New Ransomware CryPy Can Encrypt Each File Individually with a Special Key — The C&C of this ransomware is hosted on a hacked Israeli server.
Isn’t this surprising that there is a new strain of ransomware that uses a different key whenever it encrypts a file? This ransomware has been written in Python and needless to say, it has helped the encryption game reach a new high by encrypting every file present on the victim’s computer with a unique key.
MUST READ: THE NASTIEST OF ALL RANSOMWARE MAMBA ENCRYPTS HARD DRIVE
Aptly titled CryPy , this ransomware isn’t the first or only one written in Python programming language. Remember, because Zimbra, HolyCrypt and Fs0ciety Locker are also written in the same language. Yet, the reason why CryPy stands out is that it encrypts files on a system individually and that too, with a unique key for every file. This obviously makes data decryption very difficult.
The ransomware was identified by Kaspersky researchers while looking for a particular security flaw, which allows attackers to upload and implement a PHP Shell Script to an exploitable Israeli web server, in the Magento Content Management System. This server serves as the command and control center for CryPy while the data is transferred in clear text format to the server. This allows attackers to carry out man-in-the-middle attacks as well as insert additional PHP scripts. These scripts then instruct the CryPy ransomware to invade the targeted computer(s). Moreover, this command and control server can be used to carry out phish attacks too as it contains PayPal phishing pages.
#Python #ransomware #CryPy retrieves encryption key and new filename for each file from CnC. https://t.co/RjtxuMg4r9 pic.twitter.com/FgINNyfb2v
— Jakub Kroustek (@JakubKroustek) September 9, 2016
Kaspersky researchers believe that the designers of this ransomware could be Hebrew-speaking. The team identified that CryPy has two main files namely boot_common.py and encryptor.py. The first one error logs on Windows OS and the second one is the main locker. After the computer has been infected the Registry Tools are the first to be disabled by CryPy and then the focus is shifted to Task Manager, Run and CMD. Afterward, boot status policy and recovery tools are disabled. When the disabling function has been performed successfully, the malware begins encrypting the files using a different encryption key for each file.
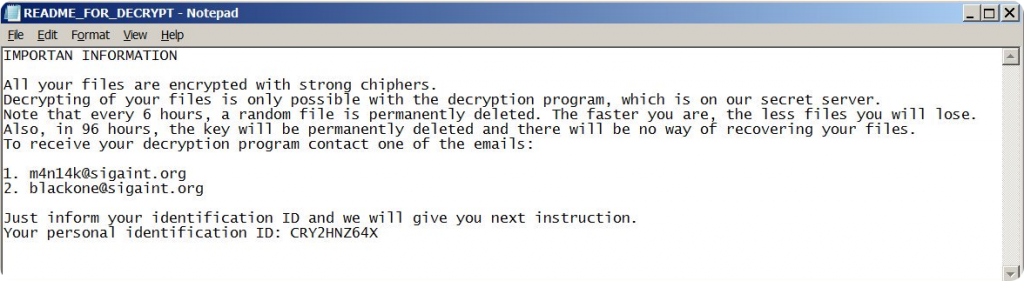
When the malware finishes locking of system and data encryption, the threat actor sends commands to inform the victims of the attack and to contact through email to pay for the decryption program. If the victims do as directed and contact the attacker via email, they are provided with a sample decryption key with which they can decrypt some of the files for free. This is the attacker’s strategy to build trust and force the victims into paying the ransom to get full decryption program.
ALSO READ: 7 CASES WHEN VICTIMS PAID RANSOM TO STOP CYBER ATTACKS
RELATED: THIS RANSOMWARE EXPOSES USERS’ LOCATION DATA ON THE INTERNET
According to Kaspersky researchers, currently, this ransomware is in the initial stages of its development because they feel that it has failed to encrypt files since the time its designer changed the server. Furthermore, the malware hasn’t been updated as well.
