The vulnerabilities, collectively called PixieFAIL, were discovered in the network stack of EDK II, during a cursory inspection of NetworkPkg and could be exploited during the network boot process.
Quarkslab bug hunters discovered nine serious vulnerabilities in EDK II, the de-facto open-source reference implementation of the UEFI specification, which could lead to remote code execution (RCE) attacks before booting the device.
These flaws, discovered in August 2023, led to DNS and DHCP poisoning attacks, information leakage, denial of service, and data insertion attacks at the IPv4 and IPv6 layers.
The vulnerabilities, collectively called PixieFAIL, were discovered in the network stack of EDK II, during a cursory inspection of NetworkPkg and could be exploited during the network boot process.
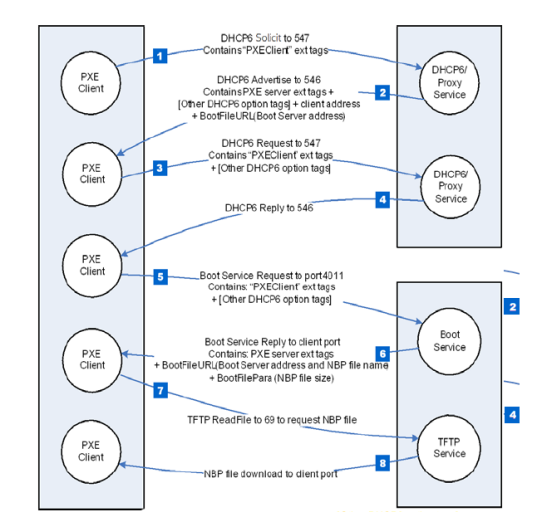
Network boot is a common feature on enterprise computers/servers, used to load an OS image from the network at boot time. This is popular in data centers and high-performance computing environments. Given that server farms and clusters often have hundreds or thousands of compute nodes, it simplifies management by downloading and running the OS from a central set of servers.
For your information, the Preboot Execution Environment (PXE), netboot, or Pixie boot, specifies a standardized client-server solution for network computers’ booting. It was introduced by Intel in 1998 and later got incorporated into the UEFI specification. With the release of UEFI version 2.2 in 2010, IPv6-based PXE became a part of the specification. The code to PXE is included in the UEFI firmware on the motherboard or within the NIC firmware read-only memory.
EDK II is UEFI’s open-source implementation developed and maintained by Tianocore, a community of developers leveraging the project for their own UEFI implementations. It incorporates NetworkPkg, a TCP/IP stack, to enable network functionalities during the initial PXE stage, allowing remote configuration and booting of networked computers.
According to Quarkslab’s blog post, all nine issues were discovered in the TianoCore EFI Development Kit II (EDK II) and affect UEFI firmware from AMI, Intel, Insyde, and Phoenix Technologies. Threat actors can exploit them for remote code execution, denial-of-service, DNS cache poisoning, and leakage of sensitive information. The vulnerabilities’ details are as follows:
CVE-2023-45229 (CVSS rating 6.5) and CVE-2023-45230 (CVSS rating 8.3) are vulnerabilities in DHCPv6 that cause integer underflow and buffer overflow in the DHCPv6 client.
CVE-2023-45231 (CVSS rating 6.5) and CVE-2023-45232 (CVSS rating 7.5) are vulnerabilities in a DHCPv6 Advertise message, causing out-of-bounds reads and infinite loops when parsing unknown or PadN options.
CVE-2023-45233 (CVSS rating 7.5) and CVE-2023-45234 (CVSS rating 8.3) are vulnerabilities in a DHCPv6 Advertise message causing an infinite loop when parsing a PadN option in the Destination Options header and the other affecting the processing of DNS Servers and Server ID options.
CVE-2023-45235 and CVE-2023-45236 are vulnerabilities affecting DHCPv6 proxy Advertise messages, with CVSS scores of 8.3 and 5.8, respectively, causing buffer overflow and predictable TCP initial sequence numbers. The ninth flaw is CVE-2023-45237 with a CVSS score of 5.3 and is related to a weakness in the pseudorandom number generator.
The list of vulnerabilities in EDK II devices is extensive, with the most severe being buffer overflow vulnerabilities for encouraging arbitrary code execution, potentially allowing attackers initial access and lateral movement.
Quarkslab contacted impacted software vendors to address the issue. Over half a year, they worked together to develop a patch without leaking any information. On January 16, 2024, a patch for fixing PixieFAIL at once was released with a firmware update.
The company has released proof-of-concept code for the first seven vulnerabilities, enabling defenders to detect infection attempts. The CERT Coordination Center has identified Insyde, AMI, Intel, and Phoenix Technologies as affected and published guidelines to deploy the fixes.
RELATED TOPICS
- Ivanti VPN Zero-Day Flaws Fuel Widespread Cyber Attacks
- Hackers can hijack your Bosch Thermostat and Install Malware
- Malware Turns Docker Servers into Traffic Boosted Crypto Miners
- CISA Warns of Exploited Flaws in Chrome and Excel Parsing Library
- Windows Defender SmartScreen Flaw Exploited with Phemedrone Stealer