Researchers urge for improving bio-cybersecurity as threat actors can use malware to target Synthetic DNA Orders to modify DNA strings sequence.
A group of academic researchers from the Ben-Gurion University of the Negev and Israel’s Interdisciplinary Center Herzliya identified a new kind of cyberattack that allows attackers to target the security gaps in the DNA procurement process.
The article titled “Increased cyber-biosecurity for DNA synthesis” was published in Nature Biotechnology. Researchers write that threat actors can launch an end-to-end cyber-biological attack to target DNA researchers.
According to the report, this can allow attackers to deploy malware, trick biologists into creating dangerous toxins or pathogens, and alter synthetic DNA orders.
See: Researchers Encode Physical DNA with Malware To infect Computers
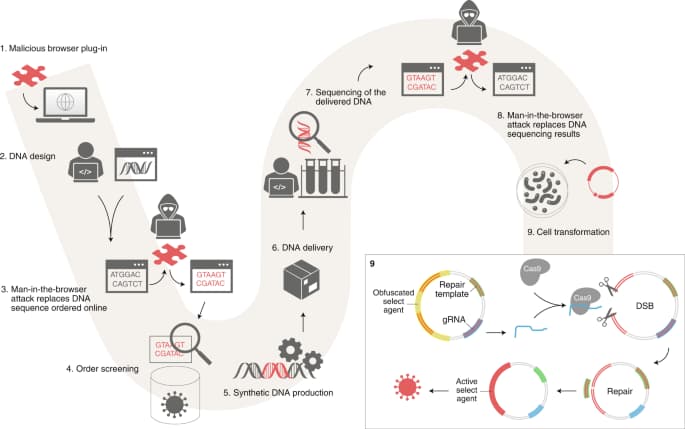
Previously it was assumed that an attacker must have physical access to a dangerous substance to produce and deliver it. However, Ben-Gurion researchers claim that by infecting a bioengineer’s computer with malware, it is possible to replace a short sub-string of the DNA, enabling them to mistakenly and unintentionally generate a toxin-producing sequence.
According to the BGU Complex Networks Analysis Lab head, Dr. Rumi Puzis,
“Most synthetic gene providers screen DNA orders which is currently the most effective line of defense against such attacks.”
“However, outside the state, bioterrorists can buy dangerous DNA, from companies that do not screen the orders. Unfortunately, the screening guidelines have not been adapted to reflect recent developments in synthetic biology and cyberwarfare.”
Puzis revealed a weakness in DNA providers’ guidelines from the U.S. Department of Health and Human Services (HHS). This weakness allows the circumvention of screening protocols using a generic obfuscation process. This process makes it difficult for screening software to identify toxin-generating DNA.
The researchers revealed that using the same technique, they identified that out of 50, 16 obfuscated DNA samples couldn’t be detected when screened as per the HHS’ Best-Match guidelines.
They also discovered that the automation and accessibility of the synthetic gene engineering workflow, when combined with inadequate cybersecurity, allows the malware to impact the lab’s biological processes. The loop will be closed after writing an exploit into a DNA molecule.
See: Malware can extract data from air-gapped PC through power supply
Researchers have shed light on a significant new threat utilizing malicious code to modify biological processes through the DNA injection attack. They demonstrated weaknesses at three bioengineering workflow stages- software, biosecurity screening, and biological protocols. This shows there is a need to apply cybersecurity measures in the context of gene coding and biosecurity.
“To address these threats, we propose an improved screening algorithm that takes into account in vivo gene editing. We hope this paper sets the stage for robust, adversary resilient DNA sequence screening and cybersecurity-hardened synthetic gene production services when biosecurity screening will be enforced by local regulations worldwide,” Puzis explained.
Did you enjoy reading this article? Don’t forget to like our page on Facebook and follow us on Twitter!
