In 2012, LinkedIn became the recipient of a large data breach that is still haunting the platform. Initially, it was reported that the hacker(s) involved managed to steal 6.5 million credentials but latest reports suggest that the data hack was far more widespread.
This revelation has arrived from Leaked Source, which is a paid search engine that provides details about hacked data. According to estimation from Leaked Source, more than 167million credentials were hacked during 2012 data breach on LinkedIn. Out of these, at least 160million contained email addresses whereas 117million contained both email IDs and passwords’ information.
Leaked Source also reported that the hacker had already decrypted almost 90% of these passwords in no more than 72 hours.
Now the latest update is that the site has revealed the list of the most common passwords that were decrypted by the hacker. There are around 2.2 million listed passwords, which still only makes up around 2% of the total data hacked.
Some of the identifiable differences between the top-most common passwords in the hacked data and the list released to inform about the year 2012 data breach have also been included in the report from Leaked Sources. The top five terms used in the passwords, as per Rapid7 RPD, a cyber-security firm, are as follows:
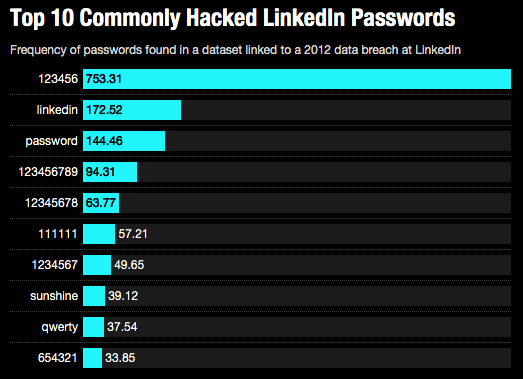
| PASSWORD | FREQUENCY |
|---|---|
| 0 | 32.49 |
| 111111 | 57.21 |
| 121212 | 17.13 |
| 123123 | 21.83 |
| 123456 | 753.31 |
| 1234567 | 49.65 |
| 12345678 | 63.77 |
| 123456789 | 94.31 |
| 1234567890 | 19.58 |
| 222222 | 16.17 |
| 555555 | 15.66 |
| 654321 | 33.85 |
| 666666 | 22.89 |
| abc123 | 30.40 |
| abcdef | 15.94 |
| bailey | 18.81 |
| baseball | 17.86 |
| buster | 18.40 |
| charlie | 28.05 |
| daniel | 19.18 |
| freedom | 15.79 |
| george | 16.62 |
| GINGER | 16.04 |
| hannah | 17.04 |
| harley | 16.27 |
| iloveyou | 20.25 |
| jessica | 16.09 |
| jordan | 15.84 |
| joshua | 15.63 |
| linked | 25.33 |
| 172.52 | |
| Linkedin1 | 19.44 |
| maggie | 23.89 |
| michael | 23.08 |
| michelle | 16.02 |
| monkey | 16.96 |
| Passw0rd | 18.21 |
| password | 144.46 |
| password1 | 30.98 |
| pepper | 15.61 |
| princess | 22.12 |
| qwerty | 37.54 |
| shadow | 17.78 |
| sophie | 15.88 |
| summer | 16.65 |
| sunshine | 39.12 |
| thomas | 16.79 |
| tigger | 15.66 |
| welcome | 18.50 |
But this analysis was conducted previously by Rapid 7 when the breach actually occurred. According to the latest on this issue by Leaked Source, the passwords were stolen by the hackers were encrypted and hashed using the SHA-1 cryptographic algorithm.
However, it has been identified that the passwords weren’t “salted” and thus, were so easily decrypted. Salted basically is a security measure that adds one buffer of randomness to the password and hence, makes it all the more difficult to decrypt.
In response, LinkedIn’s chief information security officer Cory Scott stated in a blog post that the company had already applied for salted encrypted many years back but the layer of protection was added only after 2012 data hack incident.
What we can tell you with surety is that the choices of passwords mentioned above are also quite poor and very weak in protecting your accounts online. If you want to protect your accounts from hacking then you must use a password manager to get complex and lengthy passwords.
Check the full infographic of the leaked passwords on Mashable
