It has been found that hackers can now easily abuse any website’s domain name based email addresses through the Google Apps for work. These e-mail addresses can then be used for sending phishing e-mails for an interested company so as to target users.
One can register an account with Google Apps for Work if one desires to have an e-mail address that is named after one’s brand in a manner like [email protected] instead of [email protected].
Must Read: How Gmail ID Can Be Hacked Despite Having Google’s Two-Factor Authentication On
With Google Apps for work, one can use services like Gmail, Drive storage, Calendar, online documents, video hangouts and many other collaborative services that could be shared with a team or organization.
All one needs is to sign up like a typical Gmail account and a custom domain name based email service from Google will be set up. As soon as the account is created, one can use his/her domain’s admin console panel on Google app interface, however, until the account is verified by Google, usage of any other service is not possible.
Sending Phishing E-mails from hijacked accounts
Patrick Fehrenbach and Behrouz Sadeghipour were to Cyber Security researchers who discovered that a hacker can put any unused domain – domains not previously registered with Google apps services – to register with the app. For example, bankofanycountry.com can be registered with Google apps for Work so as to get the [email protected] account. Though at this stage, one cannot use email services for [email protected] until the domain is verified by Google and so until then, no emails can be sent and received from that account.
Must Read: Researchers show how to hack Gmail with 92% success rate
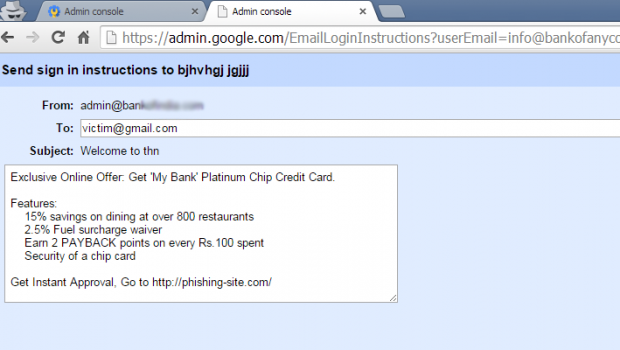
However, the researchers explained that the domain admin name can be sent to the organization users, that is, [email protected] – that has to be created from the panel in order to go ahead – through ‘Sign in Instructions’ using a page on Google apps that has an access to the following URL directly on the browser.
https://admin.google.com/[email protected]
Through the compose email address like the one shown above, the attacker can send all types of phishing email with harmful links to target users, fooling them into giving their personal information like passwords, financial detail and other types of sensitive data.
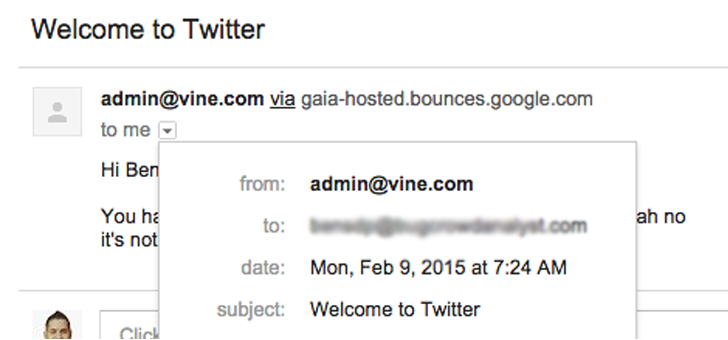
Before the security patch
Before Security Patch Researchers were able to achieve [email protected] (obtained by Twitter) and then send an e-mail to a target having a subject Welcome to Twitter thus convincing the target into providing personal details of Twitter account to this phishing e-mail.
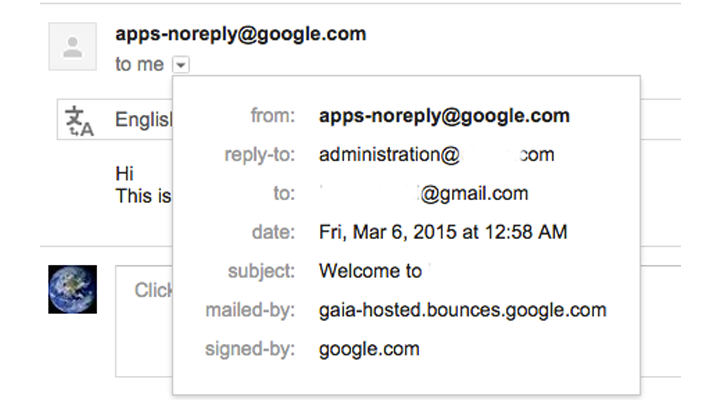
The security issue was reported to Google and perhaps it has applied a limited cover on the issue. This is because even after that, hackers can still access ‘Send Sign in Instructions’ for domains not verified, only this time through [email protected] rather than custom email address.
Behrouz told in a conversation that showing apps-noreply to senders is adequate according to Google.
After the Security Patch
The attackers are still not deterred from attacking victims as such. Usually, spam and doubtful e-mails are automatically filtered by Google as they get marked as spam or phishing warnings like when it is a legitimate source such as bank or Google, which they are not.
In contrast, through misusing Google’s vulnerability, attackers are able to send e-mails directly into the inbox without any warning since is the Google servers themselves that generate the e-mail.