Microsoft Threat Intelligence, partnered with cybersecurity firm Arkose’s ACTIR, conducted a large-scale operation against online fraudulent login markets, successfully taking down Hotmailbox.me.
Microsoft has successfully dismantled a black market for fraudulent login credentials. This action followed an investigation aimed at disrupting the fake Microsoft account network known as Storm-1152, extensively utilized by cybercriminals.
Researchers believe that cracking down on fraudulent accounts is crucial because cybercrime relies on fraudulent accounts as these act as digital keys for mass phishing, spam campaigns, and ransomware attacks.
The use of fraudulent and stolen login credentials by cybercriminals for large-scale data breaches is an undeniable reality. The recent attack on OAuth app users, as revealed by Microsoft just yesterday, serves as a small example amidst more significant incidents.
For your information, Storm-1152 is the world’s leading seller and creator of fraudulent Microsoft accounts. The platform has been exposed through a collaborative effort between Microsoft Threat Intelligence and cybersecurity firm Arkose’s Cyber Threat Intelligence Research unit (ACTIR).
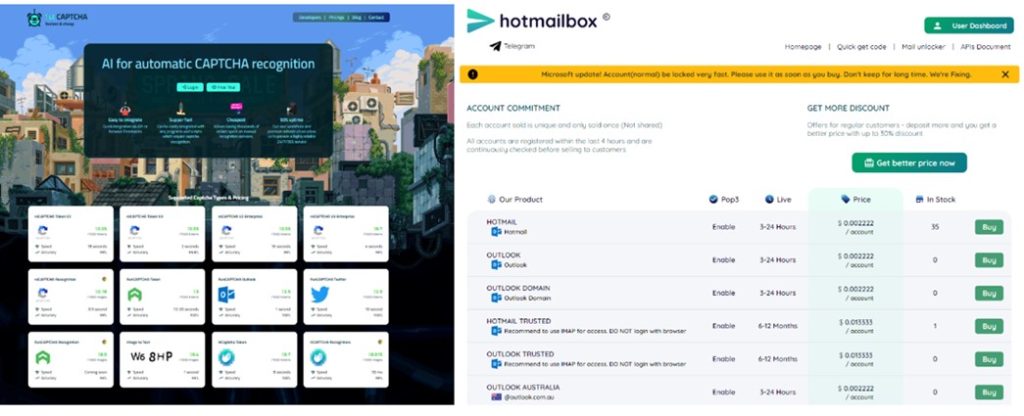
According to Microsoft’s report, Storm-1152 operates a network of illicit websites and social media pages, selling fake Microsoft accounts and identity verification bypass tools. So far, the operators have generated around 750 million fraudulent accounts, leaving a trail of destruction.
Storm-1152, a notorious group in the cybercrime-as-a-service (CaaS) industry, specializes in producing and selling millions of fraudulent Microsoft accounts. The group is impactful because it lowers the barrier to entry, enabling a wider range of actors to engage in cybercrime. This efficiency boosts the scope and frequency of cyberattacks, impacting countless individuals and businesses.
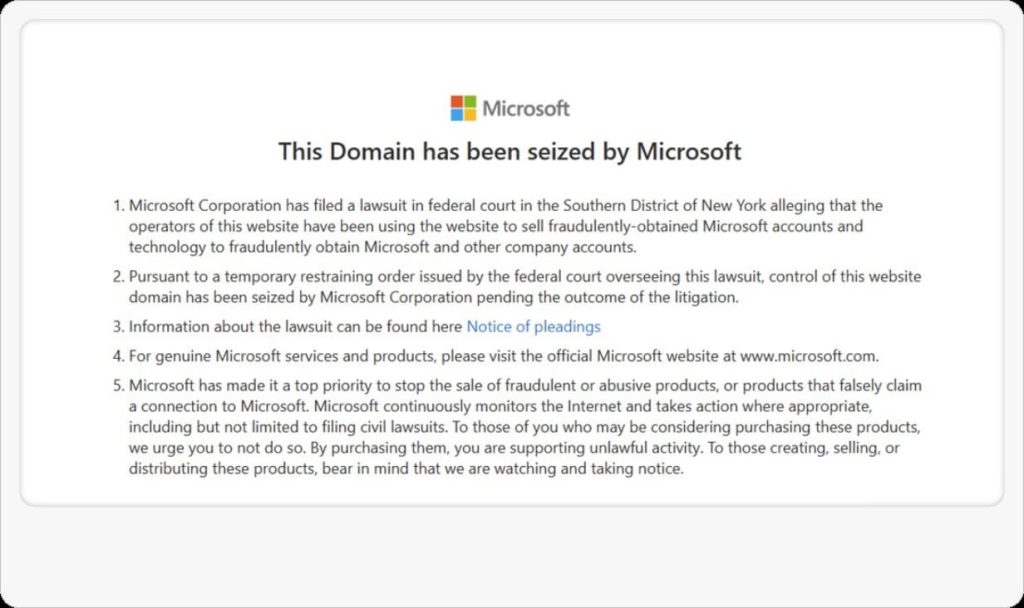
Microsoft aims to dismantle Storm-1152’s infrastructure and disrupt the entire ecosystem that enables their activities, aiming to create a safer online environment for everyone. Microsoft has obtained a court order from the Southern District of New York to seize U.S.-based infrastructure and offline websites used by Storm-1152 to harm Microsoft customers.
The case focuses on fraudulent Microsoft accounts and services sold to bypass security measures on other technology platforms. Microsoft’s Digital Crimes Unit disrupted Hotmailbox.me, 1stCAPTCHA, AnyCAPTCHA, and NoneCAPTCHA, which facilitate CAPTCHA solve service sales and identity verification bypass tools for other platforms.
Researchers have also uncovered links between Storm-1152’s network and various cybercrime groups, including Octo Tempest, Storm-0252, and Storm-0455.
Nevertheless, this was a multi-phased operation launched to expose the people operating the malicious servers. Researchers used various investigative techniques, including network traffic analysis, telemetry data, and reverse engineering, to identify the source of the storm.
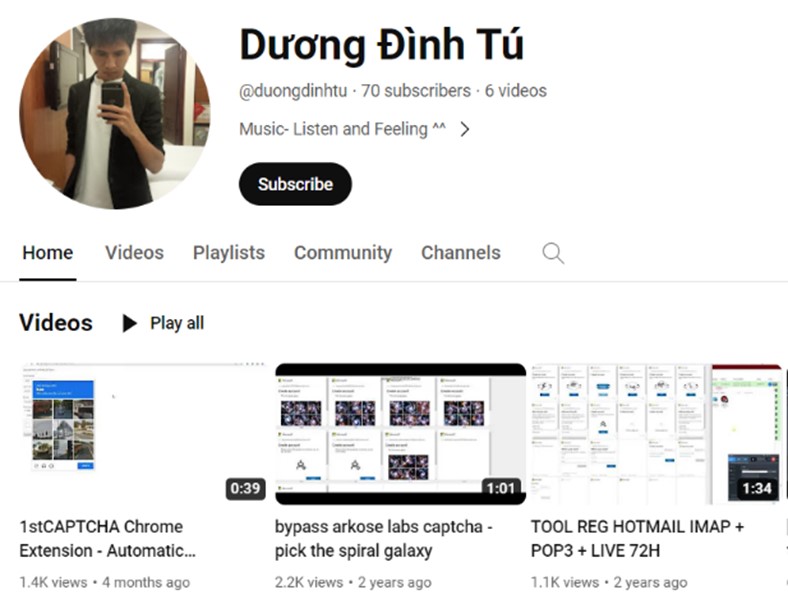
They identified three individuals, Duong Dinh Tu, Linh Van Nguyễn, and Tai Van Nguyen, as the masterminds behind the Storm-1152 machine. They hosted illegitimate platforms, authored the code, published tutorials, and offered live chat support.
Exposing the individuals behind Storm-1152 was crucial in dismantling this criminal network and holding accountable those who actively enabled online crime. Additionally, this coordinated takedown sends a clear message to Storm-1152 and others following their path: they are being watched and soon will be caught.
RELATED ARTICLES
- Storm-1283 Sent 927K Phishing Emails with Malicious OAuth Apps
- Chinese Group Storm-0558 Hacked European Govt Emails, Microsoft
- Storm-0324 Exploits MS Teams Chats to Facilitate Ransomware Attacks
- Microsoft and Fortra to Take Down Malicious Cobalt Strike Infrastructure
- EvilProxy Phishing Kit Targets Microsoft Users via Indeed.com Vulnerability
- Scammers Use Fake Ledger App on Microsoft Store to Steal $800K in Crypto