Trend Micro researchers have identified malicious Google Chrome and Microsoft Edge browser extension that is distributing backdoor to steal information from the browser as well as a spy upon the user.
According to researchers, there are two payloads involved in the ‘series of testing submissions in VirusTotal’. The submission sources and filenames hint upon the fact that these payloads are believed to be distributed by a group of malware authors from Moldova.
More: These Chrome extensions & Android apps collect your Facebook data
The downloader responsible for delivering the malware payloads based on Java and NodeJS (TROJ_SPYSIVIT.A and JAVA_ SPYSIVIT.A) contains VisIT RAT (remote administration tool) and a backdoor extension. Collectively these manage to hijack the infected device meanwhile downloader executes the JavaScript file, which is packed with ZIP archive.
The backdoor and RAT are being delivered through spam emails embedded in malicious attachments, as assessed by Trend Micro after analyzing the way malicious payload has been coded. Trend Micro has detected the malware as JS_DLOADR and W2KM_DLOADR. The downloader delivers a version of remote administration tool called VisIT to hijack the infected device and also delivers a malicious extension to serve as Backdoor.
NodeJS payload contains various files; when the macro is enabled it executes node.exe and installs the .js file that contains installation script to assess admin rights and the groups. The second step is the execution of install.vbs to acquire escalated privileges and to add new firewall rules to facilitate traffic to the RAT. Persistence is established via adding ‘shortcut (LNK) files in the Startup folder’ wrote Trend Micro researchers. Install_do.js also installs an extension to the browser extension directory of the system to create the timestamp.dat file.
More: Popular Chrome VPN extensions are leaking your DNS data
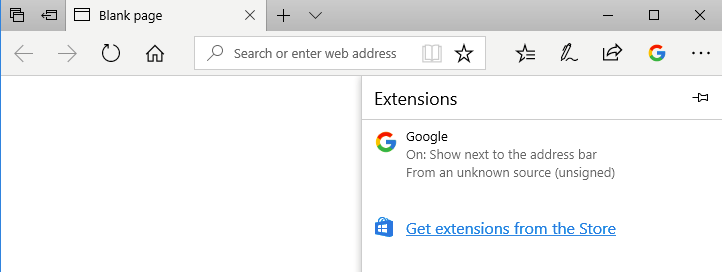
Furthermore, the NodeJS extension is responsible for executing the RAT and using taskkill/IM <filename> to kill the web browser that is currently opened. If the Java module and NodeJS identifies Edge and Chrome Browser to be opened, it kills the extension and creates a fake extension to load the malicious extension through this process.
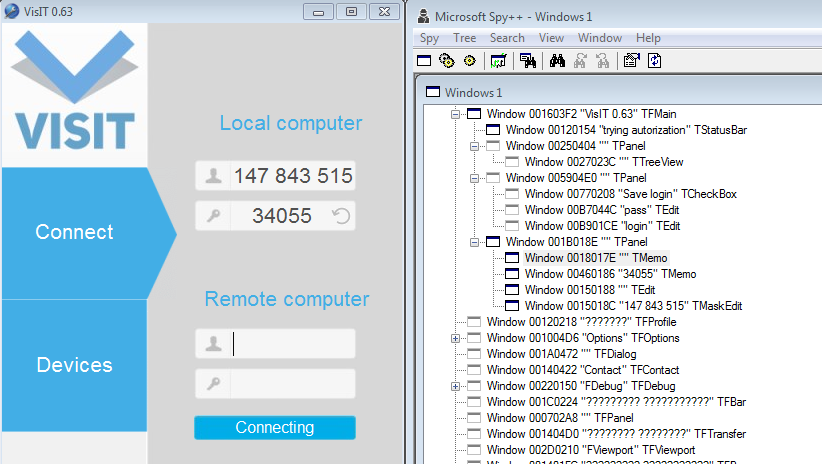
It then executes a revisit 0.63 application. It is an authentic and signed remote access tool. The stolen files are uploaded to the C&C server from the remote access tool after which the attackers can view the device ID and password. Afterward, they can connect to the device remotely and obtain full control of the machine. All the security checks are disabled and the malicious extension is loaded in both Edge and Chrome.
“This compatibility was a feature introduced by Microsoft last year to help developers port their Chrome extensions to Edge. Selenium is also used to load the extension into Edge,” researchers noted.
The malicious extension keeps on collecting the information about the opened webpage and URLs and sends it to the C&C server while performs a variety of other functions including clicking buttons, typing any value from within the webpage and selecting items from a drop-down list.
Both Microsoft and Google have been informed about the findings and Trend Micro is collaborating with the companies to ensure that the malicious extension doesn’t hinder security of the browsers. Businesses and users are urged to secure the email gateway to prevent the threat such as the Trend Micro Hosted Email Security.
More: Over 20 million Chrome users have installed fake malicious Ad Blockers
The exploitation of authentic RATs and hijacking their configuration isn’t the first of its kind incident since it has already been observed in campaigns where TeamViewer was abused by TeamSpy malware. But still, the new malware is a potent threat as it can abuse genuine APIs and open-source tools like Microsoft WebDriver and Chrome WebDriver.
Image credit: Depositphotos