KEY FINDINGS
- Chae$4 is a new and advanced malware variant that targets customers of financial and logistics companies in Latin America.
- The malware is difficult to detect because it uses sophisticated encryption techniques and stealth mechanisms.
- Chae$4 can steal login credentials, financial data, and other sensitive information.
- The malware is spread through malicious MSI installers, often disguised as legitimate application installers.
Morphisec, a leading cybersecurity firm, has discovered a new and advanced variant of the Chaes malware targeting customers of financial and logistics companies in Latin America. This article delves into the mechanics of this evolved malware, dubbed Chae$4 as well as its implications, and strategies for businesses to safeguard against it.
The Chaes malware first emerged in November 2020 primarily targeting e-commerce customers in Latin America, particularly Brazil. The malware had been active since at least mid-2020, making its presence known by targeting unsuspecting victims.
The latest variant, Chae$4, marks a significant evolution in its capabilities. Chae$4 malware features a more sophisticated code structure advanced encryption techniques and stealth mechanisms, making it even harder to detect.
According to a report shared by Morphisec to Hackread.com, Chae$4 malware predominantly uses Python, employing decryption and dynamic in-memory execution, therefore evading traditional defence systems. The malware has abandoned Puppeteer in favour of a bespoke approach to monitor and intercept Chromium browsers’ activities.
Chae$4 targets a broader range of services, including prominent platforms and banks such as Mercado Libre, Mercado Pago, WhatsApp Web, Itau Bank, Caixa Bank, and even MetaMask.
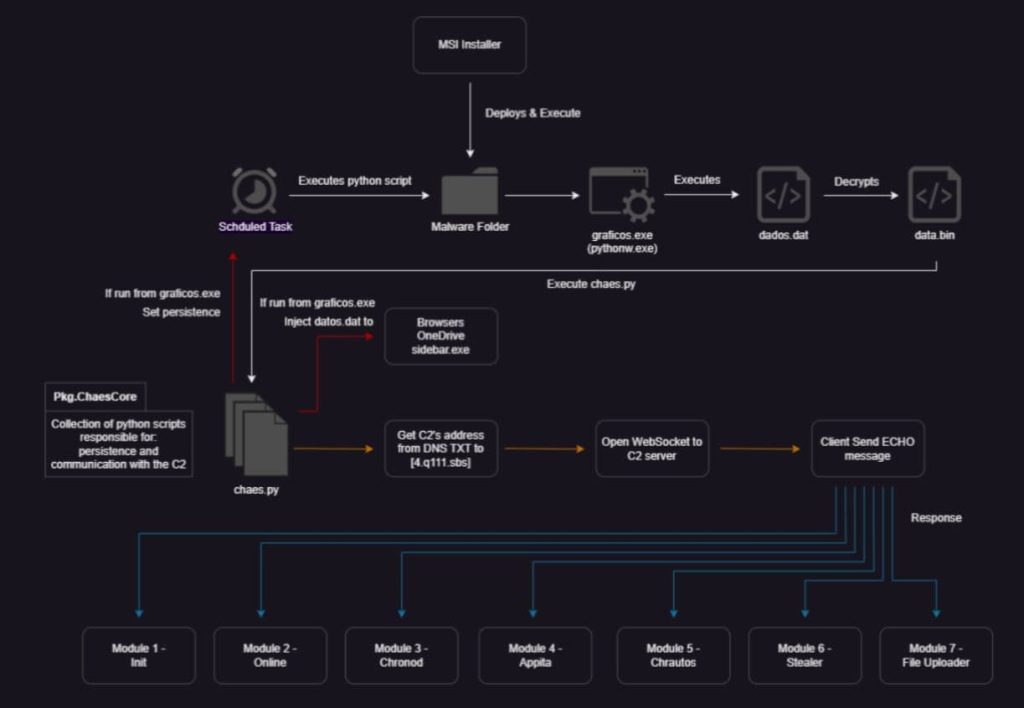
The new variant employs WebSockets for primary communication between its modules and the Command and Control (C2) server. In addition to this, Chae$4 uses a Domain Generation Algorithm (DGA) for the dynamic resolution of the C2 server’s address.
The Chae$4 malware comprises several modules, each serving a specific purpose. These modules include:
- Init Module: This module initiates communication with the attacker, gathering extensive data about the infected system.
- Online Module: It functions as a beacon, informing the attacker of the infected system’s activity status.
- Chronod Module: Responsible for stealing credentials, this module targets browser activities, including login data and financial information including BTC, ETH and PIX transfers.
- Appita Module: Similar to the Chronod module, this one specifically focuses on targeting Itau Bank’s application.
- Chrautos Module: An advanced version of Chronod and Appita modules, it offers better code architecture and enhanced capabilities.
- Stealer Module: This module specializes in stealing data from Chromium-based browsers, including login data, credit card details, cookies, and autofill information.
- File Upload Module: This recent addition allows the malware to search for and upload specific files, such as those related to the MetaMask’s Chrome extension.
The infection typically starts with the execution of a malicious MSI installer, often disguised as a legitimate application installer. The malware then deploys and downloads necessary files to establish persistence on the infected system.
The core component, ChaesCore, is responsible for setting up persistence and migrating into legitimate processes. Once initialized, ChaesCore communicates with the C2 server and downloads additional modules as required. Communication is encrypted to hide its activities.
The MSI installer contains obfuscated JavaScript and PowerShell scripts that establish the malware’s working directory and downloads essential files. The Module Wrapper decrypts and dynamically loads modules, executing their malicious code.
Different modules focus on stealing various types of data, such as login credentials, personal information, and financial data.
Chae$4 malware is a serious threat, but by taking steps to protect yourself, you can help to keep your data safe. In addition to the information above, here are some other things to keep in mind about Chae$4:
- The malware is still under development, so new features or capabilities may be added in the future.
- The malware is targeted at a specific region, but it is possible that it could be used to target other regions in the future.
- The malware is constantly evolving, so it is important to stay up-to-date on the latest information about it.