Simple DNS hijacking enables attackers to distribute Fake Infected Flash Player at UConn website.
On Sunday, the official web portal of the University of Connecticut was hacked and used to distribute powerful malware disguised as fake Adobe Flash Player update.
The university’s deputy spokesperson Tom Breen informed that on December 27 at around 11:00 a.m. Educause, a non-profit organization responsible for managing UConn’s website, missed control of the DNS entries of the website.
DNS entries are basically domain name-IP address pairs that inform the internet browsing software regarding the location from where it has to download the content of a website.
The university’s DNS listing was hijacked by the attackers and all the users of uconn.edu URL were redirected to a fake server that was under the control of the attackers, reports The Daily Campus.
On that page, a blank screen awaited users and by the time the website loaded, a popup appeared compelling users to download the latest version of Adobe Flash Player in order to continue.
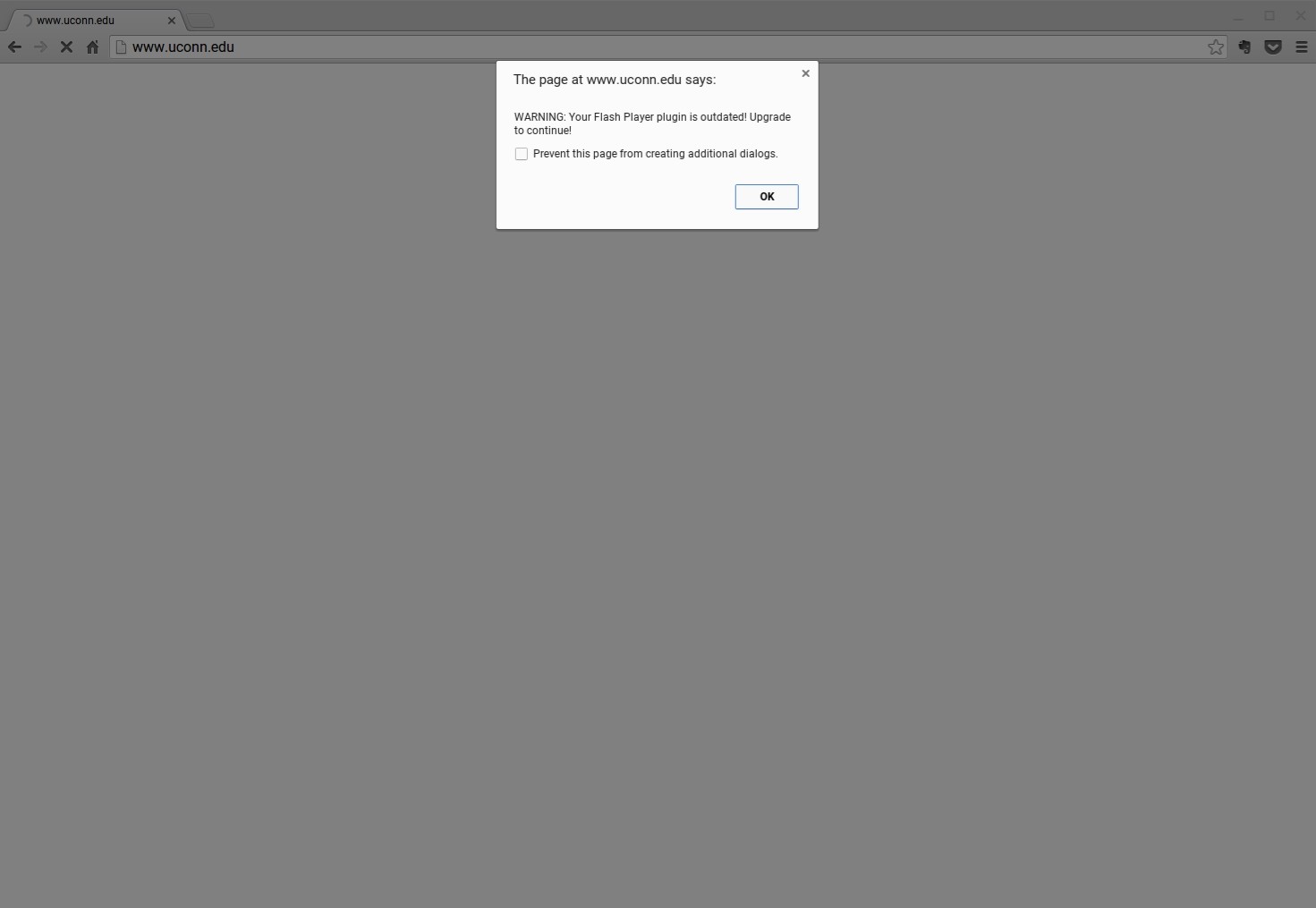
By clicking OK a file named adobe_flashplayer_18.exe gets downloaded, which obviously contains malware.
The UConn staff was quick to address this issues and managed to regain access to the DNS records but their efforts were delayed because the MX records were also corrupted, which contained all @uconn.edu email IDs.
This issue made it difficult to contact the ISP with an email originating from a legal and official address.
By the second day of Christmas, everything returned back to normal functioning and the malicious uconn.edu DNS entry was also phased out from the DNS servers.
However, despite the immediate response from the technical staff at UConn, visitors continued to experience the infected dialog box appearing on their screen for some time.
Breen clarified promptly that it was unclear how long this issue will continue to haunt users since the “impact wasn’t uniform on all ISPs.”
Breen also added that the university administration doesn’t think that this incident would impact the winter intersession classes that are due to start from Monday.
