We do know that stealing and selling private information of unsuspecting users is the favorite activity of cybercriminals. However, it is quite unlikely that someone manages to steal confidential military maintenance manuals and attempts to sell them on the Dark Web. That’s exactly what has happened.
According to security firm Recorded Future’s Insikt Group, a hacker exploited a pretty mundane FTP security flaw to obtain classified documents related to US military’s spy drones and tanks and was trying to sell the stolen files on the Deep Web and Dark Web forum last month for a meager amount of $150-200.
The hacker has stolen information about the MQ-9 Reaper drone, which is counted amongst the most advanced and lethal drones developed by the US having the ability to operate both remotely and autonomously. It is currently in use by NASA, DHS, CIA and the Pentagon – Reaper is used to carry out unmanned surveillance missions for security authorities, border control, and the military.
See: This is how hacked Israeli drone feeds look like
The hacking attempt was identified by the said group on June 1st and it was also learned that the hacker has registered his account on the Dark Web recently where he posted the screenshots of the files.

Further probe into the matter revealed that the stolen documents were authentic and were accessed by the hacker after exploiting a security flaw in a Netgear router installed at the Creech Air Force Base and infiltrating a Nevada based Air Force captain’s computer.
One of the on-sale documents revealed that the captain had recently finished a cyber-safety course in February, so it is quite surprising that he was unaware of the necessary data security practices to be followed to prevent unauthorized access.
Afterward, the hacker managed to successfully steal a cache of classified documents including maintenance books, training manuals, survival manuals, tank platoon tactics and listings of airmen from the Reaper maintenance unit of the base. The documents were posted later for sale on the Dark Web, each of which belonged to either an official from the Pentagon or the US Army.
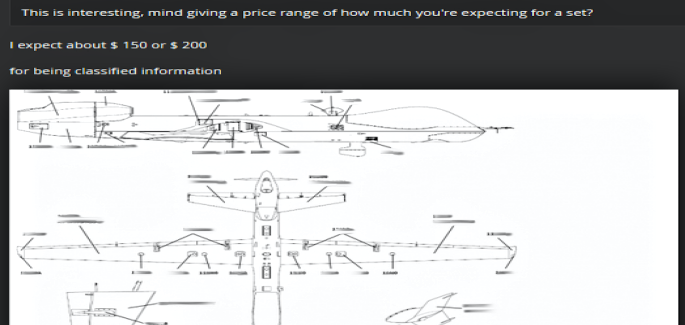
The course books, reports Recorded Future, although are not classified materials but can provide exclusive information about technical capabilities and vulnerabilities of some of the most “technologically advanced aircrafts” to malicious individuals. That’s a point to be concerned about.
See: Polar fitness app exposed location data of users in military & airbases
Recorded Future further revealed that the hacker, when contacted, bragged about how easily he managed to identify security flaws and carried out the data breach single-handedly. He also stated that he was skilled enough to exploit border surveillance cameras and airplanes to watch live streams of sensitive footages, which was his idea of personal entertainment.
It is also stated that two members of the US military, apart from the Nevada-based captain, are responsible for leaking the information because of connecting to vulnerable Netgear routers. The extent of the breach is not yet disclosed and the military is currently investigating the incident.
Image credit: Depositphotos
