Remember: There ain’t no such thing as a free lunch!
KEY FINDINGS
- A supply chain attack on the Free Download Manager website redirected some users to a malicious Debian package that installed password-stealing malware.
- The malicious package was hosted on the domain “deb.fdmpkgorg” and contained a post-install script that downloaded two executables to the /var/tmp/crond and /var/tmp/bs file paths.
- The crond job scheduler was used to force a document present at /var/tmp/crond to launch repeatedly at 10-minute intervals, effectively backdooring the infected systems.
- The attacker then established a reverse shell to their owned server and installed a Bash stealer on the infected system.
- The Bash stealer collects sensitive data such as system details, browsing history, cryptocurrency wallet files, saved passwords, and cloud services credentials.
- The campaign is no longer active, but the end goals of the attackers are still unknown.
- Not all users who downloaded the Free Download Manager received the malicious package, which may have helped the campaign to go undetected for so long.
- This highlights the need to secure Linux desktops and server devices with effective and reliable security solutions.
It is hard to process, yet not surprising, that a widely trusted free software download site was exposing unsuspected users to information-stealing malware for the past three years, and no one could have detected it until this week.
According to the cybersecurity firm Kaspersky, the malicious supply chain attack remained active from 2020 to 2022 but was only recently discovered by its researchers while investigating suspicious domains.
According to Kaspersky’s blog post, a website “freedownloadmanagerorg” used to offer e legit Linux software “Free Download Manager.” Since January 2020, it started offering a benign version of this software after redirecting users to a malicious Debian package that contained a post-install script.
Researchers noted that the website redirected users to another domain “deb.fdmpkgorg,” which hosted the Debian package. The script downloaded two executables to the /var/tmp/crond and /var/tmp/bs file paths.
This script used the cron job scheduler to force a document present at /var/tmp/crond to launch repeatedly at 10 minutes intervals so that the systems that have installed this decoyed version of the Free Download Manager were backdoored permanently. For your information, crond, aka Bew, is a backdoor variant discovered in 2013.
The attacker then established a reverse shell to their owned server and installed a Bash stealer on the infected system. This stealer was previously analyzed by Yoroi in June 2019. It collects sensitive data such as system details, browsing history, cryptocurrency wallet files, saved passwords, and cloud services credentials, including AWS, Oracle Cloud Infrastructure, Google Cloud, and Azure.
After collecting these details, the malicious stealer contacts the C2 server to download an uploader binary and saves it to this path: /var/tmp/atd. This binary is then used for uploading stealer execution results to the malware operator’s infrastructure.
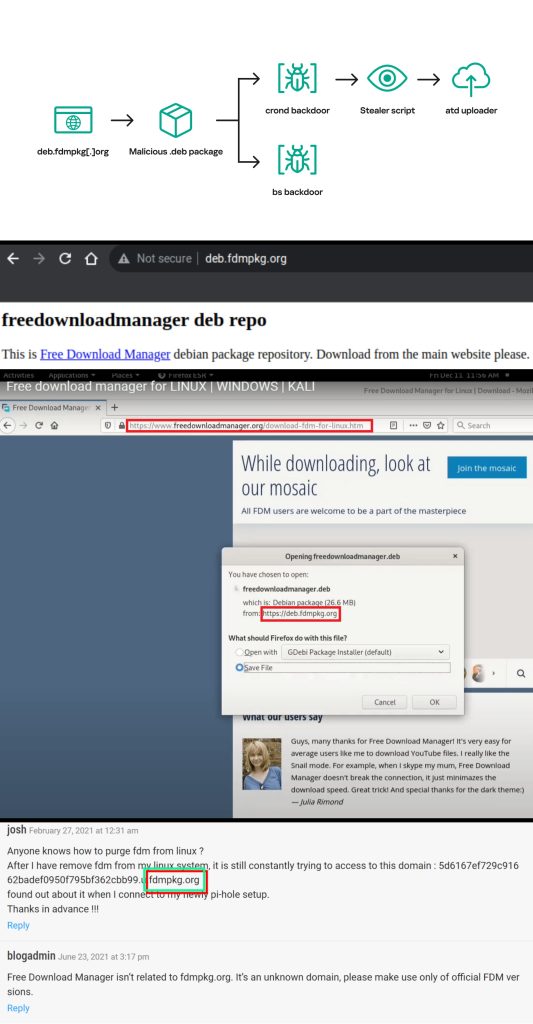
“The communication protocol is, depending on the connection type, either SSL or TCP. In the case of SSL, the crond backdoor launches the /var/tmp/bs executable and delegates all further communications to it. Otherwise, the reverse shell is created by the crond backdoor itself,” the report read.
Nevertheless, the team at Free Download Manager has apologized to its users and vowed to implement better security measures. It has also urged users to scan their system and change their passwords.
“If you were among the subset of users who tried to download FDM for Linux from our compromised page during the mentioned timeframe, we strongly recommend conducting a malware scan on your system and updating your passwords as a precautionary measure.”
Free Download Manager team
Thankfully, this campaign isn’t active anymore. The campaign’s end goals are still under investigation. However, an interesting finding is that not all users who downloaded the Free Download Manager received the malicious package. Perhaps this is how the campaign remained undetected for so long. This highlights the growing need to secure Linux desktops and server devices with effective and reliable security solutions.
RELATED ARTICLES
- Malware hits Freelancers at Fiverr and Freelancer.com
- Almost Every Major Free VPN Service is a Glorified Data Farm
- Popular free Android VPN apps on Play Store contain malware
- Free WinZip trial popup vulnerability lets hackers drop malware
- This malware hides behind free VPN, pirated security software keys
