Cybersecurity researchers at Singapore-based Group-IB have unmasked EagleStrike, a subgroup of the GambleForce hacker group. They are opportunistic hackers exploiting simple vulnerabilities.
In September 2023, Group-IB’s Threat Intelligence unit discovered a command and control server hosting publicly available open-source pentesting tools, none being custom-made, designed for SQL injections.
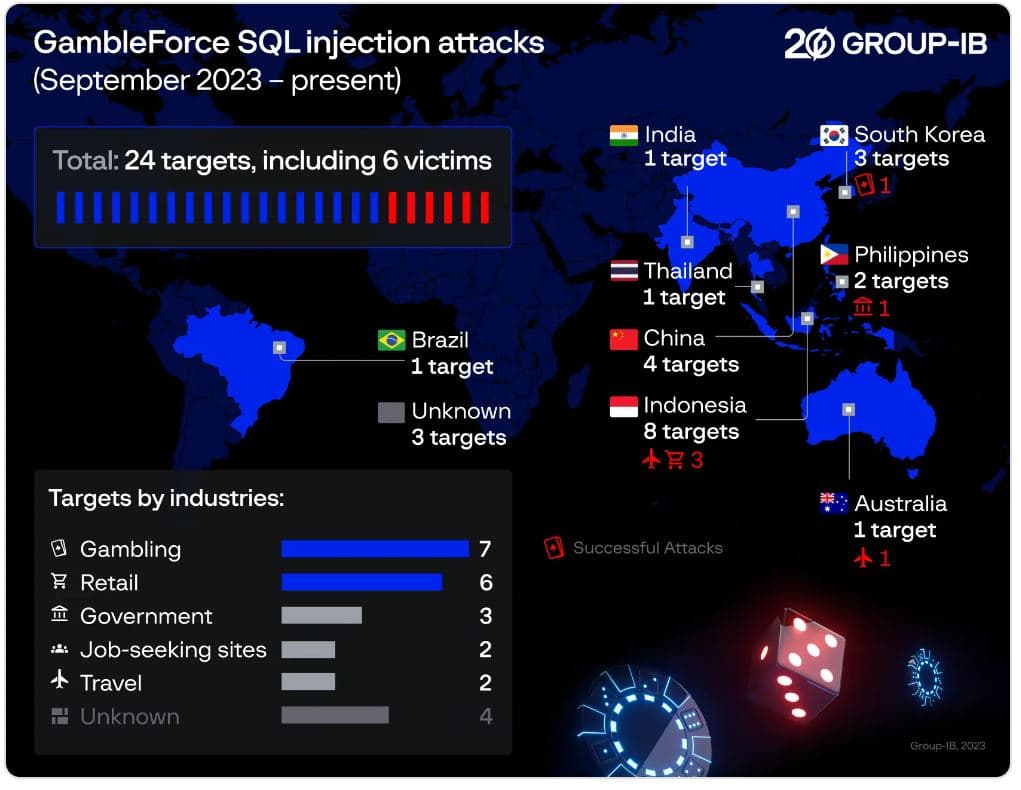
The attacker was identified as “GambleForce,” who had targeted 24 organizations in government, gambling, retail, travel, and job-seeking sectors across 8 countries between September and December 2023, successfully compromising 6 websites in Australia, Indonesia, the Philippines, and South Korea. The group has also targeted websites in China, India, and Thailand.
The group uses basic yet effective techniques like SQL injections. It exploits vulnerable website content management systems (CMS) to extract user databases containing logins, hashed passwords, and tables from accessible databases.
GambleForce is not selective in its targets but collects hashed and plain text credentials. This suggests a broader motive beyond targeted attacks, possibly amassing data for future exploits or selling on the dark web.
The threat actors aim to exfiltrate any available information within targeted databases, such as hashed and plain text user credentials. The group’s actions with the stolen data remain unknown.
In an attack targeting Brazil, GambleForce exploited CVE-2023-23752, a vulnerability in the Joomla CMS, and snatched data directly from contact form submissions, showcasing their adaptability and willingness to improvise.
Further probing revealed that GambleForce uses open-source tools like dirsearch, redis-rogue-getshell, and Tinyproxy for directory brute-forcing, web traffic intercepting, and SQL injections to exploit vulnerabilities in database servers. Their preferred tool is sqlmap, a pentesting tool that exploits SQL injection vulnerabilities.
Researchers also found Cobalt Strike, a popular pen-testing framework, on their server, showcasing commands in Chinese. It is worth noting that recently Chinese scammers have wreaked havoc by creating cloned versions of legitimate websites and redirecting visitors to gambling sites.
In November 2023, Hackread.com reported about the activities of Chinese hackers in which MindaNews, a Philippine newspaper, discovered a Chinese clone of its website (mmart-inn.com) that has been illegally replicating the newspaper’s content for two years, with the most recent translation being from February 2023.
In its blog post, Group-IB’s Threat Intelligence wrote that its researchers shared the recent findings with its 24/7 Computer Emergency Response Team (CERT-GIB), which took down the cybercriminals’ C2 server. GambleForce is likely to regroup/rebuild its infrastructure before launching new attacks.
Nevertheless, the case goes on to show that even the most basic security gaps can have significant consequences, underscoring the need for a layered defence strategy that prioritizes patching known vulnerabilities and implementing vital security controls.
RELATED ARTICLES
- Domain Squatting and Brand Hijacking: A Silent Threat
- Chinese APT Posing as Cloud Services to Spy on Cambodia
- Chinese APT spying on Vietnam military with FoundCore RAT
- Hackers attack Casino’s fish tank thermometer to obtain data
- ChatGPT Clone Apps Collecting Personal Data on iOS, Play Store