Google attributed the malware campaign to a group of attackers recruited via a Russian-language hacker forum.
Google has disclosed details of a new campaign involving phishing attacks launched against YouTube channel owners with the sole purpose of hijacking their channels. According to the report, threat actors are using cookie theft malware in the attacks to take control of the device/computer and hack YouTube accounts.
Researchers revealed that attackers behind this channel hijacking scheme are financially motivated as they auction off the stolen channels if they have a large number of followers or promote cryptocurrency scams by abusing these accounts.
About the Campaign
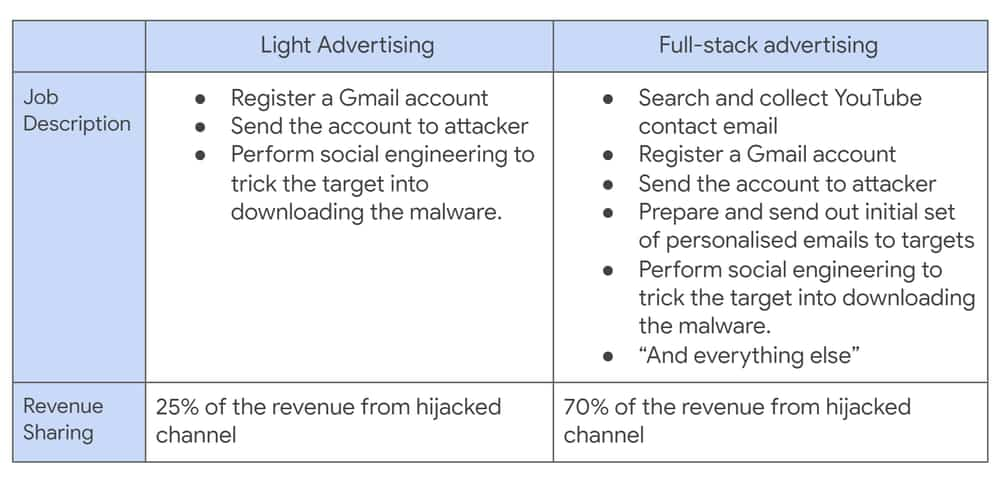
In their report, Google’s Threat Analysis Group’s (TAG) Ashley Sen attributed to a group of attackers recruited via a Russian-language forum through the following job description, offering two types of work:
The attacks have been going on since 2019, and attackers used to lure targets through fake collaboration schemes such as requests to purchase ads on the targeted user’s channel, photo editing, online games or music players, VPNs, and demo for anti-virus software, etc.
After gaining the channel owner’s trust, the scammers would send the victim a URL through email or a Google Drive PDF in which they would promise a legitimate software, but actually, it redirected them to a malware landing page.
SEE: Vlogger loses $2M in cryptocurrency during YouTube live stream
When the malware was installed on the computer, it would steal cookies from the browser using a smash-and-grab technique, and the cookies were used to hijack the session and eventually hijack the channel. Scammers would then look to sell it to the highest bidder with an asking price of $3,000 to $4,000 or launch cryptocurrency scams using it.
It was observed that scammers sent phishing messages to email IDs made public by YouTube channel owners for business purposes.
The malware used in the scam includes Azorult (also used in recent COVID-19 related scams), Raccoon, Vidar, Grand Stealer, Kantal, Nexus stealer, Masad, The Thief, Predator, Vikro Stealer, and RedLine along with open-source tools like AdamantiumThief and Sorano.
How was The Campaign Busted?
Google’s TAG team collaborated with Gmail, YouTube, Trust&Safety, CyberCrime Investigation Group, and Safe Browsing teams to decrease the distribution rate of phishing emails on Gmail. Their collaboration decreased the volume of the phishing campaign by 99.6% since May 2021 and blocked 1.6 million messages to probable targets.
SEE: OpenSea vulnerability allowed crypto stealing with malicious NFTs
Furthermore, around 62k Safe Browsing phishing page warnings and 2.4k files were blocked, with nearly 4,000 accounts restored successfully. After attackers sensed increased detection efforts, they turned to other email providers such as Seznam.cz, email.cz, Aol.com, and post.cz.
It was also noted that the attackers had registered nearly 15,000 accounts and had domains associated with fake firms, while over 1,000 websites were used to distribute malware. For preventing further distribution of phishing emails, Google notified the FBI as well.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.