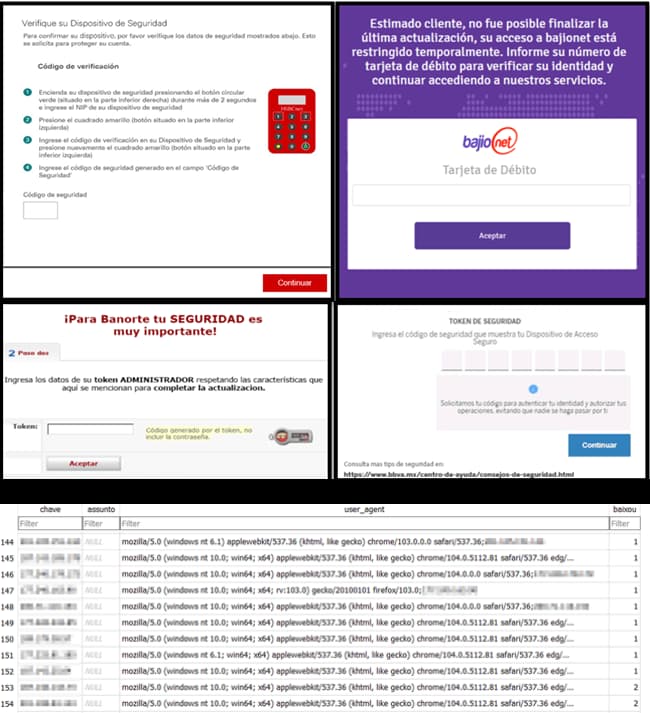
For your information, BBTok malware is a banking malware. Its new variant replicates the interfaces of over 40 banks, all located in Mexico and Brazil. The campaign involves a unique infection chain with a combination of LOLBins (living off the land binaries). Hundreds of users have been targeted so far in this active campaign.
This is a financially motivated campaign where attackers send phishing emails to unsuspecting users in Brazil and Mexico to lure them into entering the two-factor authentication codes of their bank accounts or giving away payment card numbers.
A malicious link in that email contains a .LNK file that initiates the infection chain, deploys the malware, and launches a decoy document. Further probing revealed that attackers maintain diverse infection chains for different Windows OS versions.
These chains use many file types to deploy malware, including ISO, ZIP, LNK, DOCX, JS and XLL. A rare feature of this attack is that a custom server-side application generates unique payloads for every victim after identifying their location and OS.
BBTok malware allows its operators to execute remote commands and inhabits almost all signature banking trojan capabilities, apart from replicating the interfaces of Latin American banks. Some of the banks it targets include Citibank, Scotiabank, Banco Itaú and HSBC.
These fake interfaces are designed so cleverly that victims cannot detect foul play and willingly enter their security codes or token numbers for 2FA, after which it is quite easy for attackers to hijack their bank accounts. Sometimes, the victims may be lured to enter payment card data.
Regarding this new threat, Check Point’s threat intelligence group manager, Sergey Shykevich, stated that banking malware remains a significant issue of concern in Latin America because its primary objective is to steal the victim’s financial details.
“While worldwide we see a consistent trend of multipurpose malware which is able to do a variety of different activities (stealing data and credentials, pushing ransomware, etc.), in Latin America we still see a dominance of banking malware which only goal is to steal victims’ financial information.”
“Cyberattacks have increased 8% this year and show no signs of slowing down. We urge everyone to stay vigilant and be wary of suspicious emails with attached files and pay extra attention to where they enter their banking credentials and payment card information,” Shykevich noted.
BBTok banking malware is a product of fileless attacks that took place in Latin America back in 2020 and features a broad range of functionalities, including killing/enumerating processes, clipboard content manipulation, keyboard/mouse control, and trademark banking malware features such as simulating fake login interfaces.
It has continually been evolving, making it essential to adopt necessary security practices to avoid becoming victims of phishing attacks. Ignore password resetting emails if you cannot recall any attempts to change passwords, note the email’s content and sender before opening, and avoid sharing credentials on any platform without verifying the web address.
