Currently, the FjordPhantom malware appears active in Southeast Asia, covering countries including Malaysia, Thailand, Indonesia, Singapore, and Vietnam.
Cybersecurity firm Promon has identified a novel Android malware named FjordPhantom that employs virtualization to target applications. This technique has not been observed in any malware previously. FjordPhantom propagates through messaging services and combines app-based malware with social engineering to deceive banking customers.
Promon indicated in its report published on November 30, 2023, that only one sample of FjordPhantom has been obtained. However, researchers suspect that the malware is operational in Southeast Asia, encompassing countries such as Malaysia, Thailand, Indonesia, Singapore, and Vietnam.
“In discussions with banks in the region, Promon has learned that one customer was defrauded out of 10 million Thai Baht (approximately $280,000 – £225,000) at the time of writing,” noted the report author Benjamin Adolphi and shared with Hackread.com ahead of publication on Thursday.
Further probing revealed that the malware is distributed through emails, SMS messages, and messaging apps. Users are tricked into downloading a bogus banking app, which contains FjordPhantom.
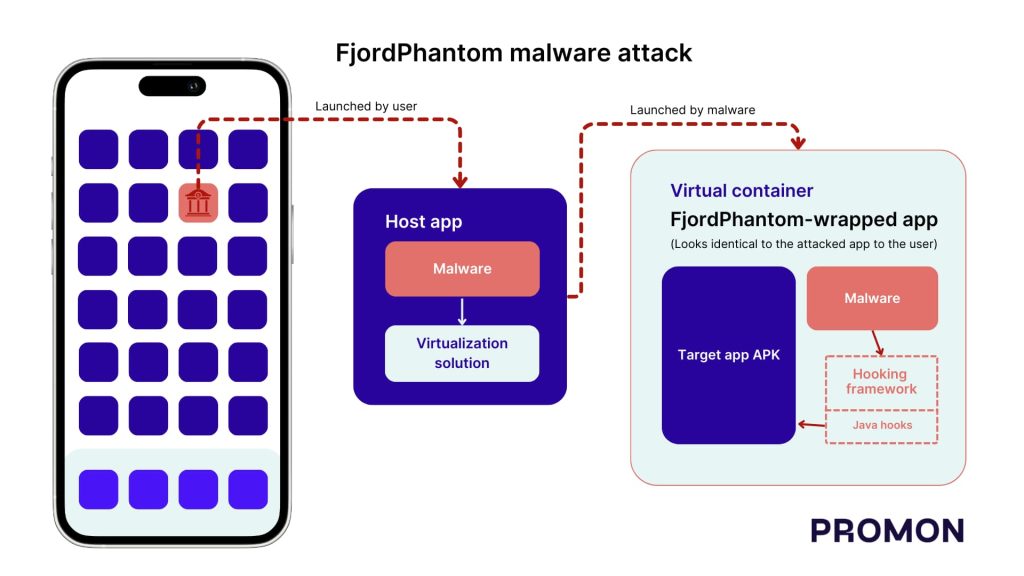
When this app gets installed, the attackers, posing as customer service representatives, guide the users about the steps to run the app. The malware uses virtualization to create a virtual container to run this app and attackers can monitor the user’s actions and steal their credentials.
The malware integrates various open-source/free projects from GitHub, incorporating a virtualization solution and a hooking framework. FjordPhantom utilizes virtualization solutions to circumvent the Android sandbox, enabling different apps to operate within the same sandbox.
This facilitates attackers in gaining access to files and memory, conducting debugging, and injecting code into other apps. The approach involves virtualization solutions loading their code into a new process before loading the hosted app’s code. Consequently, the malware can evade traditional code injection detection methods, as it doesn’t modify the original application.
The malware leverages the hooking framework to evade SafetyNet rooting detection, screenreader detection, and dismiss dialogue boxes warning the user of ongoing malicious activity on the system. Additionally, the malware logs various actions performed by the targeted applications, signifying active development and suggesting potential targeting of other apps in the future.
Researchers believe that FjordPhantom is a sophisticated Android malware used to commit real-world fraud.
Google’s Response to FjordPhantom Malware
Google has responded to the news published by Hackread.com. In an exclusive statement to the site, a Google spokesperson said that Android users are protected against threats such as the FjordPhantom malware due to the Google Play Protect feature.
“Users are protected by Google Play Protect, which can warn users or block apps known to exhibit malicious behaviour on Android devices with Google Play Services, even when those apps come from sources outside of Google Play.”
Google Spokesperson
Nevertheless, here are 5 tips for Android users to protect themselves from malware, especially banking trojans:
- Download apps only from trusted sources: The safest way to get apps for your Android device is to download them from the official Google Play Store. Google has reviewed apps in the Play Store and are less likely to be malicious. If you need to download an app from a third-party source, make sure to do your research and only download apps from reputable websites.
- Be careful about the permissions you give apps: When you install an app, it will ask you for permission to access certain data or features on your device. Only give apps the permissions they need to function. For example, if you’re installing a banking app, it will need permission to access your contacts and call history. However, there’s no reason for it to need permission to access your photos or location.
- Keep your device up to date: Google regularly releases updates for Android that fix security vulnerabilities. Make sure to install these updates as soon as they become available. You can enable automatic updates in your device’s settings.
- Install a mobile security app: A mobile security app can help protect your device from malware by scanning apps and files for threats. It can also block malicious websites and phishing attempts. Many different mobile security apps are available, so do some research to find one that’s right for you.
- Be cautious about what you click on: Be careful about clicking on links in emails or text messages, even if they appear to be from someone you know. These links could take you to malicious websites that could install malware on your device.
- IBM X-Force Discovers Gootloader Malware Variant- GootBot
- Qakbot Botnet Disrupted, Infected 700,000 Computers Globally
- Telekopye Toolkit Used as Telegram Bot to Scam Marketplace Users
- Proton CAPTCHA: New Privacy-First CAPTCHA Defense Against Bots
- Google Workspace Exposed to Takeover from Domain-Wide Delegation Flaw