A new malware threat named Latrodectus has emerged, bypassing detection methods and linked to the developers behind IcedID. This downloader malware empowers cybercriminals (including infamous actors like TA577 and TA588) to breach systems and deploy various malicious payloads.
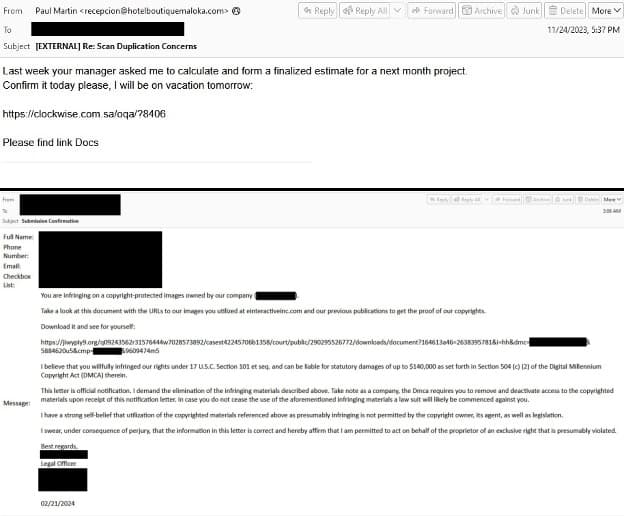
Cybersecurity researchers at Proofpoint have identified a new malware threat dubbed “Latrodectus.” First observed in November 2023, Latrodectus is a downloader malware used by cybercriminals to gain initial access to victim systems and deploy further malicious payloads.
This malware poses a major threat due to its ability to evade detection techniques commonly employed in sandboxes, which are security environments used to analyze suspicious code.
Latrodectus: A New Player with Familiar Traits
Initial analysis suggested Latrodectus might be a variant of the notorious IcedID malware. However, further investigation revealed it to be an entirely new strain, likely created by the same developers behind IcedID. This connection is supported by shared infrastructure and code characteristics.
Initial Access Brokers Leverage Latrodectus
Proofpoint report shared with Hackread.com on Thursday 04, 2024 ahead of publication on Tuesday attributes Latrodectus to two specific threat actors: TA577 and TA578. It is worth mentioning that TA578 is known for delivering malware threats like BazaLoader, Cobalt Strike, Ursnif, and KPOT Stealer.
On the other hand, TA577 is infamous for having served as a key affiliate of the Qbot network until its recent disruption. TA577 has been linked by Proofpoint to various campaigns, with subsequent ransomware infections such as Black Basta being notably attributed to them.
These actors are classified as Initial Access Brokers (IABs), specializing in gaining initial footholds within victim networks. Latrodectus serves as their tool to establish a foothold and potentially deploy ransomware or other malicious tools.
Commenting on this, Ken Dunham, Cyber Threat Director at Qualys Threat Research Unit told Hackread.com, “Battling eCrime is similar to moving a couch where roaches live, they simply run to another piece of furniture or room nearby to seek harbour and continue business as normal, despite any actions taken by the homeowner.“
“Latrodectus has powerful components upon its emergence, capable of defeating sandboxes, use of RC4 encrypted command and control communications, and more,“ Ken warned. “It appears likely that actors behind QBot felt the heat from takedowns last year, migrating to this new code base and infrastructure in the fall of 2023.“
While Latrodectus activity dropped in December 2023 and January 2024, Proofpoint reports a surge in campaigns throughout February and March 2024. This suggests a growing adoption of Latrodectus by cybercriminals.
The specific payloads delivered by Latrodectus remain unknown, but its downloader functionality allows attackers to deploy a wide range of tools through malicious emails depending on their objectives.
While technical details of Latrodectus’s modus operandi are available in Proofpoint’s blog post, here are some to mitigate the risk of Latrodectus:
- Maintain strong cybersecurity hygiene: Regularly update software and firmware on all devices. Utilize robust security solutions with advanced malware detection capabilities.
- Be cautious of suspicious emails: Phishing emails are a common method for distributing malware. Be wary of unsolicited attachments and links.
- Educate employees: Train employees on cybersecurity best practices, including email security awareness and the importance of reporting suspicious activity.