The malicious Monero mining campaign is spreading fast through ADB.miner to target Android devices.
The IT security researchers at a Chinese information security firm Netlab have revealed that the ADB.miner malware also called Android.CoinMine.15 is spreading at an excessively fast pace. Researchers have noted that its activity is at its peak at the moment with the number of infected devices getting doubled every passing day.
According to their blog post, a majority of these infected devices are smart TVs probably because these devices use ADB (Android Debug Bridge) for uninterrupted internet connections. However, smartphones, set-top boxes, media players, routers, tablets and receivers along with the Android-based single-board computer Raspberry Pi 3 are also potential targets since all of them use network debugging.
This Android Trojan performs Monero cryptocurrency mining and can easily infect other devices; it infects Android devices using an open port 5555 that is used by the ADB. It is distributed via the Droidbot.apk application with the files nohup, sss, and bot.dat, which are installed on an infected host through another infected device.
The sss file is executed using the nohup utility where the file serves as a daemon and extracts other Trojan components from bot.dat. These components include a JSON configuration file, a copy of the droidbot Trojan program and miner applications both for 32-bit and 64-bit operating systems. After being launched, droidbot produces a random IP address and attempts to create a connection with the port 5555 through creating an infinite loop, which infects the targeted device by exploiting the ADB debugger’s interface.
Additionally, a separate thread is created where a miner application is launched; this application is designed to mine Monero cryptocurrency. Through mining operation, the device’s performance is significantly reduced as it will get overheated and the battery will be drained rapidly.
It must be noted that the ADB debugger is originally disabled in a majority of Android devices but some vendors choose to enable it; it can also be enabled manually by a user and developers also use the debugging mode frequently. Around 8% of the devices have the debugging mode enabled; this means 8% of all the android devices are potentially at risk.
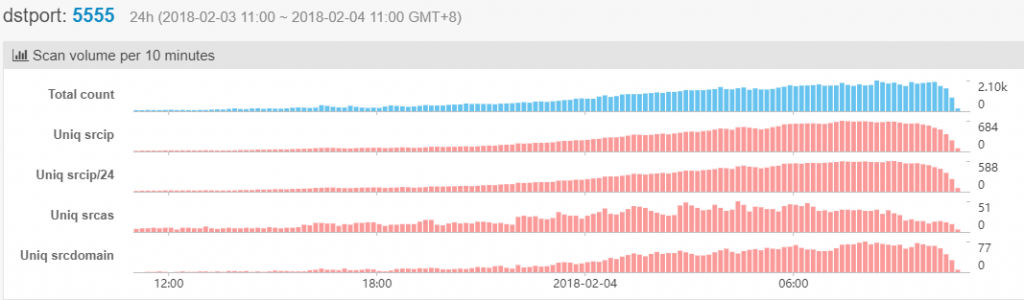
After getting infected, the compromised TV boxes and Android smartphones search networks for other devices having the Internet port 5555 open, which usually is closed but the ADB tool enables it to carry out a series of diagnostic tests. Netlab’s laboratory was scanned by 2,750 unique IPs in the initial 24 hours after the botnet was launched. This is why researchers believe that the malware is spreading at an alarmingly high rate.
“Overall, we think there is a new and active worm targeting Android systems’ ADB debug interface spreading, and this worm has probably infected more than 5,000 devices in just 24 hours. Those infected devices are actively trying to spread malicious code,” wrote the researchers from Netlab.