Microsoft threat hunters discovered a new phishing campaign launched by a North Korean government-backed hacking group involving the use of weaponized open-source software. The malware is laced with extensive capabilities, including data theft, spying, network disruption, and financial gains.
Well-known Software Used in Phishing Campaign
In the new campaign, hackers are weaponizing famous open-source software, and their primary targets are organizations in the aerospace, media, IT services, and defense sectors.
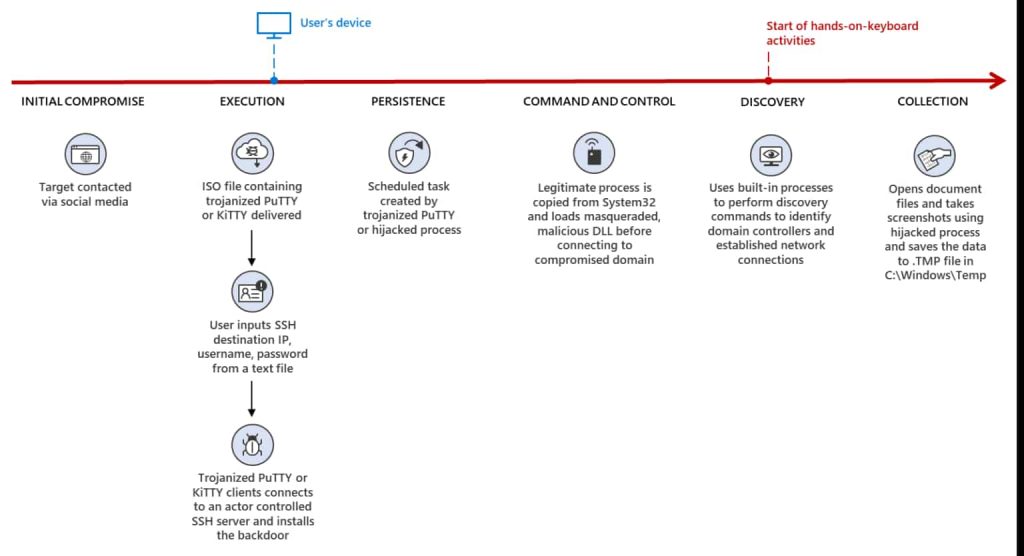
In its report published on Thursday, Microsoft stated that the hackers are a sub-division of the notorious Lazarus hacking group called ZINC. This group has injected encrypted code in several open-source apps, including KiTTY, Sumatra PDF Reader, PuTTY, and muPDF/Subliminal Recording software installers, eventually leading to espionage malware being installed as ZetaNile.
For your information, ZINC is the same group that successfully conducted the highly destructive Sony Pictures Entertainment compromise in 2014.
LinkedIn Abused to Lure Targets
The researchers have referred to the attackers as highly dangerous, operational, and sophisticated nation-state actors abusing the LinkedIn networking portal to hunt for targets. The crooks use the network to connect and befriend employees of their selected organizations. Their targets are based in India, Russia, the UK, and the USA.
The campaign started in June 2022, whereby ZINC used conventional social engineering tactics to search and connect with individuals and gain their trust before switching the conversation to WhatsApp. Once this is achieved, they deliver the malicious payloads.
LinkedIn’s threat prevention and defense team confirmed detecting fake profiles created by North Korean actors impersonating recruiters working at prominent media, defense, and tech firms. They want to lure targets away from LinkedIn and move them to WhatsApp.
It is worth noting that LinkedIn is owned by Microsoft Corporation since 2016.

Attach Methodology Explained
According to a joint blog post by Microsoft Security Threat Intelligence and LinkedIn Threat Prevention and Defense, the trojanized KiTTY and PuTTY apps use an intelligent tactic to ensure that only selected targets are infected with malware and not others.
To achieve this, the app installers don’t execute malicious code. The malware is installed only when the apps connect to a particular IP address and use login credentials given to the targets by fake recruiters.
The threat actors also use DLL search order hijacking to load and decrypt a second-stage payload when this key 0CE1241A44557AA438F27BC6D4ACA246 is presented for command and control.
Additional malware is installed when the connection is established with the C2 server. Both apps work in the same manner. Similarly, TightVNC Viewer installs the final payload after the user selects ec2-aet-tech.w-adaamazonaws from a dropdown menu of remote hosts in the app.
Microsoft is urging the cybersecurity community to pay attention to this threat, given its extensive usage and use of legit software products. Moreover, it threatens users and organizations across multiple regions and sectors.