The Sextortion Campaign involves Passwords Stolen from Old Data Breaches.
Internet users need to be wary of a new phishing scam that is actually a sextortion scheme, which utilizes old passwords of users and blackmails them for watching pornography. The scammers claim to have recorded footage of the victim while watching porn. They also claim to have the victim’s password that they used to install spyware on the targeted computer and when the victim visited pornography websites, they activated the webcam to record footage.
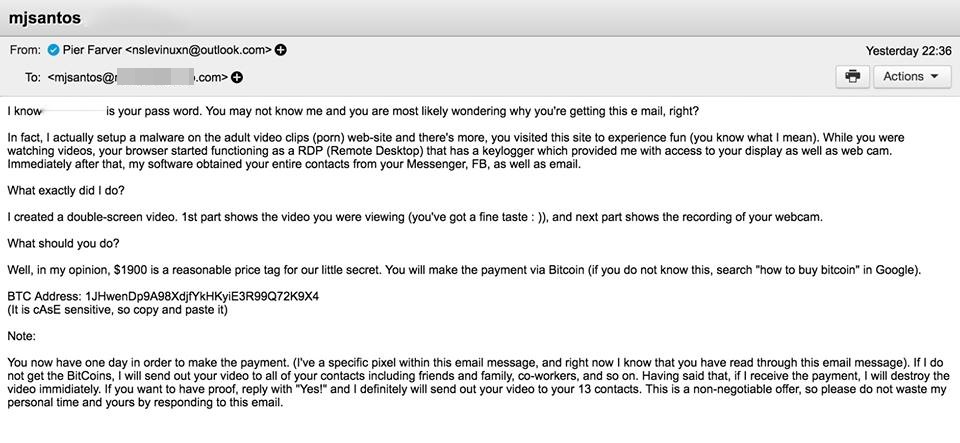
Security experts have managed to identify the messaging that these attackers may initiate with the victims. Twitter programmer Can Duruk explained in detail what users should expect. The entire messaging trail is available below:
What’s utterly concerning is that usually, the password highlighted in the email sent by the scammers is a legitimate one, which the victim had previously used. Security experts opine that it is quite probable that cyber-criminals are utilizing old passwords obtained from various large-scale data breaches such as the ones suffered by Yahoo, Uber, LinkedIn, Tumblr, Dropbox and Under Armour, etc., to blackmail users. They are simply matching old passwords with useful identifiers like email IDs. After successfully locating the victim, they can initiate a blackmailing campaign easily.
This scam has also featured on the blog site of well-known security journalist Brian Krebs, who writes that this “improved sextortion attempt” is most likely semi-automated. Krebs notes that the attacker(s) most probably has created a script that directly draws user credentials from a decade old data breach of a famous website.
Whoever got his or her password compromised in that particular data breach is now receiving the email from the scammer; Krebs believes that the scam will be refined more and scammers will use more relevant and recently compromised credentials. The primary purpose of this scam campaign is to convince users that the “hacking threat is real.”
Krebs also highlighted the fact that within the past 72 hours, he has received complaints from three users who have received a similar email from the scammer; the passwords mentioned in the emails were indeed authentic as users have at some point used and linked them to their email IDs. It was also noted by the recipients of emails that the passwords were nearly 10 years old and haven’t been used by them on their current computers.
The FBI suggests that users must remain alert and avoid opening attachments from unknown senders and be very careful while opening attachments sent by known contacts. Furthermore, users must not send compromising pictures of themselves to anyone no matter how trusted the contact must be. When not in use, webcams should be turned off manually or covered.