Newly Identified Drive-by Monero Cryptomining Campaign Targeted Millions of Android Devices in Few Months.
Hackers usually rely upon infected or rather trojanized applications and redirect notices to carry out a certain kind of online scam called malvertising and nowadays they are increasingly relying on carrying out cryptomining through these very techniques.
In their campaign, Android devices are being targeted quite frequently and in a majority of cases, the sole reason behind devices getting infected is that users ignore installing security apps and do not web filtering on their cell phones. That’s why hackers have easily managed to hijack probably millions of Android devices within a few months only for mining Monero coins in the newly discovered drive-by cryptomining campaign.
Malwarebytes identified this campaign in January 2018 but they believe that it started in November 2017. Researchers identified it while investigating another campaign called EITest in January. While inspecting different malvertising chains that led to tech support scams through a user-agent of Chrome or Internet Explorer browser on Windows, they noticed that while switching to Android device they got redirected to that cryptomining webpage.
In this new campaign, hackers managed to trick unsuspecting Android users into redirecting them to fake, malicious web pages that were designed to carry out in-browser cryptomining through exploiting the processor in order to generate Monero coins (XMR). The campaign has affected millions of mobile users.
Drive-by mining can be understood as an automated process of exploiting CPU’s power. It occurs silently and secretively without requiring the consent of the user and displays a CAPTCHA code ‘w3FaSO5R’ to the user through this message:
“Your device is showing suspicious surfing behavior. Please prove that you are human by solving the captcha.”
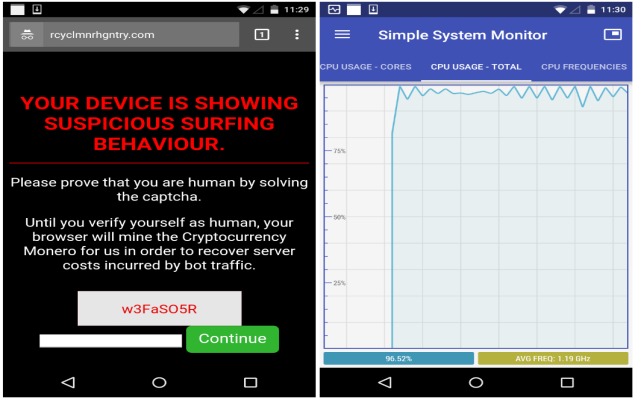
When the user enters this code and clicks on Continue, the device will start mining for Monero using 100% CPU power while some users are redirected to Google’s home page. Various similar domains are using this CAPTCHA code but still, they have different Coinhive site keys, the first key was registered in late November 2017 while new domains kept on being created afterward but the template remained the same.
Malwarebytes researchers have so far identified five such domains and two of them had more than 30 million visits per month and the cumulative traffic from these domains totaled around 800,000 visits per day. According to Jerome Segura, Malwarebytes’ lead malware intelligence analyst:
“We believe there are several more domains than just the few that we caught, but even this small subset is enough to give us an idea of the scope of this campaign. It is difficult to determine how much Monero currency this operation is currently yielding without knowing how many other domains (and therefore total traffic) are out there. Because of the low hash rate and the limited time spent mining, we estimate this scheme is probably only netting a few thousand dollars each month.”
This code has been hardcoded in the webpage’s source code and it is quite odd that it is able to effectively verify traffic between a bot and a human and redirecting to Google’s page is also another odd occurrence. While users are busy solving the code, the site starts running an extensive and exhaustive cryptojacking script that uses the CPU power to its fullest and mines Monero. This process is so exhausting for the device that it can render the mobile useless if continued for a longer duration.
Researchers believe that this campaign might be not be targeted against bots but to low-quality traffic and instead of serving regular ads the hijackers chose to use browser-based Monero miner to make more profit.
“Until the code (w3FaSO5R) is entered and you press the Continue button, your phone or tablet will be mining Monero at full speed, maxing out the device’s processor,” wrote Segura.
It was just a couple of days ago when it was reported that hackers had hijacked thousands of UK and US government websites for the sole purpose of generating Monero cryptocurrency. Moreover, popular websites like YouTube, Bla
