Microsoft Warns of OAuth-Fueled Cyber Attacks Exploiting Cloud Infrastructure for Phishing and Cryptocurrency Mining.
Microsoft has discovered a sophisticated cybercrime scheme by Storm-1283 threat actor who infiltrated a user account to hijack digital keys and mine cryptocurrency within the Microsoft cloud platform Azure.
According to the Microsoft Threat Intelligence unit’s research, the attacker utilized compromised user accounts to establish inbox rules with suspicious names, redirecting emails to the junk folder and marking them as read. Additionally, the malicious OAuth applications created by the actor were responsible for sending over 927,000 phishing emails.
In this campaign, hackers exploited the OAuth feature, which permits apps to access user data with proper authorization. They pilfer digital keys, enabling them to cause havoc through phishing or brute force—cracking weak passwords or deceiving users into divulging their login credentials. Once inside, they create or modify OAuth applications with elevated access, effectively transforming them into ‘master keys’ for online resources.
These stolen keys are used for cryptocurrency mining, granting hackers lasting access even if passwords are changed. Email and spam sprees are also common, as the master key grants hackers lasting access.
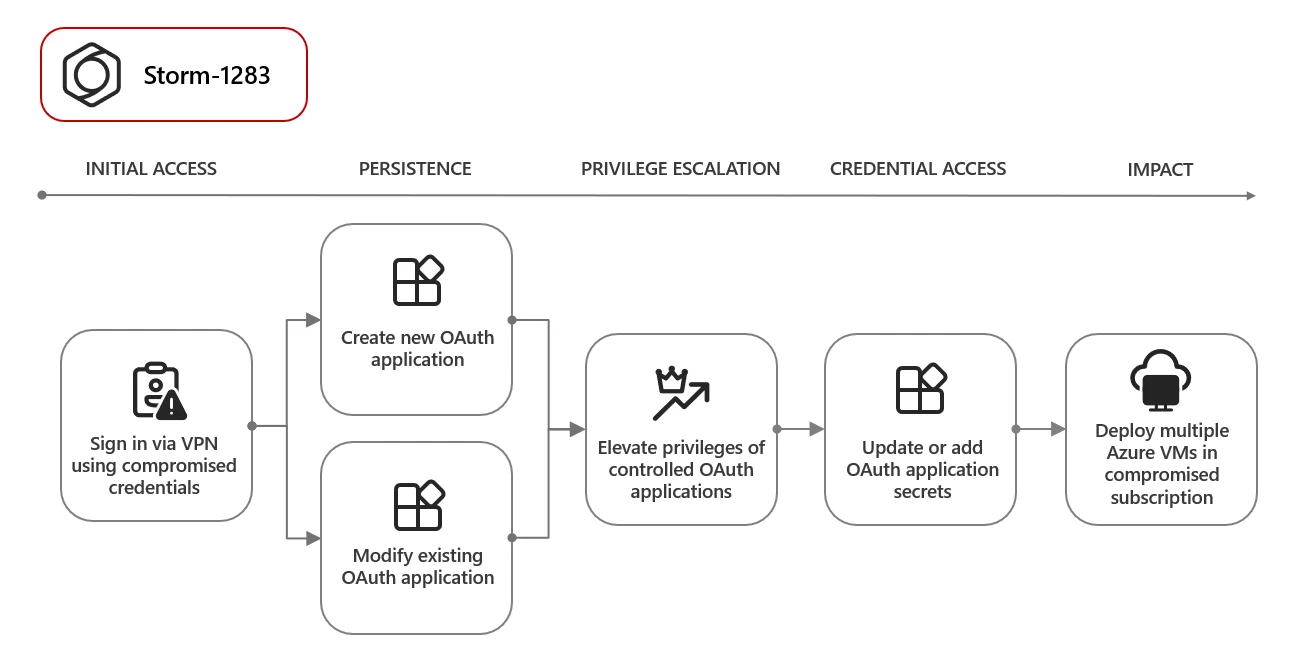
Storm-1283 breached a user account, gaining access to a virtual private network and tenant domain within Microsoft Entra ID. They created a new “OAuth application” using stolen credentials, allowing them to control resources within the compromised account.
They double-dipped existing OAuth applications, adding secret credentials to these keys. With the keys, Storm-1283 deployed virtual machines (VMs) within the compromised Azure subscription, generating cryptocurrency for their illicit gains. They re-entered the cloud, deploying more VMs to maximize their operation.
The targeted organizations suffered financial losses ranging from $10,000 to $1.5 million. Microsoft’s security researchers discovered the suspicious activity and exposed the hacker’s tactics, including masking VMs by mimicking the domain name.
Microsoft analysts also detected a threat actor who compromised user accounts and created OAuth applications to maintain persistence and launch email phishing activity. The actor used an adversary-in-the-middle (AiTM) phishing kit to send a significant number of emails with varying subject lines and URLs to target user accounts in multiple organizations.
Microsoft worked with the Microsoft Entra team to block the OAuth applications involved in the attack and advised further actions.
The company also observed large-scale spamming activity through OAuth applications by Storm-1286. The actor launched password-spraying attacks to compromise user accounts, most of which did not have multifactor authentication (MFA).
The user agent BAV2ROPC was observed in sign-in activities related to the compromised accounts, indicating the use of legacy authentication protocols such as IMAP and SMTP that do not support MFA.
Microsoft Threat Intelligence has limited the actor’s activity by taking down all malicious OAuth applications related to this campaign, which ran from July to November 2023.
DoControl‘s Vice President of Solution Consulting, Tim Davis, also commented on this campaign with Hackread.com, urging for making the cloud platform secure.
“These types of attacks underscore the need for visibility into what both systems and users are doing on any cloud platform. Both limiting of permissions (the least privilege or zero trust model) and robust anomaly detection are critical to protecting resources that are located in the cloud.”
RELATED ARTICLES
- Chinese Group Storm-0558 Hacked European Govt Emails, Microsoft
- Storm-0324 Exploits MS Teams Chats to Facilitate Ransomware Attacks
- Microsoft Outlook Vulnerability Exploited by Russian Forest Blizzard Group
- EvilProxy Phishing Kit Targets Microsoft Users via Indeed.com Vulnerability
- Scammers Use Fake Ledger App on Microsoft Store to Steal $800K in Crypto