Raccoon malware is a powerful malicious tool designed to steal all kinds of personal data including login credentials, desktop crypto wallets, credit card information, etc.
According to a report from IBM X-Force, in a recent sextortion scam, victims’ devices are infected with Raccoon payloads distributed via emails delivered using different subject lines while there is sextortion scam campaign active as well, which is none other than the typical DocuSign.
See: New sextortion scam claims to record you with hacked Google Nest cam
As per the findings from Threat Intelligence researchers at IBM X-Force, attackers are trapping unsuspecting users through infected emails from the Outlook promising to show nude extortion photos of their friend’s girlfriend.
The recipient is informed that the email is sent by the Red Skull Hacker Crew and who possess nude images of the owner’s girlfriend for which they have demanded $500.
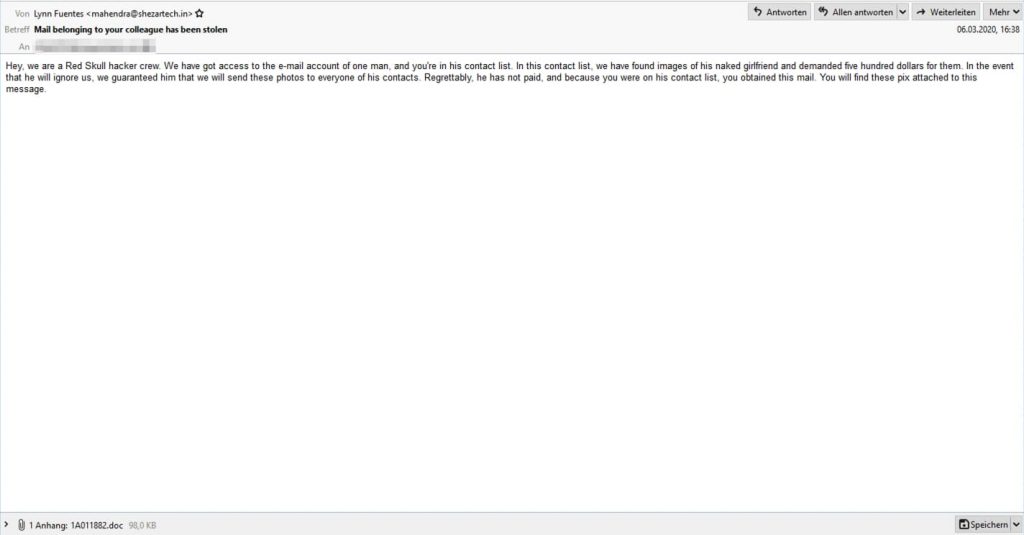
Since the victim failed to pay the ransom, they are distributing photos to all of his contacts. This is how the cunning cybercriminals are luring innocent users in getting their devices infected by opening an attachment that is part of the email.
According to the blog post published by researchers, Some of the subject lines identified by researchers are as follows:
- “Mail belonging to your colleague has been stolen;”
- “Your colleague’s account was compromised;”
- “We have got access to your friend’s account;”
- “Private info belonging to your friend has been stolen.”
When the victim opens the attachment, all that’s visible are few blurred images and the user is asked to enable content in order to view pictures.
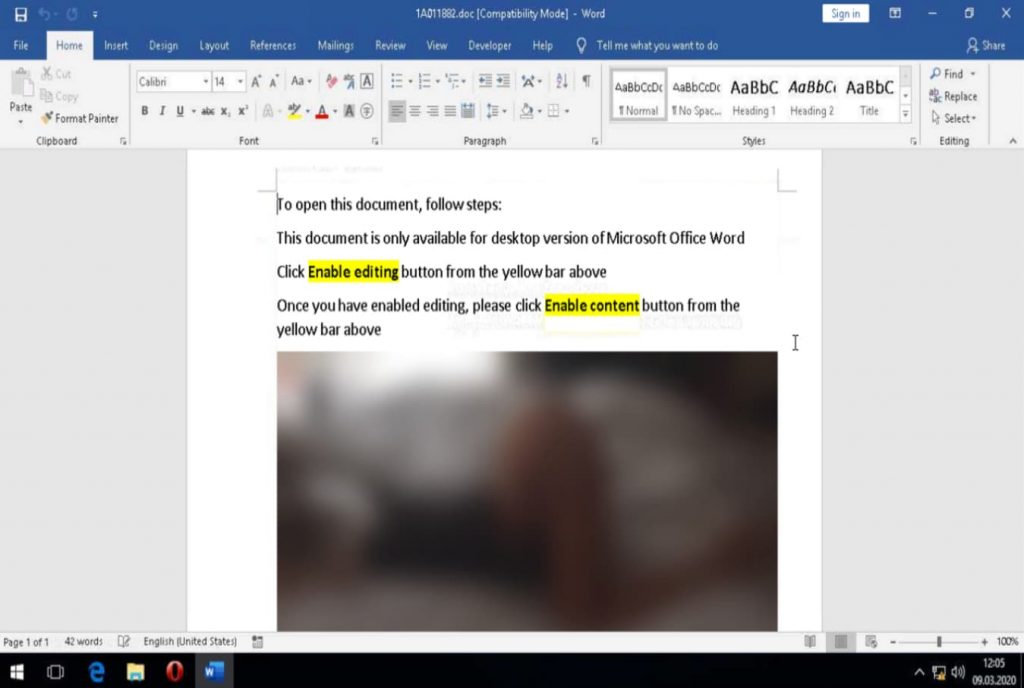
However, as it always happens, the attachment is loaded with raccoon malware that is immediately deployed on the victim’s computer through embedded macros. These macros activate a Powershell command, which actually is responsible for installing the malware.
See: New sextortion scheme uses victims’ real password for blackmailing
The domain that was delivering the malware has been taken down but it is expected to resume operation very soon or attackers can enable another domain to continue their campaign.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
