SafeBreach Labs’ researchers have successfully exploited MS Azure Automation Service to develop the first Free and Undetectable Cryptocurrency miner.
Cryptomining can cause harm if someone unauthorized does it on a regular person’s device. SafeBreach Labs found that researchers can use trustworthy, widely-used software to mine cryptocurrency without using many resources or incurring costs.
In a report shared with Hackread.com ahead of publication on Wednesday, SafeBreach researchers demonstrated this by creating the first completely undetectable cryptominer that operates freely using Microsoft Azure’s Automation service. This service is specifically made to automate cloud-management tasks, eliminating the need for building or maintaining infrastructure. Users only need to provide the scripts for execution.
In a blog post by Ariel Gamrian, three methods for running a cryptocurrency miner on Microsoft Azure servers without detection or charges were discovered. SafeBreach Labs’ researchers referred to this as the ultimate cryptominer.
They found that the Azure automation service allows the uploading of custom Python packages, which are then utilized within the runbook scripts. Whenever a package is uploaded, the service silently installs it in the background to ensure successful installation and prevent runbook execution problems. The researchers from SafeBreach Labs exploited this behaviour to develop the cryptominer successfully.
“We knew that code could not be directly executed on a .whl file installation, but we could assume what command was used in the background for installation. We assumed the .whl file would be installed by the pip executable already installed in the Automation Account using the command “pip install “pip install <whl_file>,” explained Gamrian.
“If our assumptions were correct, we could create a malicious package named “pip” and upload it to the Automation Account. The upload flow would replace the current pip in the Automation account.”
Once the custom pip was stored in the Automation account, the service automatically employed it whenever a package was uploaded. Leveraging this flow, the researchers managed to execute code. They ran this in a temporary sandboxed environment, obtaining an access token that represented the Automation Account’s assigned identity. This token allowed them to make requests on behalf of that identity, almost entirely obscuring any trace back to them.
Additionally, researchers found that they could achieve code execution by utilizing the Powershell module upload flow. This involved creating a Powershell module file containing the desired code for upload. While exploring the pricing, they discovered that the feature’s pricing details were not documented.
To determine the cost, they had to manually identify the code runtime and the associated flow cost. To test this, they initiated 55 import flows simultaneously, which theoretically accounted for approximately 10,000 minutes of runtime considering the three-hour import flow limitation.
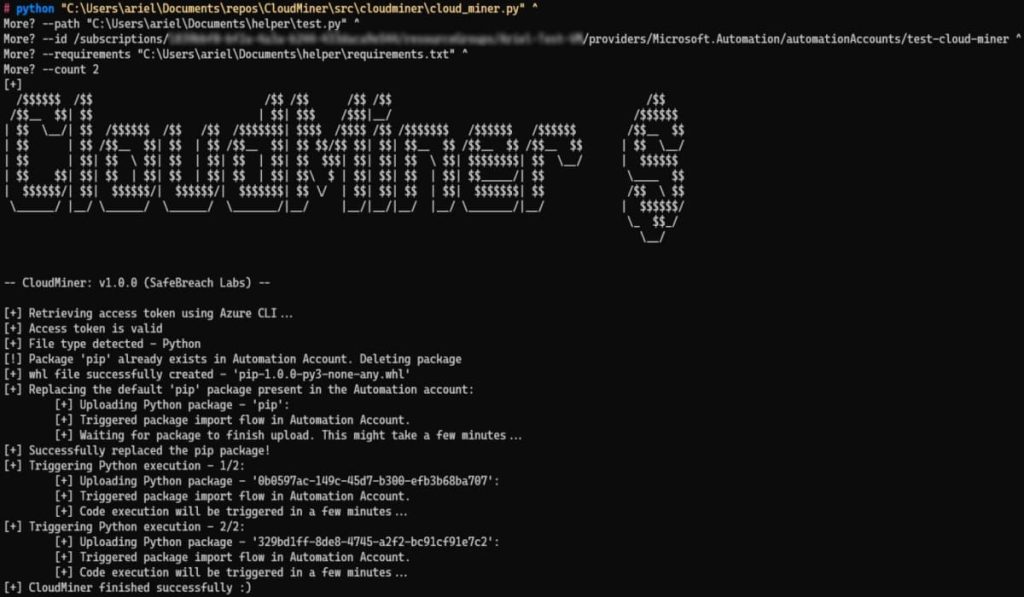
After a month, they checked and found they were not charged anything, confirming that their developed cryptominer incurred no charges and was maintenance-free. Subsequently, they developed a tool named CloudMiner, enabling anyone to execute code for free on Azure using the same technique. Users only need to provide the Python or Powershell script they wish to execute and grant access to their Automation Account, and the tool will manage the rest.
This research could significantly impact not only crypto mining but also other domains requiring code execution on Azure. Users can obtain cryptocurrency through various means, such as online exchanges, as payment, or by mining virtually.
Mining is a favoured method for earning crypto, involving a network of computers that verify and secure blockchains and digital ledgers recording crypto transactions. Miners are rewarded with new coins within this self-sustaining cycle, making it a preferred avenue for scammers.
The researchers reported their findings to the Microsoft Security Response Center, but no Common Vulnerabilities and Exposures (CVEs) were issued. However, the software company acknowledged the issue in their Security Researcher Acknowledgements for Microsoft Online Services. Subsequently, they addressed and resolved the Python 3.10 free runtime issue.
RELATED ARTICLES
- Mirai botnet exploiting Azure OMIGOD vulnerabilities
- Sensitive source codes exposed in Microsoft Azure Blob account leak
- Researchers accessed primary keys of Azure’s Cosmos DB customers
- SolarWinds hackers accessed source code of Azure, Exchange, Intune
- 240 top Microsoft Azure-hosted subdomains hacked to spread malware
- CISA’s Sparrow.ps1 tool detects malicious activity on Azure, Microsoft 365