KEY FINDINGS
- An aerospace firm in Spain is the target of an organized attack where scammers contact the company’s employees as recruiters from LinkedIn.
- The activity is attributed to Lazarus as part of its Operation DreamJob campaign.
- The targets are lured into opening a file masqueraded as a coding challenge/quiz, but it is a malicious executable.
- Attackers have used DLL side-loading to deliver payloads and employed four execution chains.
- LightlessCan backdoor is the highlight of this attack, as it can evade detection from real-time security monitoring software and even scrutiny from cybersecurity experts.
- LightlessCan is the predecessor of Lazarus’ signature RAT BlindingCan.
ESET Research has published a report describing a newly detected cyberespionage campaign from the Lazarus group. The report, authored by Peter Kálnai, revealed that Lazarus APT is exploiting the professional social networking platform LinkedIn in this campaign, which ESET believes is a part of the group’s Operation DreamJob.
Reportedly, the attackers are luring employees of a Spanish aerospace firm by impersonating recruiters from LinkedIn. Their targets are company employees using corporate computers for personal purposes. ESET’s primary discovery was that Lazarus used a previously undocumented backdoor in this campaign, dubbed LightlessCan.
It is noteworthy that since 2019, the Lazarus Group has displayed significant interest in the space industry. In November 2019, the group targeted the Indian space agency, coinciding with the country’s Chandrayaan-2 moon landing attempt.
The use of LinkedIn to target large firms is not new for the North Korea-based Lazarus group. In July 2022, it was revealed that the group used fake LinkedIn job offers to steal $625 million from the Ronin Network (RON), a blockchain network that underpins the popular crypto game Axie Infinity and Axie DAO.
Further probing into this new LightlessCan revealed that it is currently in its evolutionary phase and is a complex tool exhibiting highly sophisticated mechanisms in its design and operation. This indicates that threat actors continually advance their attack tactics and tools since LightlessCan is much more malicious than its predecessor, BlindingCan.
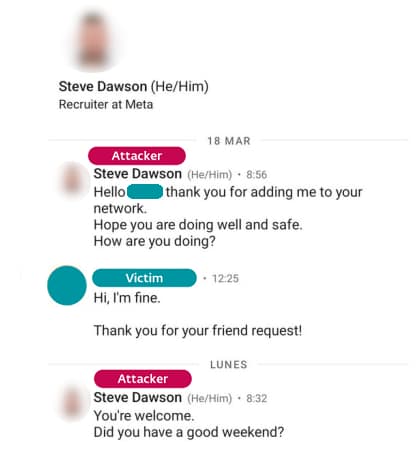
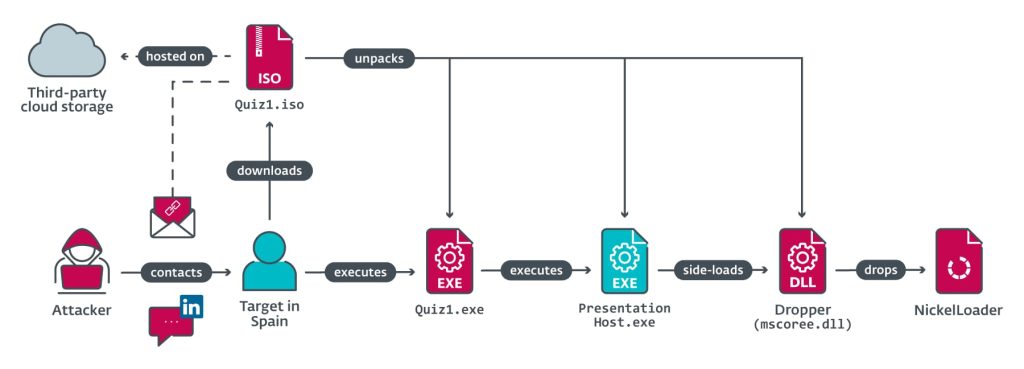
Initial access to the company’s network was achieved in 2022 through a spearphishing attack where the attackers masqueraded as Meta recruiters. They contacted the employees through the LinkedIn Messaging feature. The victim receives two coding challenges to complete the hiring process. This challenge has to be downloaded and executed on a company computer.
The first challenge is to display the phrase “Hello World!” The second challenge is printing a Fibonacci sequence where each number is the sum of the earlier two numbers. The victim is expected to self-compromise the system by luring them into executing a trojanized PDF viewer to view the job offer or connect with a trojanized SSL/VPN client that comes with an IP address and login credentials.
According to ESET, Multiple employees were targeted with this technique. The targets are requested to prove their proficiency in C++ programming by completing the challenge/quiz. The recruiter sends two executables titled Quiz1.exe and Quiz2.exe. These executables are delivered via two image files (Quiz1.iso and Quiz2.iso). These files are hosted on a third-party cloud storage platform and are basic command-line applications requiring user input.
During the final stages of the attack chain, the attacker infects the system with an HTTP(S) downloader, NickelLoader to deploy any program into the infected system’s memory.
Through NickelLoader, they deliver two RATs, the Lazarus’ flagship toolkit BlindingCan backdoor’s simplified version miniBlindingCan and the new tool ESET named LightlessCan. This is BlindingCan’s successor that supports up to 68 different commands and is indexed in a custom function table.
There are two versions of LightlessCan detected by ESET. The current version (1.0) supports only 48 commands with limited functionality. It is based on BlindingCan source code with certain indexing changes.
This new toolkit can mimic the functions of several native Windows commands, e.g. ping, ipconfig, systeminfo, sc, net, enable discreet execution within the RAT, and feature enhanced stealthiness that makes detecting/analyzing it a huge challenge.
Victor Acin, KrakenLabs Manager at Outpost24 commented on the issue and told Hackread.com that “As companies increase their cybersecurity capabilities, modernize their infrastructure, and consolidate their technology, it becomes more and more difficult to exploit vulnerabilities in the traditional way. This, as well as finding faults within the application logic and its programming that allow an attacker to gain access to that server, makes zero-days rare.”
Acin added “It’s not a surprise that threat actors resort to attacks that target the weakest component of the link – the user behind the screen. Social engineering attacks are the most common way to gain access to companies, and with the abundance of data about the employees from sources such as social media to leaks containing PII, it becomes simpler every day to put together a credible target package.”
For your information, Lazarus, aka Hidden Cobra, is a cyberespionage group from North Korea. It was first detected in 2009 and has successfully conducted several high-profile incidents, including the Sony Pictures Entertainment hack (2016) and the WanaCryptor aka WannaCry attack (2017).
Aerospace firms aren’t unusual targets for North Korea-sponsored APT groups like Lazarus as they want to access sensitive technology and gain money from cyberattacks to further the development of North Korea’s missiles.
RELATED ARTICLES
- North Korean Hackers Targeting Banks Globally: Report
- South Korea Blames North Korean Hackers For Stealing Bitcoin
- Hackers steal personal details of 1,000 North Korean Defectors
- South Korean subway system hacked, North Korea a possible culprit
- Elite North Koreans aren’t opposed to exploiting internet for financial gain