Microsoft Releases Patch for Dangerous .NET Vulnerability in Latest Security Updates.
Microsoft has finally patched a vulnerability in Microsoft Windows that was used by law enforcement agencies to target Windows users in Russia. The patch, (OS Build 15063.608), was part of Microsoft’s monthly “Patch Tuesday” series containing security updates for 85 different flaws including the serious .NET framework flaw that allowed hacking of targeted computers through malicious MS Office attachments.
The update was released on Tuesday and offers security updates for all versions of Microsoft Windows as well as other products. However, the most important vulnerability that it patches is the .NET framework flaw that affected Windows 10 systems.
Regarding the vulnerability, Microsoft wrote on its advisory page that:
“A remote code execution vulnerability exists when Microsoft .NET Framework processes untrusted input. An attacker who successfully exploited this vulnerability in software using the .NET framework could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.”
The vulnerability has been codenamed CVE-2017-8759. It affected the .NET programming framework and allowed remote code execution. According to FireEye security firm which discovered this vulnerability, the flaw was exploited through a malicious MS Office document uploaded in rich text format (RTF) while the exploitation occurred in July 2017. This flaw attempted to install FinFisher or FinSpy spyware developed by the UK based Gamma Group specifically for law enforcement agencies. However, FireEye did not point out which agency deployed FinFisher/FinSpy spyware.
FireEye also noted that the zero-day vulnerability that allowed installation of malware on Windows systems is the second flaw that has been identified in Windows OS this year. As per FireEye researcher’s analysis, apart from selling the spyware to law enforcement, financially motivated cyber criminals also benefitted from it.
“These exposures demonstrate the significant resources available to ‘lawful intercept’ companies and their customers. Furthermore, Finspy has been sold to multiple clients, suggesting the vulnerability was being used against other targets,” FireEye said.
FireEye has described the flaw as a SOAP WSDL parser code injection vulnerability. That’s because it allowed malware to inject arbitrary code in the definition contents of SOAP WSDL while the attachments responsible for inserting the malware were identified as a common attack vector. The .NET flaw scrubbed malicious input from data that was fed to the Web Services Description Language (WSDL).
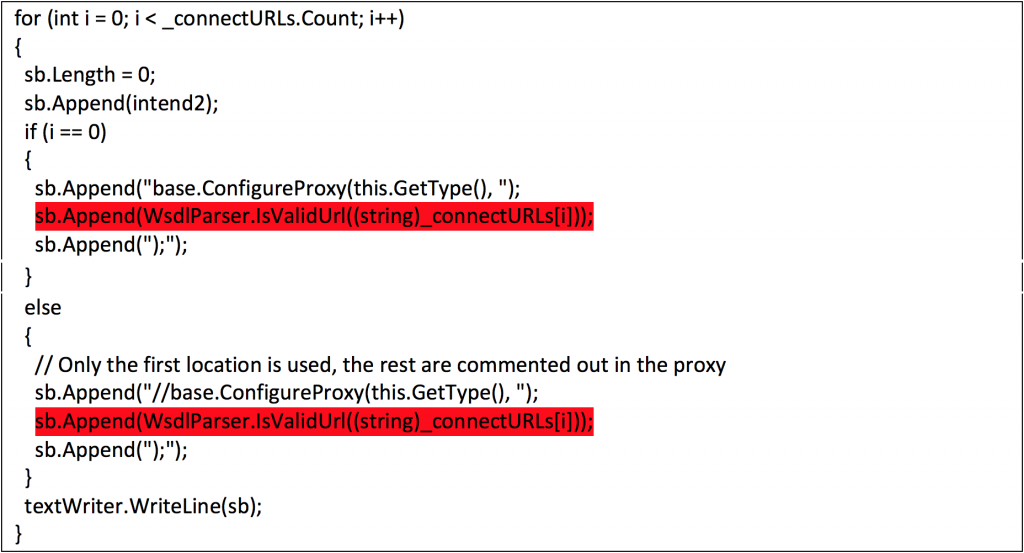
The attacker compelled Windows user to open the email containing the malicious document or application. Once injected, the code created a process for retrieving an HTA script, which in turn deleted the source code and library to download and execute “left.jpg” file. Don’t be confused by this file’s classification as a JPG image since it was everything else than an image file. It was an executable document and instantly installed FinSpy spyware, a malware that used heavily obscured coding as well as built-in virtual machine to hide its functions.
Microsoft believes that the NEODYMIUM group carried out the attack exploiting the .NET framework flaw because the same group previously exploited a similar zero-day vulnerability using spear-phishing attachments to install FinFisher spyware.
Patch Tuesday includes patches for some important vulnerabilities along with the serious .NET framework flaw including Remote Code Execution patches for MS Office, Internet Explorer 11 and Edge and patch for a BlueBorne BlueTooth flaw that allowed attackers to hack Windows PCs, Android and Linux devices.
