China’s surveillance against Uyghurs and Tibetans more persuasive than previously anticipated.
China for long has been persecuting Uyghurs Muslims on the pretext of countering extremist ideologies. Much of this has been reported in the mainstream media in the form of visibly seen concentration camps. However, another facet is also present which has been neglected if one views the lack of attention it has earned until now.
This respective front happens to be the cybersecurity world where China has been found to be using 4 Android surveillance tools since 2013 as a part of its APT campaigns according to a report by Lookout.
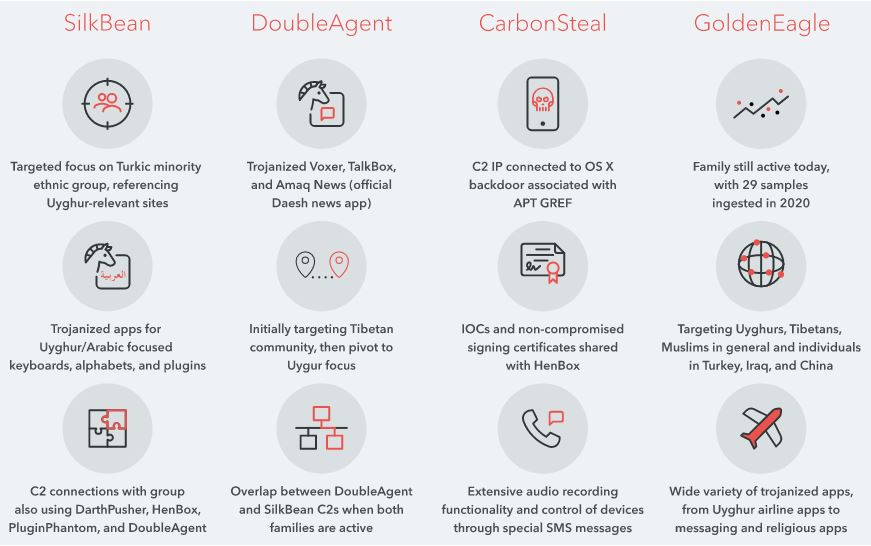
The tools named SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle each with their unique features are geared towards collecting the data of people under surveillance through malicious apps and then transmitting it to Chinese controlled C2 servers.
See: Chinese facial recognition database tracking Muslims left exposed
How the attackers managed to distribute these apps is through third-party fake app stores along with phishing attacks. There was no evidence found indicating that any compromise was made through the Google Play Store.
As shown in the infographic above, the success of the campaign can be attributed to the fact that the attackers trojanized many legitimate apps that are used daily such as Sarkuy – an Uyghur music app, and IBBIYJAWHAR – an Uyghur pharmaceutical app.
Furthermore, Lookout’s report explains that Tibetans were also targeted through these tools but to a significantly lesser extent as compared to the Uyghurs.
See: CIA’s 11-year old hacking campaign against China exposed
Talking about the source of these specifically within the Chinese administration, the researchers state,
..the past activity of this mAPT is connected to previously reported desktop APT activity in China4, which is linked to GREF, a China-based threat actor also known as APT15, Ke3chang, Mirage, Vixen Panda and Playful Dragon.
Moreover, the campaign also features malware samples with specific names that suggest China has been surveilling Muslims in about a total of 14 countries including but not limited to Turkey, Kuwait, and Syria as well in addition to the aforementioned minority.
To conclude, as for the scope of these attacks, other Android tools have also been discovered to be a part of the campaign in addition to the above ones and are known as HenBox, PluginPhantom, Spywaller, and DarthPusher.
See: Android malware HenBox hits Xiaomi devices & minority group in China
For the future, we can expect this to continue but we hope through this report, individuals belonging to these respective minorities and Muslims generally who are being targeted can take precautions to avoid installing any such malicious apps.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.