Cofense cybersecurity researchers have noticed a sudden uptick in phishing messages sent via LinkedIn, as they observed around 800 emails sent between July and August 2023.
KEY FINDINGS
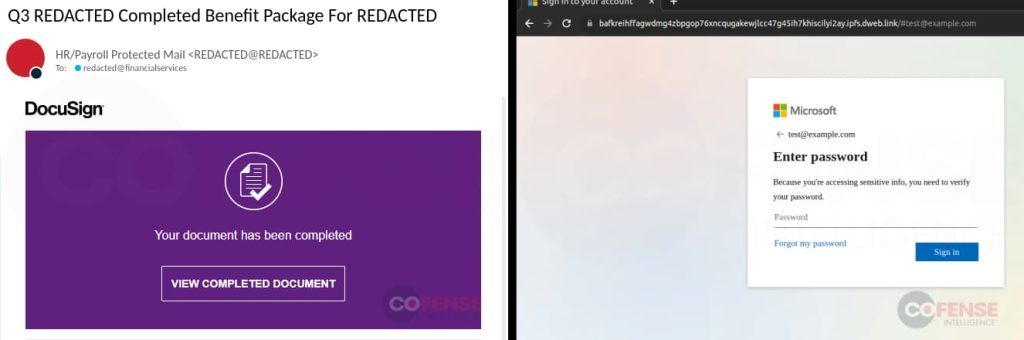
- A new LinkedIn phishing scam targets users to steal their Microsoft account login credentials.
- Phishing actors are exploiting LinkedIn’s Smart Link feature to evade email security mechanisms and redirect users to phishing pages designed to steal financial data.
- The Smart Links feature is part of LinkedIn Sales Navigator and Enterprise and allows users to send up to 15 documents with a single trackable link.
- Phishing actors are interested in exploiting Smart Links to make their phishing emails seem legitimate and appear to be sent by a trusted source apart from bypassing email protections.
- This campaign targets diverse industries, but the most prominent targets are the finance and manufacturing sectors.
If you use LinkedIn to connect with your colleagues or industry experts, then you should feel alert because, in the newly discovered phishing campaign, threat actors are abusing a legitimate feature of LinkedIn to send authentic-looking phishing emails.
According to a report from email security firm Cofense, the feature exploited in this campaign is Smart Links, part of the LinkedIn Sales Navigator and Enterprise service. Phishers are abusing it to steal payment data. They exploit Smart Links to bypass email protection mechanisms and deliver malicious lures into the email inboxes of Microsoft users. Cofense
Cofense cybersecurity researchers have noticed a sudden uptick in phishing messages sent via LinkedIn, as they observed around 800 emails sent between July and August 2023. These emails were sent through 80 unique Smart Links and mostly lured users with payments, essential documents, security notifications, or recruitment-related messages.
According to Cofense’s blog post, all the messages contained an embedded link/button to redirect the victim to a malicious website where the attackers compel them to give away personal/financial data or login credentials.
The report’s author, Cofense cyber threat intelligence analyst Nathaniel Raymond, noted that this campaign most probably exploits newly created or compromised business accounts on LinkedIn to deliver malicious lures and forces users to provide their Microsoft account details.
For your information, this feature allows businesses to promote ads or websites and redirect users to their desired domains. This tool lets business account holders contact LinkedIn users via trackable ‘smart’ links. The sender can track who interacted with their messages and in what manner. Therefore, this tool is ideal for pitch testing and enhancing the process.
The smart link includes the LinkedIn domain with a parameter and an eight-alphanumeric character ID. However, adversaries have added new information, such as the recipient’s email ID, to autofill the phishing page the victim gets redirected to.
Employees at a wide range of organizations are targeted in this campaign, including manufacturing, financial, energy, construction, insurance, health, mining, consumer goods, and technology. But manufacturing and financial organizations were the top targets.
“Despite finance and manufacturing having higher volumes, it can be concluded that this campaign was not a direct attack on any one business or sector but a blanket attack to collect as many credentials as possible using LinkedIn business accounts and smart links to carry out the attack.”
Nathaniel Raymond – Cofense
To protect yourself against malicious phishing links, you must be wary of emails from unknown users, even if the email came from an authentic source or domain. Only click on links embedded in the email if you believe the email is legit, and if you are unsure, a good idea is to contact the sender directly to verify it. Use a reliable password manager to create unique passwords for online accounts and enable 2FA on all of them.
RELATED NEWS
- New LinkedIn phishing campaign found using Google Forms
- Fake LinkedIn job offers scam spreading More_eggs backdoor
- Iranian Hackers Posed as Israelis in Targeted LinkedIn Phishing Attack
- Ducktail Malware Exploits LinkedIn to Hack Facebook Business Accounts
- Hackers Used Fake LinkedIn Job Offer to Hack Off $625M from Axie Infinity
