In BazaCall, a “vishing-like” method is used in which victims receive email messages notifying them that subscription fees apply or their subscription will expire if they don’t call a particular phone number.
A new campaign was identified in which fake call centers are tricking victims into downloading malware, performing data exfiltration, and deploying ransomware on the affected machine. The attack is called BazaCall.
This new campaign was discovered and reported by Microsoft 365 Defender Threat Intelligence Team. The researchers noted that BazaCall attacks could quickly spread within a network and carry out extensive credential and data theft. It can also distribute ransomware within just 48 hours of the compromise.
SEE: Microsoft patent reveals chatbot to talk to dead people
This campaign seems to be inspired by the trend where BazaLoader-associated criminals use call centers, mainly where non-native English speakers are employed, in their intricate attack chain.
How BazaCall Traps Victims?
It shuns the traditional social engineering practices that we have become accustomed to, such as where rogue URLs or infected documents are used to unleash the malware.
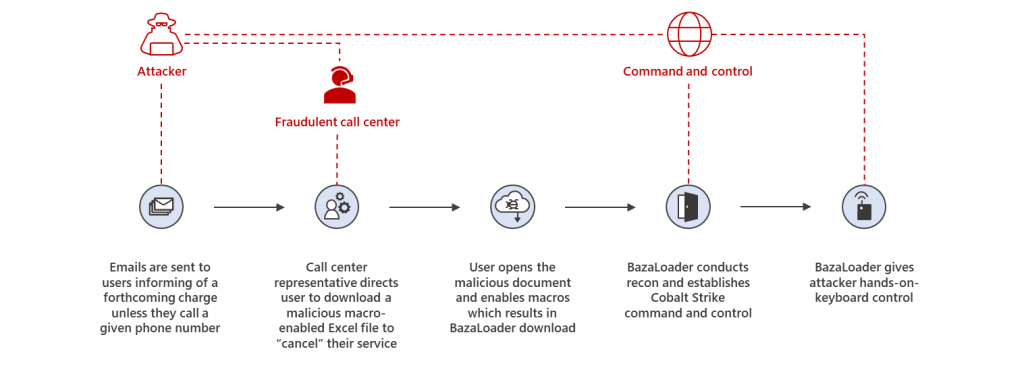
In BazaCall, a “vishing-like” method is used. In this attack, victims receive email messages notifying them that subscription fees apply or their subscription will expire if they don’t call a particular phone number.
In a blog post, researchers at Microsoft 365 Defender Threat Intelligence Team wrote that,
“Each wave of emails in the campaign uses a different “theme” of subscription that is supposed to be expiring, such as a photo editing service or a cooking and recipes website membership. In a more recent campaign, the email does away with the subscription trial angle and instead poses as a confirmation receipt for a purchased software license.”
When the victim calls that number, they are linked with an employee at the fake call center who instructs them to visit a genuine-looking website. The victim has to download a file from their account page to cancel the subscription. After the macros are enabled on the downloaded documents, the BazaLoader malware is delivered from a Cobalt Strike beacon.
What is BazaLoader
Also known as BazarBackdoor, BazaLoader is a downloader based on C++. Palo Alto Networks first discovered the malware in March 2021. It can install different types of malicious software on infected machines, including ransomware and data-stealing malware.
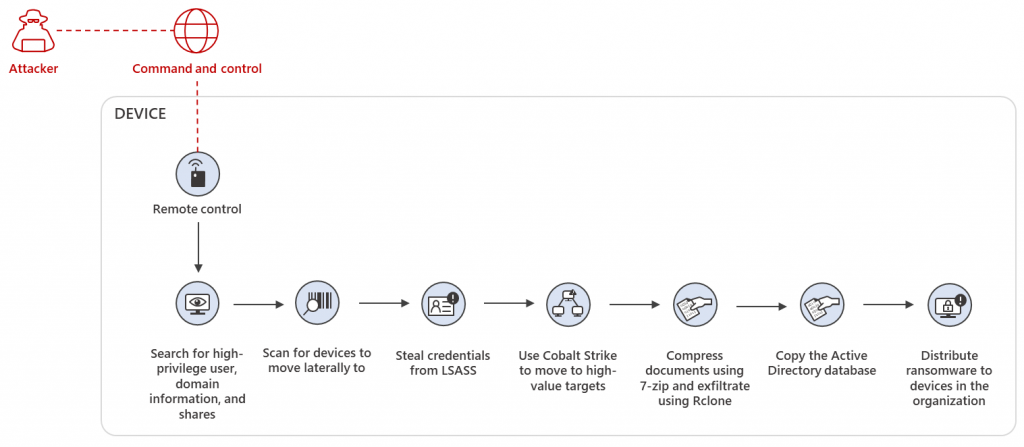
Reportedly, multiple threat actors have used the backdoor in campaigns since April 2020, research suggests, and it frequently serves as a loader for devastating threats like Ryuk or Conti ransomware.
Since the malware isn’t distributed through a malicious document or URL within the email body, it becomes pretty difficult to detect the threat, and attackers can successfully evade malware detection software.
“BazaCall campaigns highlight the importance of cross-domain optics and the ability to correlate events in building a comprehensive defense against complex threats,” researchers concluded.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
