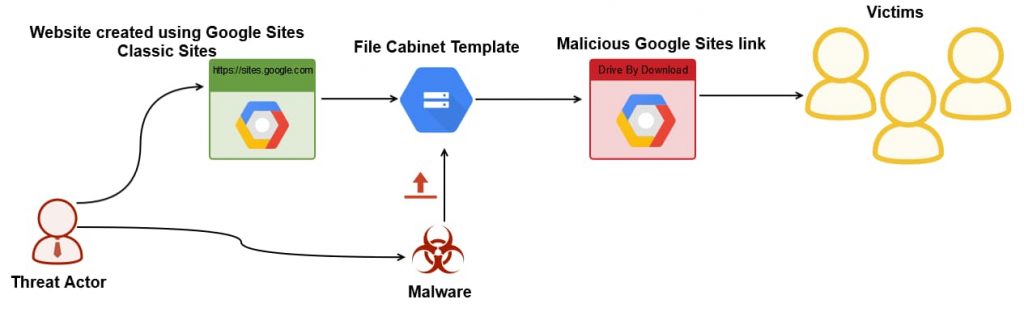
The IT security researchers at Netskope Threat Research Labs have discovered a new malware hosted on the Google Sites, a dedicated platform offered by Google for developing websites.
Dubbed LoadPCBanker by researchers; the malware is actually an executable that is hidden inside a PDF file titled “PDF Reservations Details MANOEL CARVALHO hospedagem familiar detalhes PDF.exe.”
See: GoogleUserContent CDN Hosting Images Infected with Malware
The name shows that hackers are specifically targeting English and Portuguese speakers (in Brazil). This file is a dropper that has been tasked with stealing information and transferring the data to an MYSQL server, which is directly controlled by unknown hackers. Furthermore, the PDF file is designed to be holding guest house reservation information while it is stored in the Google Sites File Cabinet storage space.
The malware has been named LoadPCBanker because of the way that it is deployed. According to researchers, the attack was discovered because of its interesting delivery method since unlike other Google services such as Gmail that block malicious file uploads, Google File Cabinet doesn’t showcase such limitations.
What’s notable about this attack is that, while other Google services such as Gmail have protections in place to block malicious file uploads like this, Google File Cabinet does not, wrote Netskope’s Ashwin Vamshi in a blog post.
It is basically a legacy platform where simple websites can be built but the File Cabinet is a separate functionality used for uploading files that are later hosted on the website. This particular functionality is being exploited by cybercriminals this time around to launch LoadPCBlocker.
Hackers use File Cabinet for distributing malware by uploading it to websites and sending out links of the malicious websites to unsuspecting users through phishing emails. When the recipients click on the links that are displayed as Google URLs, they are redirected to the attacker’s websites where the malicious executable is disguised as a PDF file in the form of hotel or guest house reservation information.
Perhaps, cybercriminals are now eyeing to exploit the positive brand image and reputation that Google enjoys around the world. As noted by Ashwin Vamshi of Netskope, users are “more likely to fall victim to an attack launched from within a Google service.”
Netskope researchers further revealed that the users are most likely to click on Google links instead of an attachment since they now know the consequences of opening suspicious attachments. There are several attack stages of LoadPCBanker malware.
See: Hackers abusing Google App Engine to spread PDF malware
The first stage is where the parent downloader is launched to allow transferring of the next-stage payloads from a file hosting website to the victim’s device. These payloads are responsible for collecting clipboard data, screenshots, and record keystrokes. The data is then transferred to the MYSQL server of the attacker.
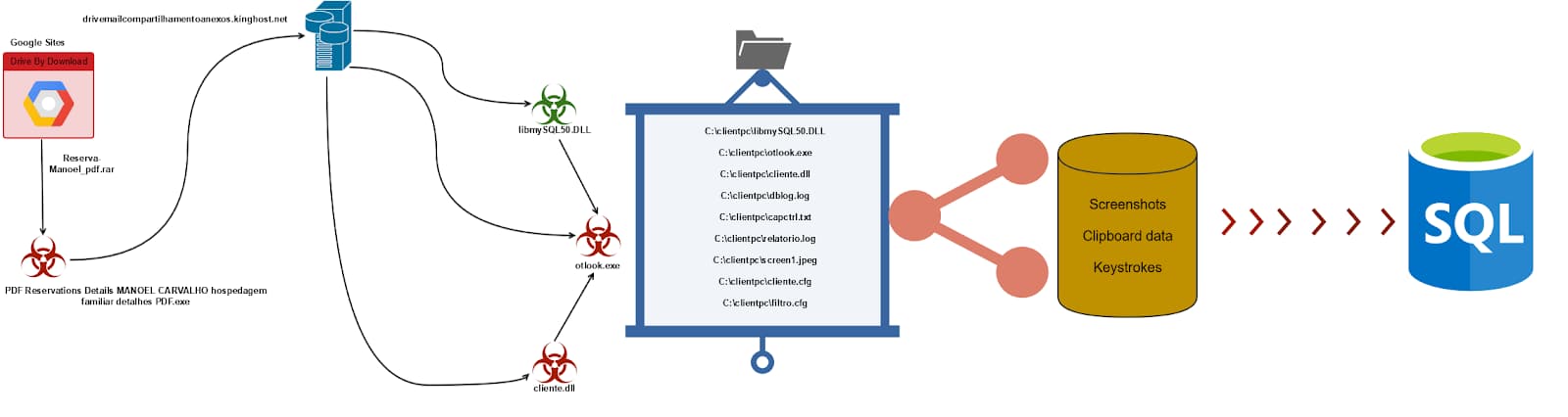
According to researchers, this mechanism doesn’t show the attacker’s sophistication but shows that cybercriminals are trying to exfiltrate information by blending in with the standard SQL traffic to evade detection. It is worth noting that security researchers identified a similar malware in 2014 and this time around it has been launched again with some major upgrading in its functionality.
It is not yet clear whether the same attacker is behind the new wave of attacks or the malware code was shared with someone else.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.