A website has been exposed tricking unsuspecting users into downloading a Coronavirus tracking app on their Android phones which in reality is ransomware.
Coronavirus or COVID-19 is taking over the world by storm and curiosity to learn about this disease is what hackers are exploiting these days – In the latest; a malicious website has been identified offering Coronavirus tracking app for smartphones which in reality is ransomware aiming at your wallet.
See: Hackers clone ProtonVPN website to drop password stealer malware
According to the IT security researchers at DomainTools (who identified the scam), the malicious domain was registered on March 8th, 2020 claiming to provide a real-time Coronavirus outbreak tracker app through download.
The website (coronavirusappsite) also claims to offer in-depth information on Coronavirus infection including a live heat-map displaying how many countries have been affected so far.
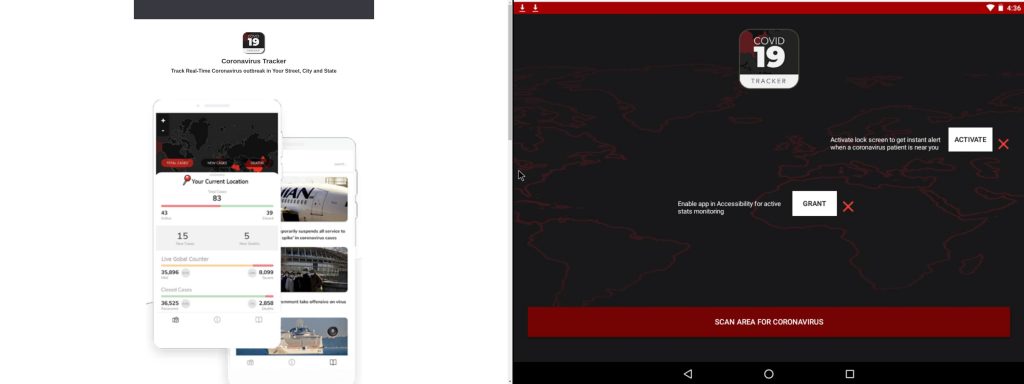
However, in a blog post, the company revealed that once downloaded and installed on your Android smartphone, the so-called Coronavirus tracking app turns into ransomware which the researchers have dubbed as CovidLock – The attack executes by forcing the victim to change their phone’s password ultimately blocking them from accessing their device.
See: Hackers hit hackers in a new malware campaign
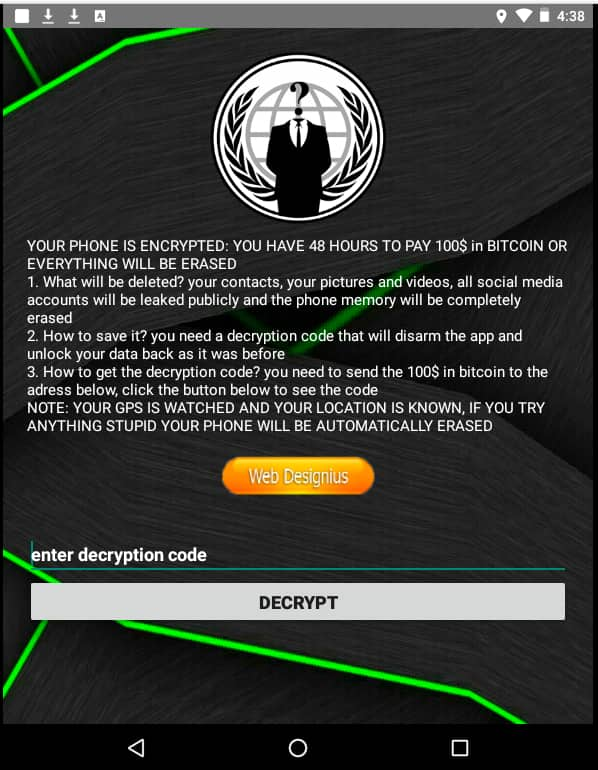
Furthermore, the ransomware locks the targeted phone’s screen and displays ransom note asking the victim to send $100 in Bitcoin or kiss goodbye to their data including contacts, photos, and videos. The ransom note also threatens to leak social media details of the victim on the Internet and completely erase the phone’s memory.
“Your GPS is watched and your location is known, if you try anything stupid your phone will be automatically erased,” says the ransom note in a desperate attempt to steal money from the victim.
Here is a full preview of the ransom note:
According to DomainTools’ senior security engineer and malware researcher Tarik Saleh, to unsuspecting users, it may look like a sophisticated ransomware scam carefully crafted to take advantage of fears amid Coronavirus infection but in reality, none of the files on a targeted smartphone are actually encrypted.
“This is screen-lock ransomware and doesn’t encrypt any user files,” said Saleh. “Since Android Nougat has rolled out, there is a protection in place against this type of attack, however, it only works if you have set a password. If you haven’t set a password on your phone to unlock the screen, you’re still vulnerable to the CovidLock ransomware.”
It is unclear who is behind this campaign or who owns the domain, however, IP address and other records indicate that its owner might be someone in Morocco.
At the time of publishing this article; the Bitcoin wallet of scammer was empty indicating that so far no one has fallen for Coronavirus tracking app ransomware scam. However, if you are curious about Coronavirus do not download such apps from third-party stores and keep scanning your device with a reliable anti-ransomware app.
Coronavirus malware scam is not new
This is not the first time when Coronavirus has been used to spread malware and steal personal information of unsuspecting users. On March 12th, HackRead reported how hackers have been using fake live heat map of Coronavirus to spread Azorult malware, which is a data-stealing malware discovered in 2016.
Earlier in January this year, cybercriminals were caught using the Coronavirus disaster to spread fear and infect users’ devices with Emotet banking trojan that has been used in various malicious campaigns in the past for gaining financial data.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
