The attack could have been carried out with a “basic RF transceiver” which would not cost more than a few dollars at most.
Voice sensitive devices can ease your life, be it Amazon Alexa or simply a remote controller. However, this can also mean a new attack surface for threat actors to explore and prey on.
This is exactly what happened recently when the Comcast XR11 voice remote controller was found to be vulnerable and could be turned into a spying tool that eavesdrops on users.
This was eased by the fact that it uses radio frequency which can be used for remote access by its nature.
Discovered by researchers at Guardicore, the attack has been named WarezTheRemote and is termed to be a very serious threat considering that the remote is used for over 18 million devices across the USA.
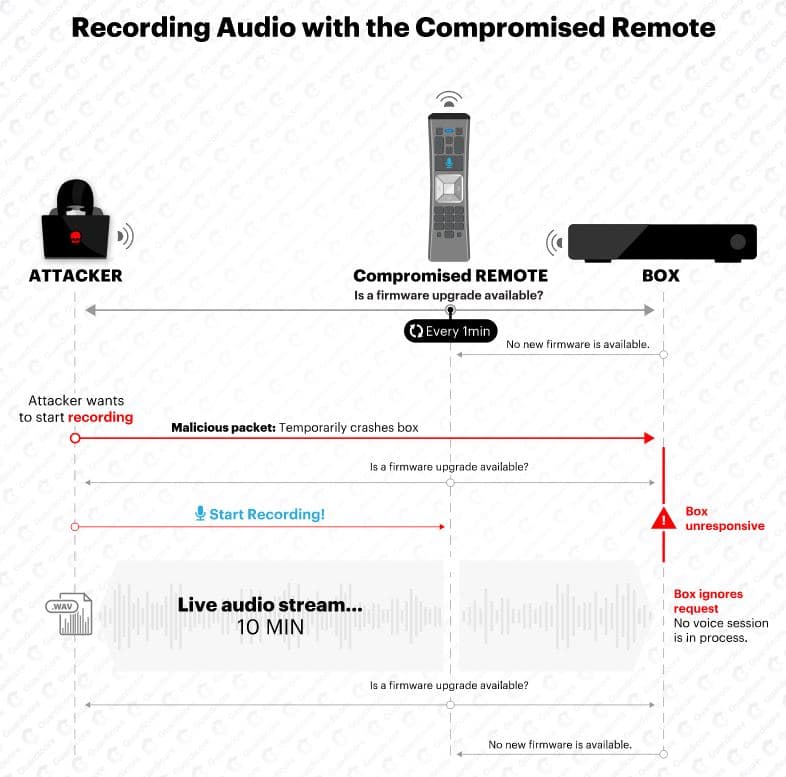
Explaining the attack process, the researchers state in a blog post that:
WarezTheRemote used a man-in-the-middle attack to exploit remote’s RF communication with the set-top box and over-the-air firmware upgrades – by pushing a malicious firmware image back the remote, attackers could have used the remote to continuously record audio without user interaction.
The vulnerability was that the original XR11 firmware didn’t verify that responses to encrypted requests are encrypted as well. This means that if an attacker within RF range had responded to outgoing (encrypted) requests from the remote in plaintext, the remote would have accepted the spurious responses.
An alarming thing to note is that the entire attack can be done remotely without the attacker having physical contact with the device and that too with a “basic RF transceiver” which would not cost more than a few dollars at most.
However, the attacker would need to be in a range of 65 feet to hear the conversations as the researchers demonstrated with the help of a “16dBi antenna.”
This can turn into a perfect spying tool for government-backed spying agencies looking to find dirt on their subject and malicious hackers looking for personal or financial information on victims – All the need to do is exploit the flaw, park their vehicle outside the victim’s house and rest is history.

Nonetheless, an amplifier could extend this distance range even further making it easier for threat actors to escape any physical suspicion as well.
Watch as researchers demonstrate how it is done:
For the time being, you can rest assured knowing that Comcast has fixed the vulnerability and released a patch on September 24, thanks to Guardicore’s timely disclosure in a responsible manner on April 21 earlier this year.
The patch numbered 1.1.4.0 fixes the issue by not allowing unencrypted firmware packets to be transmitted and also disabling a plain-text response capability that was responsible for the flaw.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
