mSpy, the notorious software-as-a-device product which so far enabled two million plus people spy on their spouses and kids, is believed to be a victim of serious hacking.
Last week it was discovered that massive data has been stolen from the company’s servers and posted on the Dark Web, revealing numerous emails, text messages, payment and location data to an uncertain number of mSpy “users.”
mSpy is not entertaining requests and queries for five days now furthermore, KrebsOnSecurity cracked the hacking source but pity it was shared from a link to a Webpage only accessible via TOR, a technology that enables users to keep their actual internet addresses hidden and host Websites very difficult to reach or take down.
A real set back that leaves millions of users’ privacy at risk:
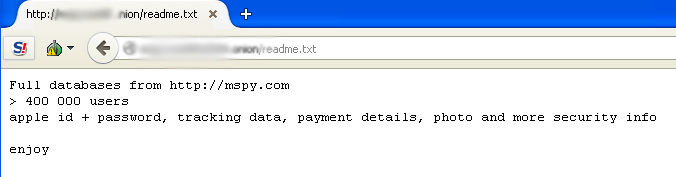
The Tor-based site hosts several hundred gigabytes worth of data chunks, taken from mobile devices running mSpy’s products, inclusive of about four million events registered by the software. The hackers who have claimed this invasion also unveil that this enormous data theft contains confidential information on more than 400,000 users, including Apple IDs and passwords, tracking data, and payment details on some 145,000 successful transactions.
Although, the precise number of mSpy victims couldn’t be confirmed, but it is evident that insane amounts of sensitive data has been compromised which includes: photos, corporate email threads, calendar data and extremely private conversations. The huge data dump also exposes thousands of support request emails from people all over the world that paid between $8.33 to as much as $799 as various subscription charges to mSpy’s surveillance.
mSpy Unfolded:
It’s unclear still as to where mSpy is actually based; according to the company’s Web site it has offices in the United States, Germany and the United Kingdom, although there is no physical address given, the registration records show that the company is tied to a now-defunct firm called MTechnology LTD out of the United Kingdom.
Documents related to the Companies House, at the UK show that the two founding members of the company are self-proclaimed programmers Aleksey Fedorchuk and Pavel Daletski, and that Daletski is a British citizen, and Mr. Fedorchuk is from Russia. Neither of the men could be accessed for comment.
Court documents (PDF) attained from the U.S. District Court in Jacksonville, Fla. concerning a trademark clash referring to mSpy and Daletski state that mSpy has a U.S.-based address of 800 West El Camino Real, in Mountain View, Calif. According to these documents Daletski is a director at a firm based in the Seychelles called Bitex Group LTD. It is in fact amusing that the lawsuit was brought to light by Retina-X Studios, an mSpy competitor based in Jacksonville, Fla. that creates a product called MobileSpy.
U.S. regulators and law enforcers have grown weary of companies that offer mobile spyware services similar to mSpy. In September 2014, U.S. authorities arrested a 31-year-old Hammad Akbar, the CEO of a Lahore-based company that’s responsible for a spyware app called StealthGenie. The FBI noted that while the company advertised StealthGenie’s use for “monitoring employees and loved ones such as children,” the primary target audience were cheating spouses. Akbar was later charged with selling and advertising wiretapping equipment.
Spyware HUNTERS:
U.S. Attorney Dana Boente expressed his disdain in a press release for advertising and selling of spyware technology and called it a criminal offense and warned that such behavior will be dealt with an iron hand by their office. Akbar pleaded guilty to the charges in November 2014, and according to the justice department, that made him the first ever person to have admitted to criminal activity in advertising and selling spyware that invades a victims privacy in any way or form. As opposed to Akbar’s StealthGenie and some other mobile spyware products, mSpy advertises that its product works even on non-jailbroken iPhones, enabling users to log the device holder’s contacts, call logs, text messages, browser history, events and notes.
According to mSpy FAQ if users purchase mSpy minus Jailbreak, and have the target mobile user’s iCloud credentials, then physical access to the device will not be needed, leave a few instances. Nevertheless, on purchase of mSpy for jailbroken iOS phone or tablet, 5-15 minutes of physical access to the device will be required for a successful installation.
A public relations source from mSpy to KrebsOnSecurity in March 2015 stated that approximately 40 percent of the company’s users are parents willing to keeping tabs on their kids. The plan backfired badly because now they’ve unintentionally exposed their kids’ credentials to bullies, hunters and evil doers.
Note:
Readers are asking us to provide leaked data link. I am sorry I won’t be sharing the link nor I will allow anyone to post the data here in comments. It’s users’ personal data and we should respect their privacy.
Krebs On Security