A hacker who found critical vulnerability in Canadian Freedom Mobile has no downloaded the customer data and warned the company to put proper security measures.
A hacker using the alias NullHumanity claims that they have managed to identify a flaw in the customer login system of Freedom Mobile, a Canadian wireless telecommunications provider and claims to obtain private details of customers including their phone number, address, call history and other information effortlessly. The findings were reported by MobileSyrup.
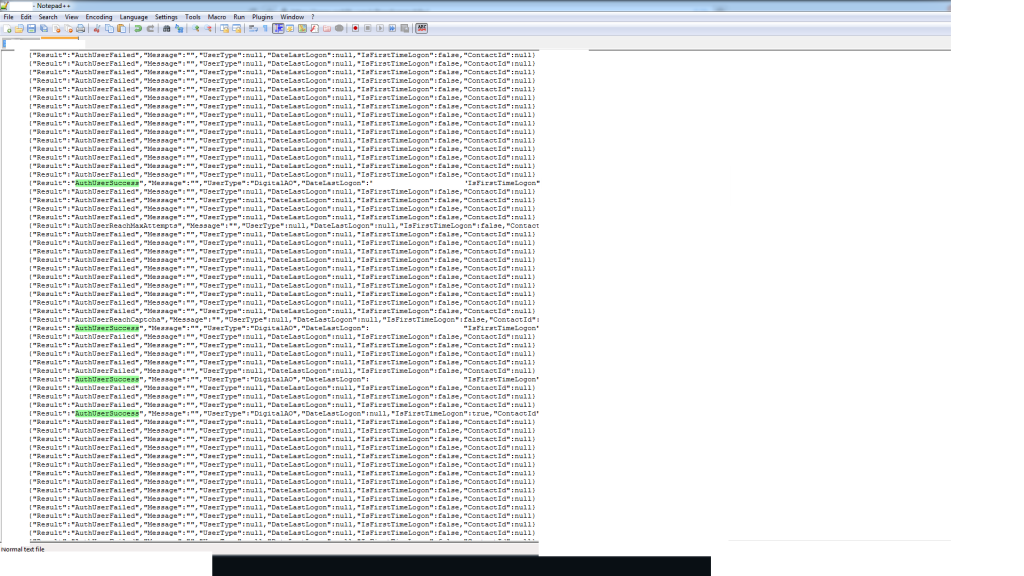
The hacker made claims on Freedom subreddit along with posting a screenshot of the code to prove successful brute forcing of Freedom Mobile’s user logins. The hacker further claimed that the customer login system has been “forced to the Phone Number/PIN model,” which cannot be modified by the support center of the carrier as well. This will make it easier to brute force customer logins because only 10,000 probably combos of PINs are there, which are quite easy to predict and numerous services are there for identifying carrier numbers, noted NullHumanity.
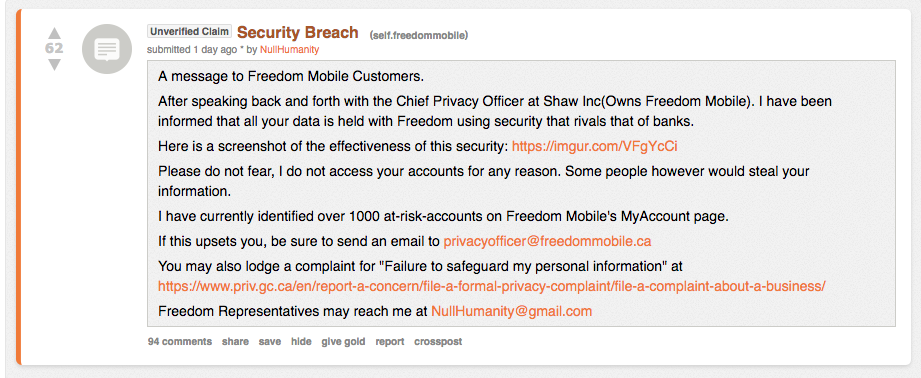
The hacker also stated that currently 2,000 at-risk accounts have been identified on Freedom Mobile’s MyAccount page but he does not intend to exploit them. “Please do not fear, I do not access your accounts for any reason. Some people, however, would steal your information. I have currently identified over 1000 at-risk-accounts on Freedom Mobile’s MyAccount page,” posted NullHumanity.
Furthermore, NullHumanity stated that they could possibly target up to 350,000 accounts considering the Freedom Mobile’s current number of subscribers. They also explained that if a hacker manages to access secondary API through guessing the phone number and PIN combination then he can expect to get sensitive details like date-of-birth, full name, phone number, email IDs, full call history and billing-related information.
Chethan Lakshman, the vice president of external affairs at Freedom Mobile, stated that: “The security measures we have in place cannot protect against guessing common passwords. We continue to strongly encourage our customers to use unique PIN numbers that are not easy to guess, and to change their PINs frequently to best protect their personal account information.”
Moreover, Lakshman stated that the company will review its security measures and will make necessary improvements or carry out modifications to ensure the security of its customers’ data. The security practices at the company have been designed to protect its customers’ data from all kinds of malicious operations and offers reliable login procedure. However, NullHumanity reported that the procedure is quite simple and not much secure as well.
“I wrote a script of 23 lines of code. Anyone with basic knowledge can do it,” wrote NullHumanity.
The issue was notified to Freedom Mobile by NullHumanity on 30th January but the company’s representatives rebuffed them citing that the 4-digit PIN numbers system is quite reliable as it is widely being used in the banking industry. However, NullHumanity claims that this method is not working for Telus, Bell, Rogers, Virgin, and Koodo, which were checked by the hacker after identifying the flaw in Freedom Mobile’s system.
Thus, on 5th February, NullHumanity reported the issue to the Office of the Privacy Commissioner of Canada (OPC). A representative of OPC stated that at the moment they cannot provide much information about this issue. NullHumanity recommends that whoever wants to enjoy the safe and secure experience at Freedom Mobile must create a unique and hard-to-identify PIN code.
Image credit: DepositPhotos
