A recently discovered cross-platform malware, appropriately named JaskaGO, has surfaced, targeting both macOS and Windows systems.
Cybersecurity researchers at AT&T Alien Labs have discovered a sophisticated malware strain called JaskaGO, crafted in the Go (Golang) programming language and equipped with the ability to maintain persistence in infected systems. It can exfiltrate valuable information, including browser credentials and cryptocurrency wallet details.
JaskaGO was detected in July 2023, targeting Mac users. Since then, the threat has evolved its capabilities and developed in both macOS and Windows versions, with a low detection rate, as evidenced by recent anti-virus engine samples.
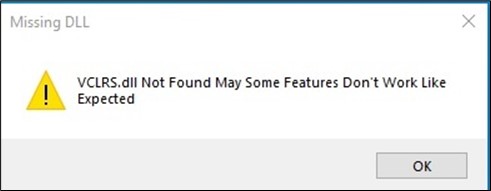
According to AT&T Alien Labs’ report, JaskaGO is a deceptive tool that presents a fake error message claiming a missing file to mislead users into believing the malicious code failed to run.
Further, it uses file names resembling well-known applications, such as “Capcut_Installer_Intel_M1.dmg” and “Anyconnect.exe,” suggesting a common strategy of malware deployment under the guise of legitimate software in pirated application web pages.
The malware first scans the system to determine if it is operating within a virtual machine (VM), obtaining general machine information, such as the number of processors, system up-time, available system memory, and MAC addresses. The presence of MAC addresses associated with well-known VM software, such as VMware or VirtualBox, is a key indicator.
If not detected, it starts collecting information and continuously queries its C2 server, awaiting instructions for various commands. These commands include creating persistence, stealer functionalities, pinging the command and control, executing shell commands, alert messages, retrieving the running process list, executing files on disk or in memory, writing to the clipboard, performing random tasks, downloading and executing additional payloads, initiating the process to exit (self), and initiating the process to exit and delete itself.
JaskaGO is equipped with extensive data exfiltration capabilities, and stores acquired data in a specially created folder, zipping and sending it to the attacker. It can be configured to target additional browsers, collecting browser information such as credentials, history, cookies, password encryption keys, profile files, and login information.
Persistence mechanisms are established through two methods: Service Creation in Windows and Execution as Root in macOS. In Windows, the malware creates a Windows Terminal profile by generating the file: UserName\AppData\Local\Packages\Microsoft. WindowsTerminal_*\LocalState\settings.json.”
On macOS, the malware employs a multi-step process to establish persistence within the system: Execution as Root, Disabling Gatekeeper, and Duplicating itself. To ensure persistence, the malware creates either LaunchDaemon or LaunchAgent based on successful root access to get automatically launched during system startup and further embed itself into the macOS environment.
JaskaGO is still being investigated; but serves as a warning to Mac users who may have felt unaffected by cyber threats, emphasizing the importance of constant vigilance regardless of the chosen operating system.
RELATED ARTICLES
- BlueNoroff APT Targeting macOS with ObjCShellz Malware
- Lazarus Group uses KandyKorn macOS malware for crypto theft
- Cracked macOS Software Laced with New Trojan Proxy Malware
- New Malware Turns Windows and macOS Devices into Proxy Nodes
- Researchers Leverage ChatGPT to Expose Notorious macOS Malware
- Windows, Linux, macOS Users Targeted by Chinese Iron Tiger APT Group