The IDF and Israeli Security Agency Shin Bet have jointly conducted an operation called “Operation Hunter’s Network” against the Hamas network after the officials got a hint of a new campaign from Gaza-based Hamas hackers. In this new campaign, hackers posted seductive pictures of young, beautiful Israeli women on social media to attract IDF soldiers and get classified information from them.
The operation against these hackers lasted for months after receiving reports about suspicious online activities of some of the Israeli soldiers. Through the operation, a large number of accounts owned by Hamas’ operatives on social media platforms including Facebook was identified. These accounts were operated using stolen identities or fake information and the sole purpose was to lure IDF soldiers through seductive profiles to obtain confidential information. Both reservists and regular soldiers fall prey to Hamas’ trap.
Read More: This is how hacked Israeli drone feeds look like
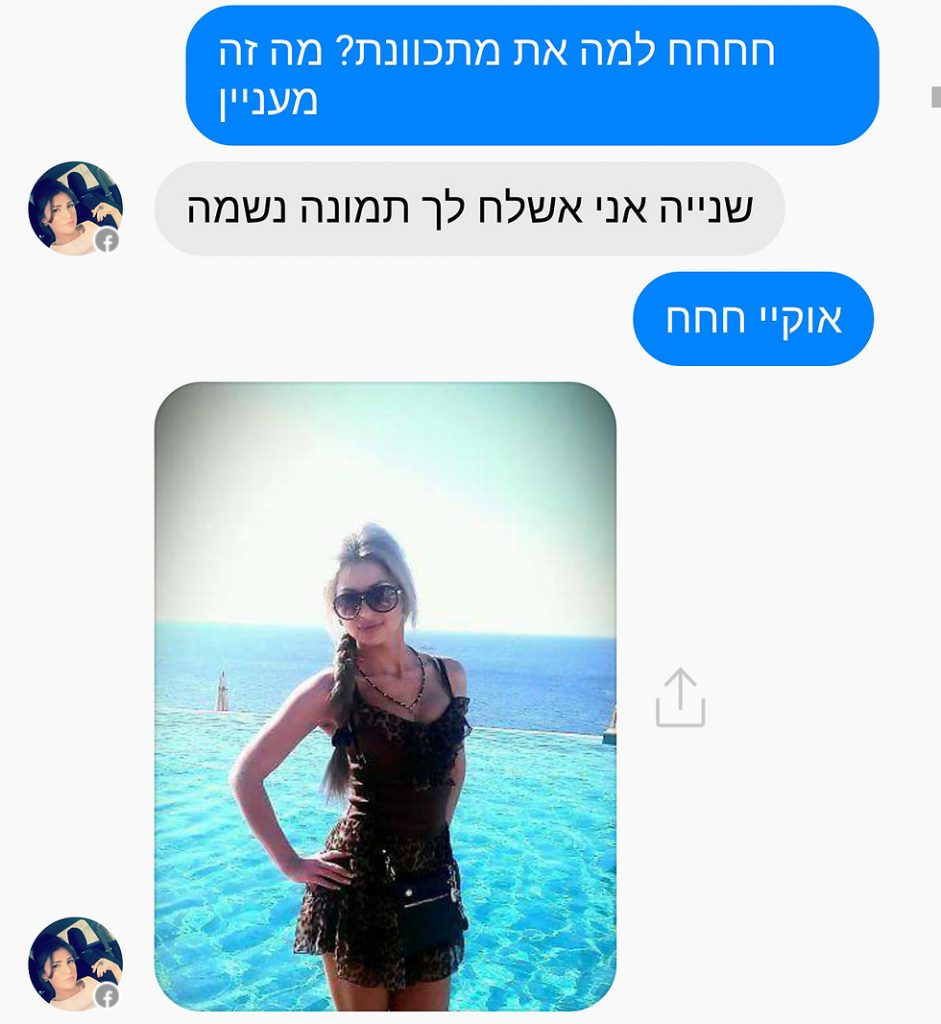
Military Intelligence officials in Israel are referring to these accounts as Enemy Accounts. The Hamas operatives hunted down IDF soldiers and gained their confidence. After having an intimate chat, the supposed account holder asked them to download an app such as Wowo Messenger, SR Chat and YeeCall Pro to start video chatting. These apps actually were infected with Trojan horse viruses.
After the virus reached its destination, that is, the soldier’s phone, the Hamas operatives immediately obtained access to the data on their phones such as pictures, text messages, WhatsApp conversations, contacts and they also identified the location of the soldier. The virus also enabled Hamas operatives to access the camera and microphone of the phone, through which they could capture images and record communications and conversations. They also downloaded other applications to ensure that the phone remains infected even after the malicious app was detected and deleted. The soldier remained unaware of this data capture.
As soon as the phone was infected the seducers completely stopped contacting the soldiers, this sudden change of attitude alerted them about some kind of foul play and they informed their commanders.
A senior IDF official told The Jerusalem Post that the male soldiers were the key targets in this campaign but some female soldiers were also trapped. The victims involved a major as well but the campaign was believed to be a low-level threat. However, the fact cannot be ignored that this could have been a serious national security issue.
“There is, of course, a potential of serious harm to national security, but the damage that was actually done was minor, anyone who was infected is not infected anymore,” said the official.
No arrests have been made so far because the soldiers were unaware of the trap and they were just the victims. The infected phones have been reformatted so that they Hamas operatives aren’t able to compromise them any further.
In order to increase public awareness regarding the risks involved in using social media and how to ensure that the general public is prevented from such traps, Operation Combat Hunter was launched by the military as a precautionary measure. The military is also expanding restrictions on the use of social media by Israeli soldiers. Such as, high ranked military personnel (those who are Lieutenant-Colonel or above) cannot upload their pictures in uniform or disclose that they are IDF soldiers. The IDF has also released the pictures of 16 characters that Hamas is using to entice and trap Israeli military personnel.
Read More: Israel’s Major Traffic Tunnel Hit by a Massive Cyber-Attack


New guidelines for using social media have also been released by the Military Intelligence according to which soldiers can only befriend those people who they know personally and they cannot upload confidential information or download applications from third-party sources.
Furthermore, the IDF plans to train its soldiers to become aware of the threat that is posed by the posting or uploading of personal pictures on social media platforms. A new division will also be created that will operate 24/7 and will immediately notify the military about any suspicious online activity.
The IDF noted that over 3,000 IDF related Facebook groups are currently active out of which dozens are closed groups that allow soldiers to openly discuss operational issues. Hamas managed to infiltrate these pages after gaining the trust of the admins. Now, the pages’ administrators have been alerted as well and instructed to add only those people to their groups whom they already know.
The joint operation was conducted by the IDF’s Information Security Department and Cyber Defense Unit in collaboration with Shin Bet. The main platform exploited by Hamas to carry out this campaign was Facebook. It is believed that through this campaign, Hamas only managed to get images of IDF war rooms, armored vehicles, tanks, observation devices and the location of soldiers posted in the border area.
This is not the first time when the Israeli military has embarrassed itself with such scams. In 2015, hackers used pictures of IDF women soldiers to successfully breach Israeli military servers.

Read More: Israel’s Channel 10 TV Station Hacked by Hamas
In 2016, pro-Hezbollah hackers calling themselves Kadimon or Qadmon (نحن قادمون) hacked Israeli government security cameras to keep an eye on activities of government workers.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
