DNS Queries Intercepted Due to Bogus DNS Traffic Protection Standards.
Would you believe that a majority of the DNS queries that are sent remain unprotected on the web? We would never have believed it but the fact is that DNS traffic interception is a reality and it is happening quite extensively. This issue has been brought to light by the US and Chinese universities researchers.
According to the latest research from China’s Tsinghua University’s research team and the University of Texas at Dallas a small but significant portion of the DNS queries, about 0.66%, sent over the TCP can be intercepted by threat actors. The research team comprised of Baojun Liu, Chaoyi Lu, Haixin Duan, and Ying Liu from China and Zhou Li and Shuang Hao from the US. The findings have been detailed in a paper titled “Who Is Answering My Queries: Understanding and Characterizing Interception of the DNS Resolution Path.”
Researchers examined residential and cellular IP addresses from across the globe for this research. They set up a full-fledged system to assess DNS interception. Around 148,748 IP addresses (both residential and cellular) were inspected.
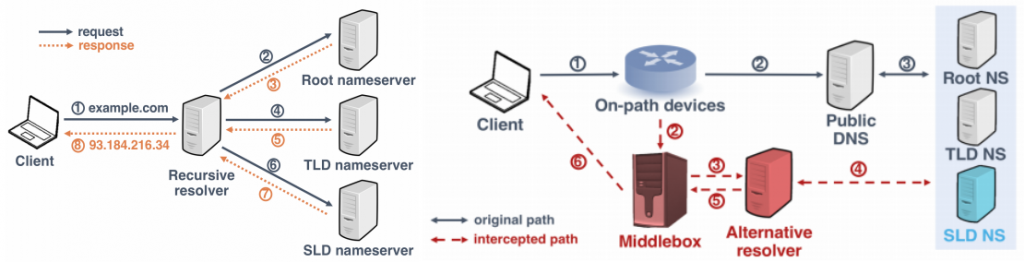
It is indeed concerning that DNS queries are insecure just because of the lackluster implementation and adoption of the proposed DNS traffic safeguarding standards. These include DNSSEC and DNS-over-HTTPS. It must be noted that DNS queries are used by software and browsers to resolve IP addresses and domain names.
The purpose of DNSSEC is to prevent tampering of intercepted domain name searches by miscreants. It performs this task by digitally signing the answers to these queries. If there is any forgery detected, it notifies the software. The same function is performed by DNS-over-TLS and DNS-over-HTTPS but their additional job is to encrypt the queries. This prevents malicious intruders from identifying the sites you are visiting.
See: Most Threatening DNS Security Risks And How To Avoid Them
However, it is reported that these safeguarding standards have not be adopted comprehensively. The DNS traffic is neither encrypted nor authenticated. This means the traffic can be easily spied on. Moreover, cybercriminals can use this glaring flaw to redirect unsuspecting users to infected, fake versions of legitimate websites. This interception may not lead to grave outcomes but can definitely prove to be detrimental to protecting user privacy.
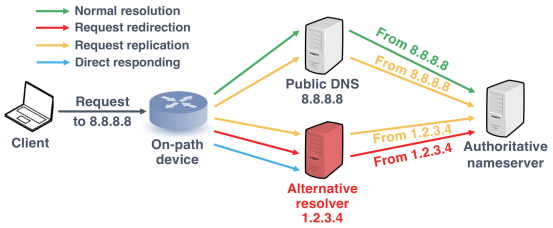
The problem is that even users aren’t much aware of the intricacies of DNS queries and end up getting exploited by cybercriminals. It is worth noting that web users can select their own DNS resolvers. This can be done by pointing their apps and OS manually at a specific DNS. For instance, you can easily point your applications to Google Public DNS (8.8.8.8) or Cloudflare (1.1.1.1). But, generally, people choose to accept whichever DNS resolver their ISP offers.
Researchers used registered domains to study the dynamics of unprotected DNS queries. They also searched for spoofed IP addresses of web users at specific DNS resolvers that secretly intercept DNS traffic. In 259 out of the 3,047 service providers, a DNS query interception was detected.
In this regard, about 27.9% of UDP-based packets for Google Public DNS were detected to be intercepted in comparison to the 7.3% of the TCP supported data transfer. While Chinese providers turned out to be the largest facilitators of this interception.
“We also discover 82 ASes are intercepting more than 90 percent of DNS traffic sent to Google Public DNS. As an example, 8 responses from Google Public DNS are tampered with in AS9808 (Guangdong Mobile), pointing to a web portal which promotes an APP of China Mobile” wrote the researchers.
According to Luke Brown, VP EMEA at WinMagic, DNS provides a critical service for Internet applications. Almost every Internet connection requires DNS queries, this research shows that the queries can be intercepted and used maliciously. Privacy is at risk as safeguarding standards, DNSSEC and DNS-over-HTTPS, have not been properly adopted.
See: Popular Chrome VPN extensions are leaking your DNS data
“DNS queries are used by everyone accessing the web via browsers, it is the process that turns www.XYZexample.com into an IP address. Personal privacy is in jeopardy as long as this data remains unencrypted. Cybercriminals that track users’ browsing habits will have access to private information, such as hobbies, interests and daily routines,” Brown said.
“In some cases, this could be used for blackmailing targets, and in all cases, it can be used for reconnaissance. This information could be useful to any criminal attempting to spear-phish their victims, as it provides targeted information that can be used to personalize attacks.”
“Encryption must be implemented in the initial design of all systems. As this report shows, encryption of personal data is still not a priority of many organizations. This is a problem that must be dealt with immediately. It may be the case that companies are not thinking about DNS queries as a potential attack vector. If this is true, how many other data-related processes are unprotected? Businesses need to be thinking about encrypting data at any point on the network, wherever it be in the cloud, data center or on an endpoint,” Brown explained.
