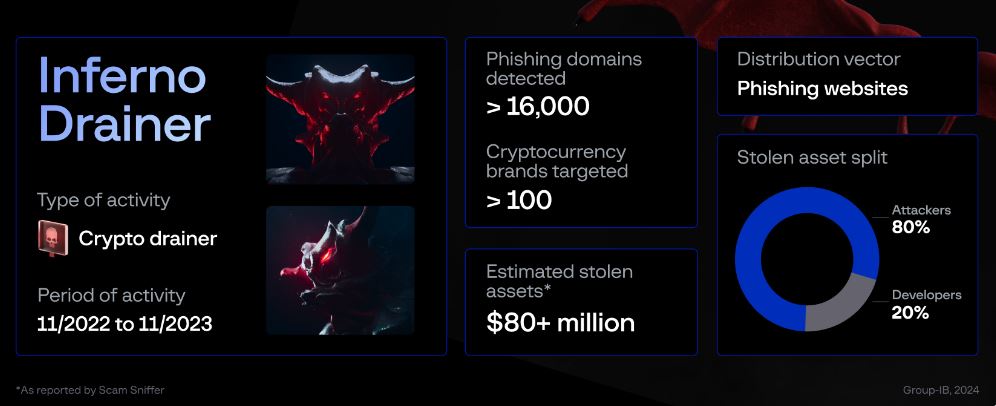
Group-IB Global Pvt. Ltd. has revealed shocking details on Inferno Drainer, a phishing operation targeting cryptocurrency wallet providers. The scam, involving the deployment of a multichain crypto drainer, operated under a scam-as-a-service model, targeted over 100 brands and 16,000 malicious domains, stealing over $80 million in digital assets from November 2022 to November 2023. It ceased operating in November 2023 after causing significant financial damage.
The Inferno Drainer team is “estimated to have reaped over $87 million in illicit profits by scamming over 137,000 victims,” Group-IB’s blog post read.
Researchers discovered over 14,000 phishing websites with malicious scripts impersonating Seaport, WalletConnect, and Coinbase protocols, with over 5,500 spoofed and 550 scripted. The scammers’ Telegram channel description only mentions @Mr_inferno_Drainer, supposedly its developer and tech support provider, whereas the team’s first public mention was on the day the channel was created, on November 5, 2022.
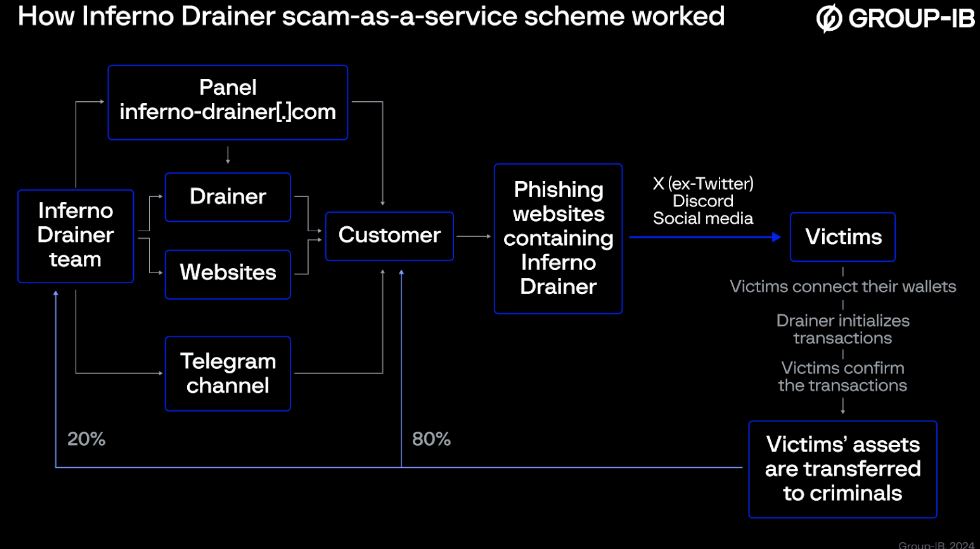
Inferno Drainer team used high-quality phishing pages to lure unsuspecting users to their websites. They targeted victims via social media platforms like X, Telegram, and Discord, offering free tokens called airdrops and rewards for minting nonfungible tokens. Google-owned Mandiant’s X account was also compromised, distributing links to a phishing page hosting a cryptocurrency drainer called CLINKSINK.
Group-IB analyzed 500 domains and found a JavaScript-based drainer hosted by a user “kuzdaz” on a GitHub repository. Another set of 350 sites was found on a different repository.
These sites lured victims to connect their wallets for potential riches while the malicious scripts were designed to complete unauthorized transactions. The scam operators claimed a flat rate of 20% of stolen assets, while affiliates retained 80% of their gains. They spoofed Web3 protocols (including Seaport, WalletConnect, and Coinbase) under DApps to initiate malicious transactions.
For affiliates, it offered a customer panel to customize malware features and detailed statistics, including the number of victims connecting to their wallets on each phishing website, the number of confirmed transactions, and the stolen assets’ value.
Group-IB’s High-Tech Crime Investigation Department’s Andrey Kolmakov stated that despite the group’s claim to shut down its operations in November, this control panel remained active throughout December, allowing other hackers to exploit the situation.
“Inferno Drainer may have ceased its activity, but its prominence throughout 2023 highlights the severe risks to cryptocurrency holders as drainers continue to develop further,” Kolmakov noted.
RELATED ARTICLES
- Scammers Selling Twitter (X) Gold Accounts Fueling Disinfo, Phishing
- Multilingual malware hits Android devices for phishing & cryptomining
- Hacker stole $55M worth of crypto from DeFi lender bZx via phishing
- Hackers Aim at Crypto Wallets with Hacked Namecheap Phishing Emails
- Cryptocurrency losses reach $1.75 Billion in 2023; CeFi and Hacks Blamed