KEY FINDINGS
- A new malware campaign is targeting the CVE-2023-40477 vulnerability in WinRAR.
- The campaign uses a fake proof-of-concept (PoC) script to trick researchers into downloading and executing a VenomRAT payload.
- The threat actors behind the campaign may be targeting researchers in order to gain access to their systems and steal their data.
- Palo Alto Networks recommends that users update WinRAR to the latest version and be careful about clicking on links in emails and on social media.
- If you believe that you may have been infected with this malware, you should immediately contact your IT security team.
Security researchers at Palo Alto Networks have discovered a new malware campaign targeting the CVE-2023-40477 vulnerability in WinRAR. The campaign uses a fake proof-of-concept (PoC) script to trick researchers into downloading and executing a VenomRAT payload.
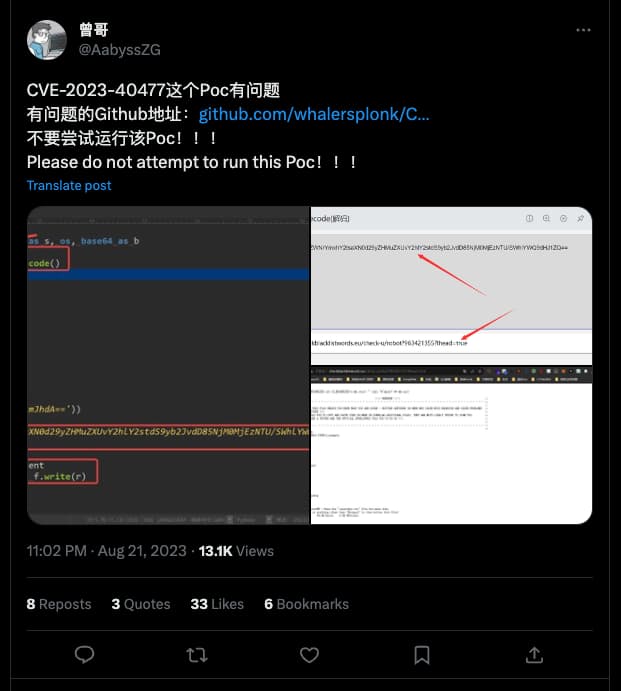
The fake PoC script is based on a publicly available PoC code for a vulnerability in GeoServer tracked by CVE-2023-25157. The code has been modified to remove comments regarding details about the CVE-2023-25157 vulnerability and to add additional code that downloads and executes a batch script with a comment of “Check dependency.”
It’s worth noting that @AabyssZG, a Chinese cybersecurity researcher and founder of Yuanlong Sec Security Team (AabyssTeam), was the first to discover the fake PoC script, which was hosted in a GitHub repository by a user named whalersplonk.
According to Palo Alto Networks’ blog post, the batch script creates a batch file in %TEMP%/bat.bat that reaches out to the following URL and runs the response:
hxxp://checkblacklistwords[.]eu/check.php
The downloaded PowerShell script downloads an executable from checkblacklistwordseu/words.txt and saves it to %APPDATA%\Drivers\Windows.Gaming.Preview.exe. The PowerShell script not only runs the executable but also creates a scheduled task named Windows.Gaming.Preview that runs the executable every three minutes to persistently run the payload.
The Windows.Gaming.Preview.exe executable is a variant of VenomRAT, which is a remote access trojan (RAT). VenomRAT can be used to steal data, execute commands on the victim’s system, and control the system remotely.
Palo Alto Networks researchers believe that the threat actor behind this campaign is targeting researchers in order to gain access to their systems and steal their data. The researchers also believe that the threat actor may be using the compromised systems to launch further attacks against other organizations.
An unknown threat actor attempted to compromise individuals by releasing a fake PoC after the vulnerability’s public announcement, to exploit an RCE vulnerability in a well-known application. This PoC is fake and does not exploit the WinRAR vulnerability, suggesting the actor tried to take advantage of a highly sought-after RCE in WinRAR to compromise others. The fake PoC is based on publicly available code for a vulnerability in GeoServer that sets off an infection chain that installs VenomRAT. While we cannot provide accurate figures on the impact or number of compromises, we saw that the instructional video provided by the actor along with the fake exploit script had 121 views.
Palo Alto Networks – Unit 42
Timeline of Events
The following is a timeline of events surrounding this incident:
- June 8, 2023: The Zero Day Initiative discloses the CVE-2023-40477 vulnerability to WinRAR.
- July 16, 2023: The threat actor sets up the checkblacklistwordseu domain.
- August 17, 2023: The Zero Day Initiative publicly releases information about the CVE-2023-40477 vulnerability.
- August 21, 2023: The threat actor commits the fake PoC script to GitHub.
- August 22, 2023: The threat actor uploads a video to Streamable demonstrating how to use the fake PoC script.
- August 25, 2023: The Streamable video expires.
Recommendations
Palo Alto Networks recommends that users take the following steps to protect themselves from this malware campaign:
- Update WinRAR to the latest version.
- Be careful about clicking on links in emails and on social media.
- Do not download and execute files from untrusted sources.
- Use a security solution that can detect and block malware.
If you believe that you may have been infected with this malware, you should immediately contact your IT security team.