One of the most secure system arrangements today consists of air-gapped PCs. The reason being their total disconnection from the internet. However, there are times when they too can be breached in various ways, a few involving the use of the computer’s speakers through sound waves.
Such exploits have prompted cybersecurity experts to even remove audio equipment from air-gapped computers essentially making them audio-gapped. In February this year, it was reported that hackers can steal data from air-gapped PC using screen brightness and now the same can be done through their power supply.
See: 8 Technologies That Can Hack Into Your Offline Computer & Phone
Mordechai Guri, a cybersecurity researcher from the Israeli Ben Gurion of the Negev University has conducted an experiment that shows how power supply units(PSUs) can be exploited to extract information from both an air-gapped & audio-gapped computer.
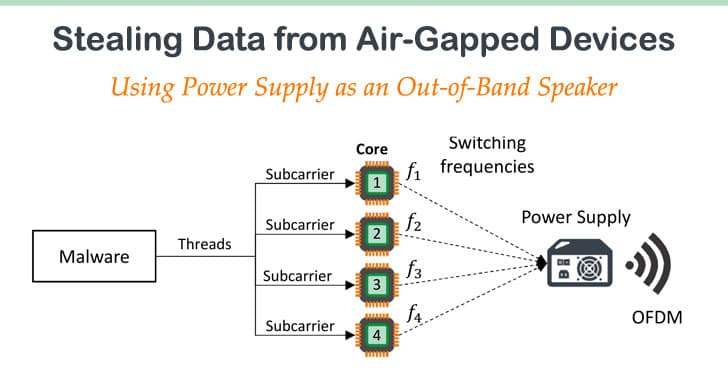
Termed as POWER-SUPPLaY; the malware exploits the PSU using it as an “out-of-band, secondary speaker with limited capabilities”.
The data that can be extracted includes different files & information of the user’s keystrokes transmittable up to 1 meters away along with passwords and encryption keys that the attacker could receive with a device that is five meters away from such as a smartphone as shown in the picture below (B).
Further, different types of computers can be exploited in this way including PC workstations, servers, embedded systems, and IoT devices making a whole range of devices vulnerable.
Elaborating on the specifics, Mordechai stated in their study that,
The malicious code manipulates the internal \textit{switching frequency} of the power supply and hence controls the sound waveforms generated from its capacitors and transformers. Our technique enables producing audio tones in a frequency band of 0-24khz and playing audio streams (e.g., WAV) from a computer power supply without the need for audio hardware or speakers.
An alarming thing perhaps is that no elevated privileges are needed to conduct the attack nor does the attacker need to physically access the hardware.
 Nonetheless, the maximum 6 meters distance requirement can become a serious limitation since it may call for the attacker to be near the system, thereby requiring some sort of social engineering and not operating truly in the “remote” sense.
Nonetheless, the maximum 6 meters distance requirement can become a serious limitation since it may call for the attacker to be near the system, thereby requiring some sort of social engineering and not operating truly in the “remote” sense.
Moreover, this becomes even more complicated when you think about where such air-gapped computers are used, primarily in highly secure environments such as government and corporate offices.
However, the research does not deal with the question of how the malware will be implemented in the first place on such a secure computer ironically leaving further gaps.
As for measures that can be taken by those who use such computers, some of them include Zoning in which electronic devices can be prohibited in areas containing air-gapped computers.
See: Sonic & Ultra signals can be used to crash Windows, Linux & hard drives
This, though, has the disadvantage of the obvious cost of the space needed. A host intrusion detection system may also be used which can monitor the running processes to observe any anomalies. This too has drawbacks such as false alarms being rung due to some processes naturally using CPU intensive calculations which would also come across as suspicious despite being entirely legitimate.
Watch the demonstration below:
To conclude, you may want to check out other instances of such attacks that have been conducted before to get a greater perspective on using air-gapped computers securely. Moreover, it would be wise to hire an expert to handle such a network’s security instead of trying to wing it.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.

