Digital hacking and learning about hacking has now become easier than you ever imagined, investigation report by the Digital Citizens Alliance reveals — Remote Access Trojan (RAT) Openly Available, Privacy Invasions at its Peak.
We all are aware of the fact that people have open access to the Internet, and anyone can find any piece of information, provided they know how and where to find it. Thus, hackers are openly tapping into the most lucrative and valuable resource i.e. the Internet, to publicize the privacy-invading tools.
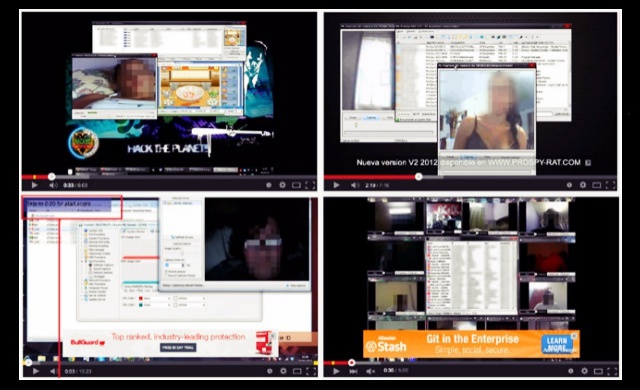
A non-profit advocacy group named Digital Citizen Alliance revealed that the Internet is filled with information related to hacking, everything is out there, openly available, and within easy access of the wannabe hackers.
The hackers are selling Remote Access Trojan (RAT) to the interested wannabe hackers, and believe it or not, most of the purchasers of these malware programs are youngsters and novice hackers. The malware and Trojans being provided by the hackers will allow anyone to take control of the targeted electronic device, eventually attacking the victim. The report calls them “ratters.”
The report also reveals that hackers are uploading malware programs and applications on websites that receives a lot of teenage users. Young Internet users are the easiest target of the hackers because their risk threshold is on the higher side and they are more prone to click on unacquainted websites and weblinks.
This is the reason why researchers have seen a sudden increase in the webcam videos of people who clicked unconsciously on a malware link and eventually opening their computer to the vulnerabilities and anonymous criminals who are determined to blackmail, mock and/or spy onto the victim’s personal life and data stored on their computer.
Remote Access Trojans are specifically targeted towards the most vulnerable audience i.e. young people, who usually feel embarrassed or frightened to share about the threats with their parents.
Surprisingly, there is not much being done to combat these disturbing privacy invasions. But the organization believes that individuals and corporations can take certain steps to fix this ever-increasing problem.
Facts about Remote Access Trojans (RATs)
The report reveals some unbelievable facts about malware. We have included it here:
- RATs are openly available.
- RATs are inexpensive tools and technically simple to use.
- Usage of RATs in one-on-one attacks against consumers has become a growing problem, confirmed by law enforcement firms.
- Devices infected with RAT are being openly sold by hackers, thus generating money from the malicious attacks on consumers.
- Devices destined for girls are sold at higher rates than the devices destined for boys.
- Websites like YouTube and other sites that provide unlicensed music and movies are the best platforms to spread RATs.
- Thousands of tutorials are openly available on YouTube, presenting how to use and spread RATs.
- About 40 percent of these RAT tutorials uploaded on YouTube have advertisements beside the videos. And hackers are generating money through the YouTube Partner Program.
What is Remote Access Trojan (RAT) and How Hackers Are Using It
Remote Access Trojan, widely known as RAT, is one of the six kinds of Trojan. It is the most popular and the simplest computer hacking tool available.
RATs are basically a malicious code that can be concealed within the photographs, documents, videos, and music too, as these are the easiest and simplest ways to trick the targeted audience into downloading the malware onto the computer.
The malicious software or application, in front of your screen, is just a simple code. But once it gets access into your computer, that simple piece of code will allow the hacker to perform all those tasks on your computer which you can perform, and that too without your consent.
All your content and data including your documents, pictures, videos, and any other personal information will be at the hacker’s fingertips.
Additionally, the hacker can use your computer system to victimize you, either by turning on the webcam to spy on you or by sending malicious emails to your contacts and what’s riskier is that the hacker can even launch a massive RAT attack using your computer to harm others.
“That computer is a window into your digital world. But what you may not realize is that computer is a window into your private life. The camera on your computer, when hacked, can become a tool to spy on you in your own home. And it’s easy.”
Adam Benson, Deputy Executive Director of the Digital Citizens Alliance said,
“Ratters are disturbingly comfortable with spreading misery and fear. It’s like a game for them. We saw them chat about it on Hack Forums and then share videos showing off how they scare young people, spy on people in private moments and steal pictures from victims’ accounts.”
Victim’s and Security Firm’s Response to RAT Malware
The Digital Citizen Alliance worked with California-based teen named Cassidy Wolf, a former Miss Teen USA and the victim of a ratter’s sextortion attempt, said that these cyber attackers and hackers should be treated just as harshly as those committing violent sex crimes in the offline world.
The security researchers worked with her because it is the best-known and one of the most high-profile stories that happened in 2013 about how RAT attacks can literally put one’s hopes and dreams at risk.
Her computer was compromised, the webcam was hacked, and all the data, personal social media accounts as well as some other information was also compromised. And she didn’t even know that her every action was being monitored and observed for several months!
One night, Miss Wolf received an anonymous email telling her “to do what I say or else I will post” the lots of pictures and videos.
According to the report:
The hacker would go onto threaten Cassidy, saying he wanted her to make a sexually explicit video. If she didn’t comply, he said he would transform her “dream of being a model . . . into a pornstar.”
Wolf said:
“A crime is a crime, whether it happens in the digital space or the physical world. These ratters don’t see the pain they cause. I went through three months of extortion and threats. There were times I thought it might go on for the rest of my life. The victims we see on ratter’s videos are real people. We need to inform people of this danger and get support from tech companies that can help stop the spread of RATs. RAT victims shouldn’t be reduced to click-bait.”
Hemanshu Nigam, a former federal prosecutor against online crimes at the US DOJ and a Chief Executive Officer of the cyber security company SSP Blue, said about these RAT attacks:
“We used to worry about protecting women and teen girls from the dangers of sexual predators in the physical world. Now we also need to protect them from digital rapists. Online rapists inflict pain and suffering repeatedly on innocent victims. We’ve got to prosecute these criminals and do everything we can to take away their platforms.”
YouTube and the RAT Problem
It has become really easy for anyone to find thousands and thousands of RAT related videos which include tutorials about the usage of RAT and how hackers can use various tools to infect the targeted computer with RAT malware.
On YouTube, you will be able to find:
- Tutorials on how to use RATs and tips on spreading malware to other devices.
- Examples of successfully deployed RATs, with the IP address as well as the real faces of victims.
- Links for ratters to download RATs they can use to slave devices.
To defend these acts and to help people in requesting the removal of non-consensual videos from the YouTube platform, an online mechanism by Google. The user can use the reporting form to flag and remove the content of the slaved computer systems. But originally this reporting system was launched to address revenge porn videos being uploaded on YouTube.
But in order to report these privacy invasions, the victimized people must need to know about it first. Despite the fact that there are thousands of videos on YouTube – most of which can easily be found by searching for a simple term “rat victims”, but the victims are not even aware that their computers slave and their secret videos are being released publicly.
One of the YouTube spokespeople told in an email statement that every minute there are about 400 hours of videos are uploaded which makes it next to impossible to watch and verify the content. But he also said, “ has clear policies that outline what content is acceptable to post, and we remove videos violating these policies when flagged by our users.”
He also added any user is free to flag a video for a review by the team, and if the matter is serious then YouTube policies allow them to remove those videos.
How You Can Protect Your Privacy
As a precautionary measure, Mr. Benson recommends every computer user to “tape” their webcam. At least that is exactly what he does when he is not using the webcam. “I have tape on both my work computer and home computer,” he said. He also advised that people should keep their computer’s antivirus software and operating system up to date, and refrain from clicking on the web links leading to ambiguous destinations.
RATs are so powerful malware tool that it can affect the victim in less visual but equally disturbing ways because it grants hackers complete access to the computer, and the computer cannot be safeguarded just by installing antimalware and antivirus applications.
Even the professionals who are aware of the malware and the risks involved, cannot completely protect themselves from such harmful malware.
Did you enjoy reading this article? Kindly do like our page on Facebook and follow us on Twitter.
