The whistleblowing site WikiLeaks is back with yet another Vault 7 series related document. This one is called “Cherry Blossom” program which gives a glance at the wireless hacking capabilities of The Central Intelligence Agency (CIA).
The Cherry Blossom project according to the leaked documents was allegedly developed and implemented by the CIA with the help of a nonprofit research institute headquartered in Menlo Park, California for its project “Cherry Bomb.”
RELEASE: CIA ‘CherryBlossom’ & ‘CherryBomb’ have been infecting #DLink, #Belkin & #Linksys WiFi routers for years https://t.co/uCQLaaRwrO pic.twitter.com/gEfD84RKlX
— WikiLeaks (@wikileaks) June 15, 2017
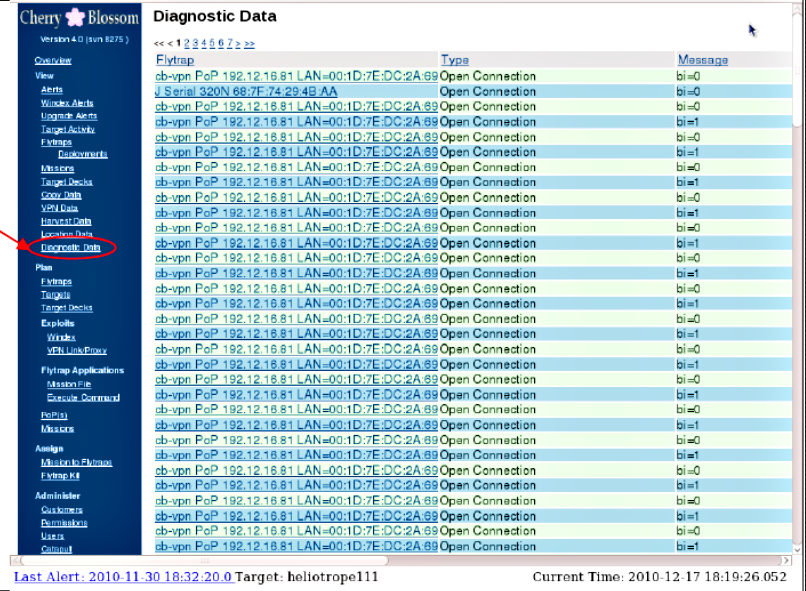
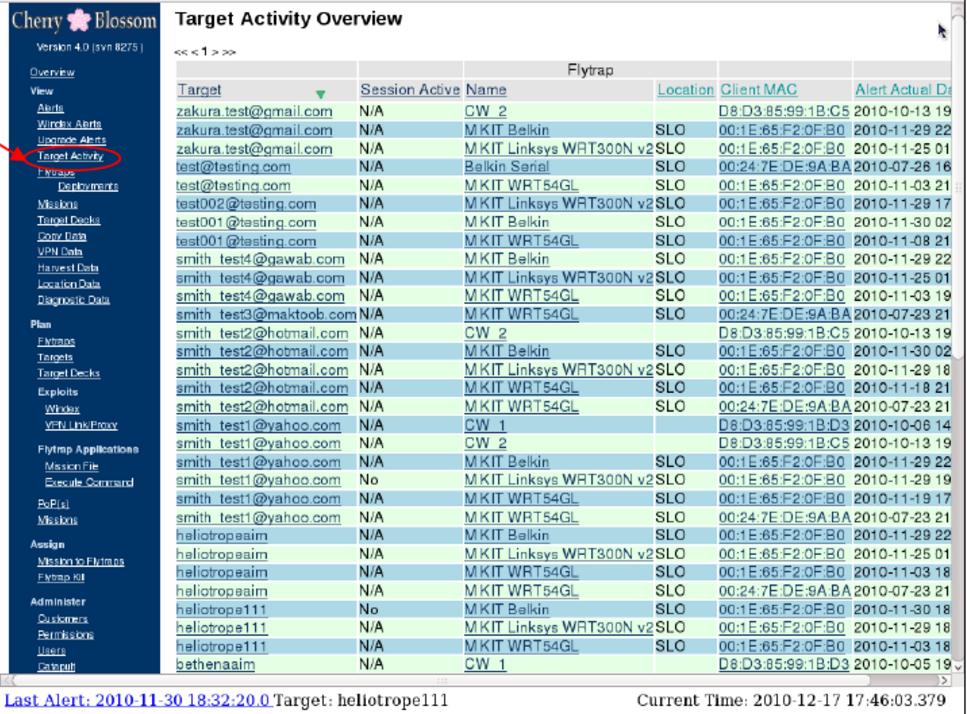
Cherry Blossom itself is a firmware allowing the attackers to exploit vulnerabilities and compromise wireless networking devices such as access points (APs) and wireless routers. Upon compromising the targeted device remotely, Cherry Blossom replaces the existing firmware with its own allowing the attackers to turn the router or access point into a so-called ‘FlyTrap’. The FlyTrap can scan for “email addresses, chat usernames, MAC addresses and VoIP numbers” in passing network traffic – All that without any physical access.
According to the Wikileaks press release:
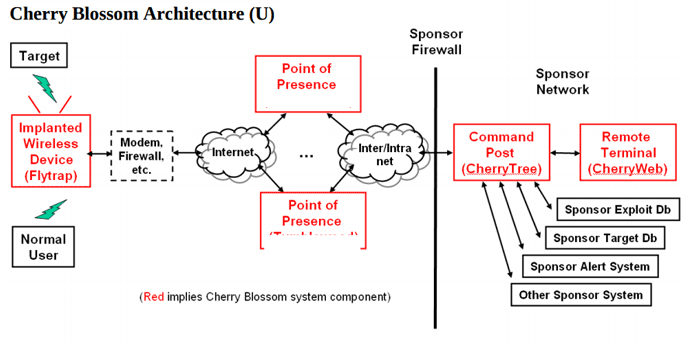
Once the new firmware on the device is flashed, the router or access point will become a so-called FlyTrap. A FlyTrap will beacon over the Internet to a Command & Control server referred to as the CherryTree. The beaconed information contains device status and security information that the CherryTree logs to a database. In response to this information, the CherryTree sends a Mission with operator-defined tasking. An operator can use CherryWeb, a browser-based user interface to view Flytrap status and security info, plan Mission tasking, view Mission-related data, and perform system administration tasks.
Furthermore, WikiLeaks notes that because WiFi devices are common in homes, public places and offices it makes them fitting target to conduct ‘Man-In-The-Middle’ attacks as Cherry Blossom program can easily monitor, control and manipulate the Internet traffic of connected users.
Some of the devices which can be exploited by Cherry Blossom for vulnerabilities include 3Com, Aironet/Cisco, Allied Telesis, Ambit, Apple, Asustek Co, Belkin, Breezecom, Cameo, D-Link, Gemtek, Linksys, Orinoco, USRobotics, and Z-Com. The full list of hundreds of other vendors is available here .
So far, the Vault 7 series has shown how CIA allegedly hacks TVs, smartphones, trucks and computers. The series also highlights the critical vulnerabilities which the intelligence community discovers in operating systems like Windows and Mac OS but never shares with the manufacturers.
The documents have also shown how the CIA uses malware and other software against unsuspecting users around the world. These include Dark Matter, Marble, Grasshopper, HIVE, Weeping Angel, Scribbles, Archimedes, AfterMidnight or Assassin, Athena and Pandemic.
