Browsing Category
Phishing Scam
289 posts
9 Years Jail for iCloud Phishing Scam Hacker Who Stole Nude Photos
The hacker was arrested in 2021 for breaching Apple iCloud accounts and stealing more than 620,000 private images…
June 20, 2022
Cybercrime Syndicate Leader Behind Phishing and BEC Scams Arrested in Nigeria
Cyber security companies across the globe helped Interpol bust an unnamed cybercriminal being large-scale BEC scams and phishing…
May 26, 2022
How to detect phishing images in emails
Phishing has long been a common way to induce a receiver to unveil personal data. Primarily, it works…
April 27, 2022
MetaMask Asks Apple Users to Disable iCloud Backup for Wallet After User Lost $650,000
MetaMask has warned Apple users to disable automatic iCloud backup of their wallet data. The warning results from…
April 19, 2022
Phishing scam: NFTs Worth $1.7M Stolen from OpenSea Users
OpenSea’s CEO Devin Finzer has denied the claims that a vulnerability in their smart contract was exploited to…
February 21, 2022
Hacker stole $55M worth of crypto from DeFi lender bZx via phishing
The hack took place after one of the bZx’s employees was sent a phishing email embedded with a malicious macro hidden in an MS word document.
November 8, 2021
Google details cookie stealer malware campaign targeting YouTubers
Google attributed the malware campaign to a group of attackers recruited via a Russian-language hacker forum.
October 22, 2021
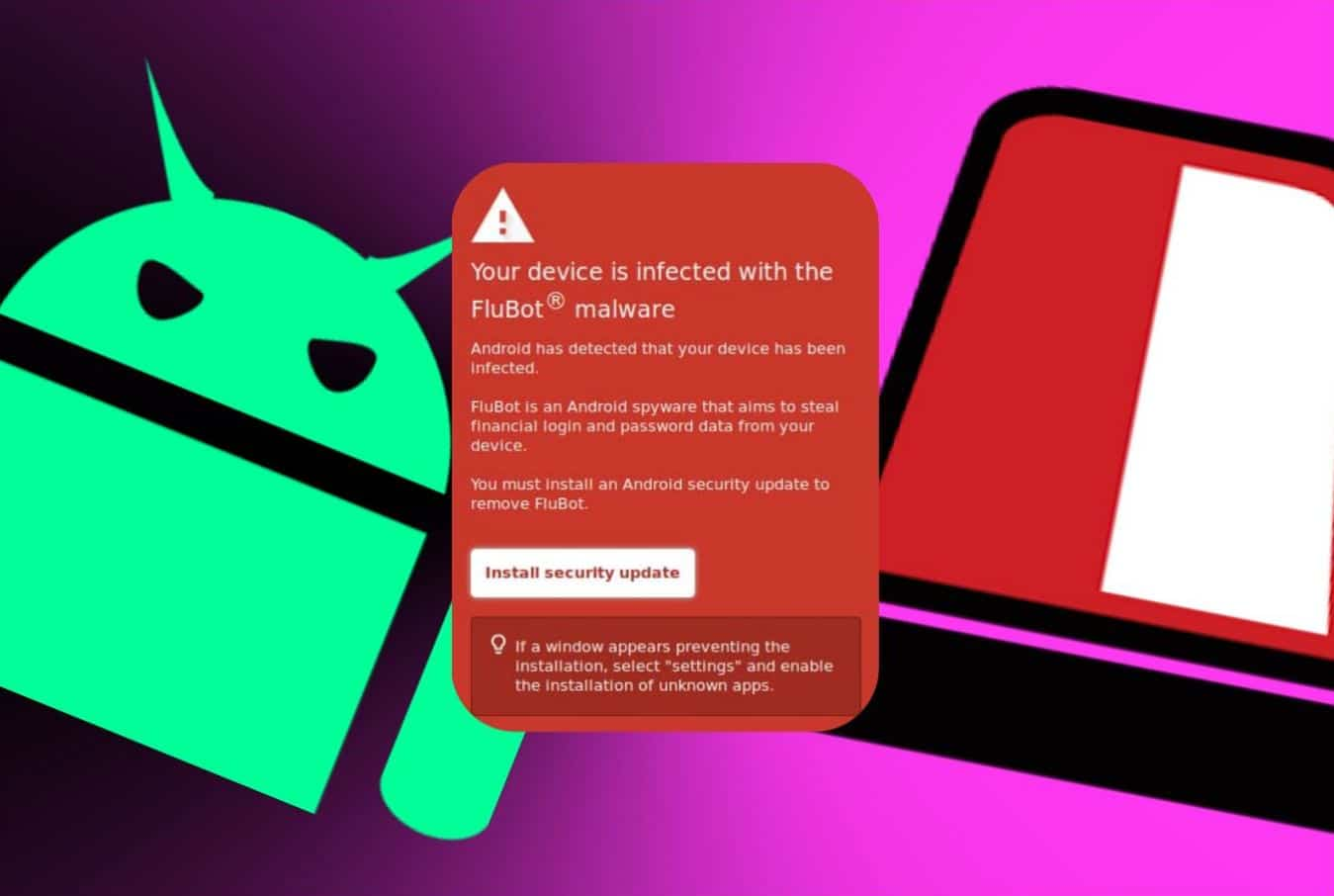
Android flubot malware installs itself by faking security update
The warning is obviously phony but looks authentic that can deceive users into installing Flubot malware on their devices.
October 2, 2021
Telegram Bots Stealing One-Time Passwords
So far two Telegram bots called SMSRanger and BloodOTPbot have been found taking part in this malicious campaign.
September 29, 2021
TA544 threat actors hit Italian firms with Ursnif banking trojan
A new malware campaign from a group called TA544 is targeting organizations in Italy with Ursnif banking trojan - Here's how it works.
September 29, 2021