It is no secret that the US government has always suspected and even accused North Korea was carrying out ransomware attacks using the destructive WannaCry ransomware and for hacking Sony Pictures. But it merely has remained a suspicion so far. However, now the US authorities have found solid evidence of the involvement of North Korean behind major hack attacks in the US and the rest of the world and the country has been accused formally for its wrongdoings.
In a 179-page long affidavit submitted by the special agent supervising the investigations, it is revealed that the US government has formally declared North Korean government as the sole perpetrator behind many devastating hack attacks involving the use of WannaCry ransomware. These include the hack attack on Sony Pictures, Bangladesh’s national bank where $81 million was stolen, ransomware attack on the NHS (National Health Service) of UK, and attacks on many other banks and organizations. The information was revealed to the public at a press conference by the US Department of Justice and the Federal Bureau of Investigation on Thursday.
https://twitter.com/MalwareTechBlog/status/1037866475426467840
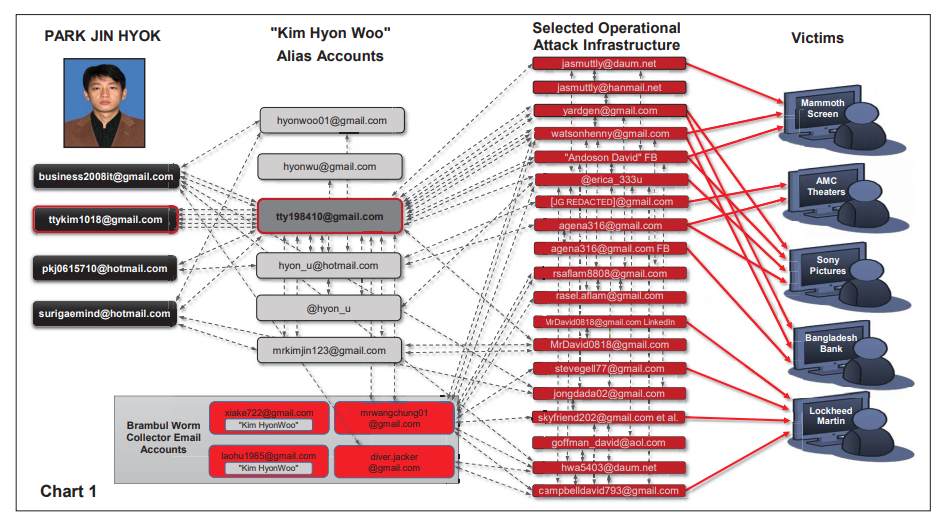
Reportedly, many of the major cyber attacks involving renowned organizations like Sony Pictures were carried out by a group of hackers from North Korea called Lazarus. The group launched attacks with the backing of the North Korean government, and apparently, the hackers worked for a firm called Chosun Expo Joint Venture.
One of the members of the Lazarus Group of hackers had been named by the authorities. The accused, Park Jin Hyok now appears on the Most Wanted poster of the FBI and is now declared a fugitive from justice. It is also reported that the US will now be imposing additional sanctions against North Korea.
The affidavit provides glaring details about the way the group used Gmail accounts and tried to cover their tracks at length. Despite all their efforts, they did leave some traces behind that led the US authorities to track them. Such as, one of the email accounts that the hackers used belonged to the North Korean government official, which hinted at the fact that the government did play a key role in facilitating the hackers.
Here, it must be noted that a large number of entertainment groups, financial institutions, and organizations were attacked and the same code was used to design the notorious WannaCry ransomware that created havoc at a global scale. According to the Assistant Attorney General for National Security, John Demers:
“The scale and scope of the cyber-crimes alleged by the complaint are staggering and offensive to all who respect the rule of law and the cyber norms accepted by responsible nations.”
The hackers used same IP addresses, devices, and encryption keys to launch attacks while the domain names were hard-coded into the malware that was being controlled by the hackers. One of the domains used was named fancug.com. Investigators also identified that the hackers firstly targeted companies and tracked individuals through their social media accounts. Park Jin Hyok visited China frequently for conducting legal computer work and returned to North Korea to carry out hack attacks for the government.
The accused is currently present in North Korea and the US authorities believe that they cannot capture him from there as the country doesn’t share an extradition treaty with North Korea. But, the DoJ claims that it is one thing to name the group and another to capture them. The purpose of officially filing a complaint is to make North Korea aware that their secret is out.